October was European Cyber Security Month (ECSM) and International Cybersecurity Awareness month with the latter’s theme being “Secure Our World”. It’s safe to say that instilling best practices for online safety to individuals, businesses and critical infrastructure is mission critical in 2024. At Greenbone, in addition to our Enterprise vulnerability management products, we are happy to make enterprise grade IT security tools more accessible via our free Community Edition, Community Portal and vibrant Community Forum to discuss development, features and get support.

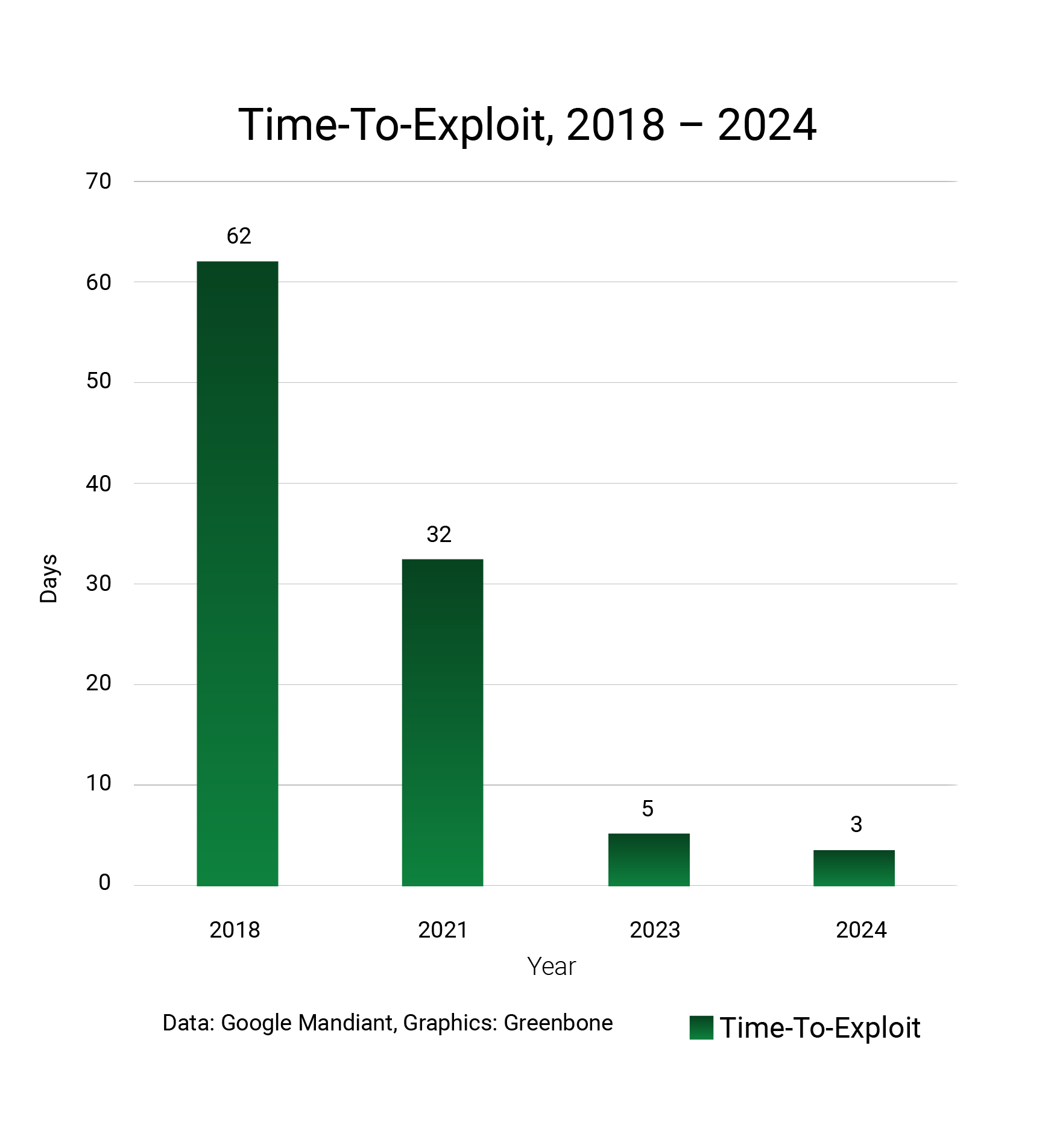
Our core message to cybersecurity decision makers is clear: To patch or not to patch isn’t a question. How to identify vulnerabilities and misconfigurations before an attacker can exploit them is. Being proactive is imperative; once identified, vulnerabilities must be prioritized and fixed. While alerts to active exploitation can support prioritization, waiting to act is unacceptable in high risk scenarios. Key performance indicators can help security teams and executive decision makers track progress quantitatively and highlight areas that need improvement.
In this month’s Threat Tracking blog post, we will review this year’s ransomware landscape including the root causes of ransomware attacks and replay some of the top cyber threats that emerged in October 2024.
