Open Source Vulnerability Management
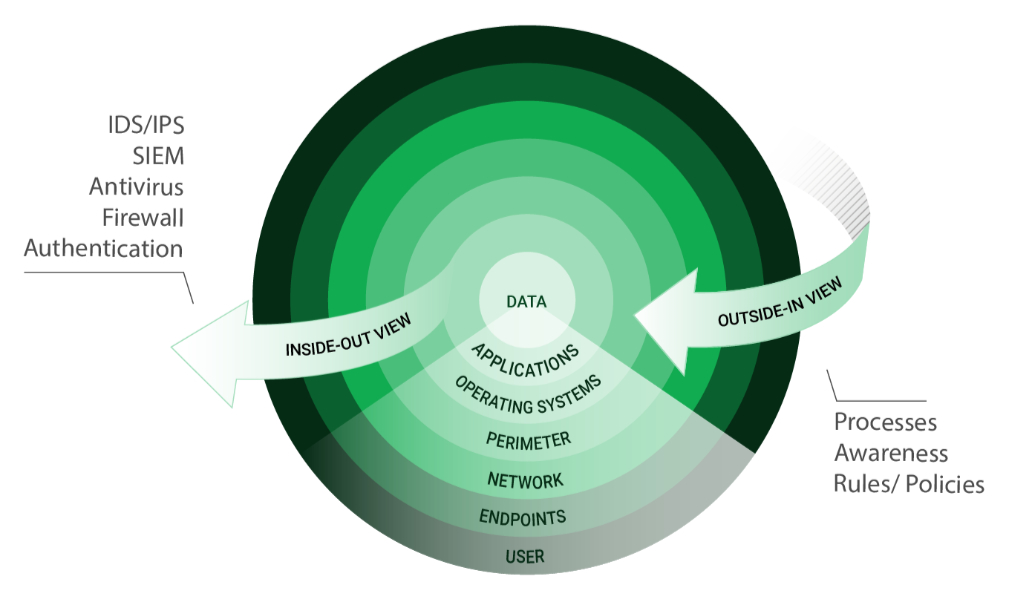
Outside-in Instead of Inside-Out
With open source vulnerability management, you are looking at your IT infrastructure from the outside – just like a potential attacker would. The aim is to locate any vulnerability that might exist in your IT infrastructure.
What Are the Benefits of Externally Focused Vulnerability Management?
Be a Moving Target – Hard to Hit
Run for cover – it’s the right reaction, even in cyberspace. But have a plan first. Vulnerability management is the answer.
You can reduce your attack surface by
99%.
Stay One Step Ahead of Attackers
How Can Vulnerabilities Be Systematically Identified and Addressed?
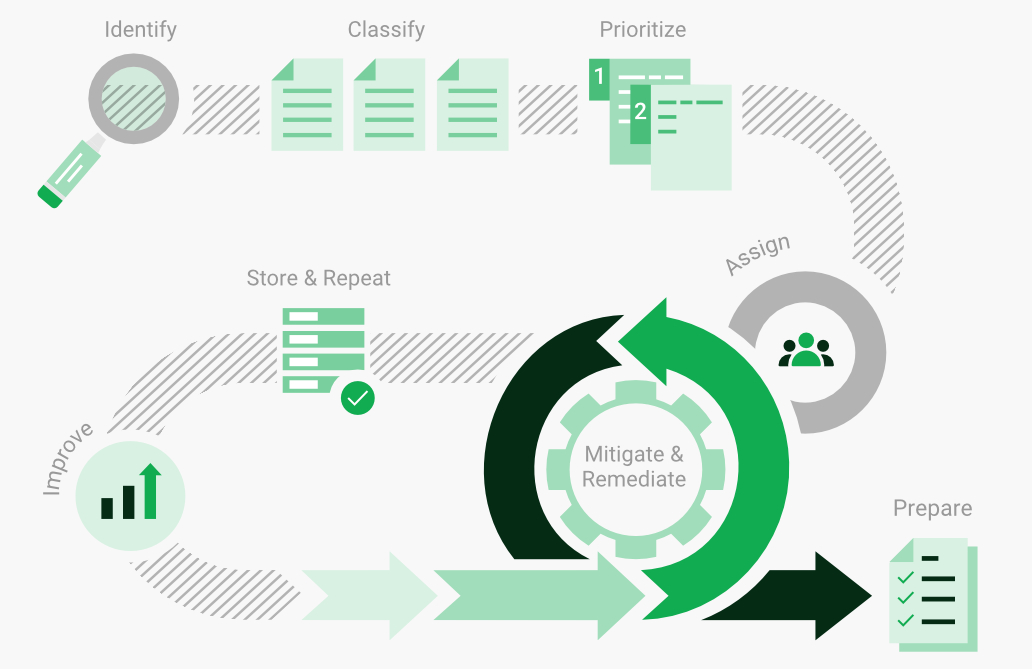
IT security is a process – Open Source vulnerability management provides the foundation. Once you know where the chinks are in your armor, you can do something about them.
The process – from recognition to remedy and monitoring – represents a continuous cycle. You’ll always be one step ahead of attackers.
Still another plus: with our IT security solutions you can focus your hot spots, thus increasing the efficiency of antivirus systems, firewalls & Co.
Tight Budget?
Vulnerability management is the smart way to go with your IT budget.
We’ll calculate it for you.