International Efforts to Combat Ransomware Continue
The International Counter Ransomware Initiative (CRI), consisting of 68 countries and organizations (notably lacking Russia and China), convened in Washington, D.C., to improve ransomware resilience globally. The CRI aims to reduce global ransomware payments, improve incident reporting frameworks, strengthen partnerships with the cyber insurance industry to lessen the impact of ransomware incidents, and enhance resilience by establishing standards and best practices for both preventing and recovering from ransomware attacks.
Microsoft’s Digital Defense Report 2024 found the rate of attacks has increased so far in 2024, yet fewer breaches are reaching the encryption phase. The result is fewer victims paying ransom overall. Findings from Coveware, Kaseya, and the Chainanalysis blockchain monitoring firm also affirm lower rates of payout. Still, ransomware gangs are seeing record profits; more than 459 million US-Dollar were extorted during the first half of 2024. This year also saw a new single incident high; a 75 million US-Dollar extortion payout amid a trend towards “big game hunting” – targeting large firms rather than small and medium sized enterprises (SMEs).
What Is the Root Cause of Ransomware?
How are successful ransomware attacks succeeding in the first place? Root cause analyses can help: A 2024 Statista survey of organizations worldwide reports exploited software vulnerabilities are the leading root cause of successful ransomware attacks, implicated in 32% of successful attacks. The same survey ranked credential compromise the second-most common cause and malicious email (malspam and phishing attacks) third. Security experts from Symantec claim that exploitation of known vulnerabilities in public facing applications has become the primary initial access vector in ransomware attacks. Likewise, KnowBe4, a security awareness provider, ranked social engineering and unpatched software as the top root causes of ransomware.
These findings bring us back to our core message and highlight the importance of Greenbone’s industry leading core competency: helping defenders identify vulnerabilities lurking in their IT infrastructure so they can fix and close exploitable security gaps.
FortiJump: an Actively Exploited CVE in FortiManager
In late October 2024, Fortinet alerted its customers to a critical severity RCE vulnerability in FortiManager, the company’s flagship network security management solution. Dubbed “FortiJump” and tracked as CVE-2024-47575 (CVSS 9.8), the vulnerability is classified as “Missing Authentication for Critical Function” [CWE-306] in FortiManager’s fgfm daemon. Google’s Mandiant has retroactively searched logs and confirmed this vulnerability has been actively exploited since June 2024 and describes the situation as a mass exploitation scenario.
Another actively exploited vulnerability in Fortinet products, CVE-2024-23113 (CVSS 9.8) was also added to CISA’s KEV catalog during October. This time the culprit is an externally-controlled format string in FortiOS that could allow an attacker to execute unauthorized commands via specially crafted packets.
Greenbone is able to detect devices vulnerable to FortiJump, FortiOS devices susceptible to CVE-2024-23113 [1][2][3], and over 600 other flaws in Fortinet products.
Iranian Cyber Actors Serving Ransomware Threats
The FBI, CISA, NSA and other US and international security agencies issued a joint advisory warning of an ongoing Iranian-backed campaign targeting critical infrastructure networks particularly in healthcare, government, IT, engineering and energy sectors. Associated threat groups are attributed with ransomware attacks that primarily gain initial access by exploiting public facing services [T1190] such as VPNs. Other techniques used in the campaign include brute force attacks [T1110], password spraying [T1110.003], and MFA fatigue attacks.
The campaign is associated with exploitation of the following CVEs:
- CVE-2024-24919 (CVSS 8.6), an information disclosure in Check Point Security Gateway VPNs
- CVE-2024-21887 (CVSS 9.1), a command injection flaw in Ivanti Connect Secure and Ivanti Policy Secure
- CVE-2024-3400 (CVSS 10), a command injection flaw in Palo Alto Networks PAN-OS
- CVE-2022-1388 (CVSS 9.8), an authentication bypass vulnerability in F5 BIG-IP and CVE-2020-5902 (CVSS 9.8), a Remote Code Execution (RCE) flaw in F5 BIG-IP Traffic Management User Interface
- CVE-2020-1472 (CVSS 5.5), a privilege escalation vulnerability in Microsoft Netlogon Remote Protocol
- CVE-2023-3519 (CVSS 9.8), an unauthenticated RCE flaw and CVE-2019-19781 (CVSS 9.8), a directory traversal vulnerability in Citrix Application Delivery Controller and Gateway
- CVE-2019-11510 (CVSS 10), an unauthenticated file read and CVE-2019-11539 (CVSS 7.2), a Remote Command Execution flaw, both in Pulse Secure Pulse Connect Secure
Greenbone can detect all CVEs referenced in the campaign advisories, providing defenders with visibility and the opportunity to mitigate risk. Furthermore, while not tracked as a CVE, preventing brute force and password spraying attacks is cybersecurity 101. While many authentication services do not natively offer brute force protection, add-on security products can be configured to impose a lockout time after repeated login failures. Greenbone can attest compliance with CIS security controls for Microsoft RDP including those that prevent brute-force and password spraying login attacks.
Finally, according to the EU’s Cyber Resilience Act’s (CRA), Annex I, Part I (2)(d), products with digital elements must “ensure protection from unauthorized access by appropriate control mechanisms”, including systems for authentication, identity and access management, and should also report any instances of unauthorized access. This implies that going forward the EU will eventually require all products to have built-in brute force protection rather than relying on third-party rate limiting tools such as fail2ban for Linux.
Unencrypted Cookies in F5 BIG-IP LTM Actively Exploited
CISA has observed that cyber threat actors are exploiting unencrypted persistent cookies on F5 BIG-IP Local Traffic Manager (LTM) systems. Once stolen, the cookies are used to identify other internal network devices which can further allow passive detection of vulnerabilities within a network. Similar to most web-applications, BIG-IP passes an HTTP cookie between the client and server to track user sessions. The cookie, by default, is named BIGipServer<pool_name> and its value contains the encoded IP address and port of the destination server.
F5 BIG-IP is a network traffic management suite and LTM is the core module that provides load balancing and traffic distribution across servers. CISA advises organizations to ensure persistent cookies are encrypted. F5 offers guidance for setting up cookie encryption and a diagnostic tool, BIG-IP iHealth to detect unencrypted cookie persistence profiles.
While active exploitation increases the threat to organizations who have not remediated this weakness, the vulnerability has been known since early 2018. Greenbone has included detection for this weakness since January 2018, allowing users to identify and close the security gap presented by unencrypted cookies in F5 BIG-IP LTM since its disclosure.
New High Risk Vulnerabilities in Palo Alto Expedition
Several new high risk vulnerabilities have been disclosed in Palo Alto’s Expedition, a migration tool designed to streamline the transition from third-party security configurations to Palo Alto’s PAN-OS. While not observed in active campaigns yet, two of the nine total CVEs assigned to Palo Alto in October were rated with EPSS scores in the top 98th percentile. EPSS (Exploit Prediction Scoring System) is a machine learning prediction model that estimates the likelihood of a CVE being exploited in the wild within 30 days from the model prediction.
Here is a brief technical description of each CVE:
- CVE-2024-9463 (CVSS 7.5, EPSS 91.34%): An OS command injection vulnerability in Palo Alto’s Expedition allows an unauthenticated attacker to run arbitrary OS commands as root in Expedition, resulting in disclosure of usernames, cleartext passwords, device configurations and device API keys of PAN-OS firewalls.
- CVE-2024-9465 (CVSS 9.1, EPSS 73.86%): An SQL injection vulnerability in Palo Alto Networks Expedition allows an unauthenticated attacker to reveal sensitive database contents, such as password hashes, usernames, device configurations and device API keys. Once this information has been obtained, attackers can create and read arbitrary files on affected systems.
Four Critical CVEs in Mozilla Firefox: One Actively Exploited
As mentioned before on our Threat Tracking blog, browser security is critical for preventing initial access, especially for workstation devices. In October 2024, seven new critical severity and 19 other less critical vulnerabilities were disclosed in Mozilla Firefox < 131.0 and Thunderbird < 131.0.1. One of these, CVE-2024-9680, was observed being actively exploited against Tor network users and added to CISA’s known exploited catalog. Greenbone includes vulnerability tests to identify all affected Mozilla products.
The seven new critical severity disclosures are:
- CVE-2024-9680 (CVSS 9.8): Attackers achieved unauthorized RCE in the content process by exploiting a Use-After-Free in Animation timelines. CVE-2024-9680 is being exploited in the wild.
- CVE-2024-10468 (CVSS 9.8): Potential race conditions in IndexedDB allows memory corruption, leading to a potentially exploitable crash.
- CVE-2024-9392 (CVSS 9.8): A compromised content process enables arbitrary loading of cross-origin pages.
- CVE-2024-10467, CVE-2024-9401 and CVE-2024-9402 (CVSS 9.8): Memory safety bugs present in Firefox showed evidence of memory corruption. Security researchers presume that with enough effort some of these could have been exploited to run arbitrary code.
- CVE-2024-10004 (CVSS 9.1): Opening an external link to an HTTP website when Firefox iOS was previously closed and had an HTTPS tab open could result in the padlock icon showing an HTTPS indicator incorrectly.
Summary
Our monthly Threat Tracking blog covers major cybersecurity trends and high-risk threats. Key insights for October 2024 include expanded efforts to counter ransomware internationally and the role proactive vulnerability management plays in preventing successful ransomware attacks. Other highlights include Fortinet and Palo Alto vulnerabilities actively exploited and updates on an Iranian-backed cyber attack campaign targeting public-facing services of critical infrastructure sector entities. Additionally, F5 BIG-IP LTM’s unencrypted cookie vulnerability, exploited for reconnaissance, and four new Mozilla Firefox vulnerabilities, one actively weaponized, underscore the need for vigilance.
Greenbone facilitates identification and remediation of these vulnerabilities and more, helping organizations enhance resilience against evolving cyber threats. Prioritizing rapid detection and timely patching remains crucial for mitigating risk.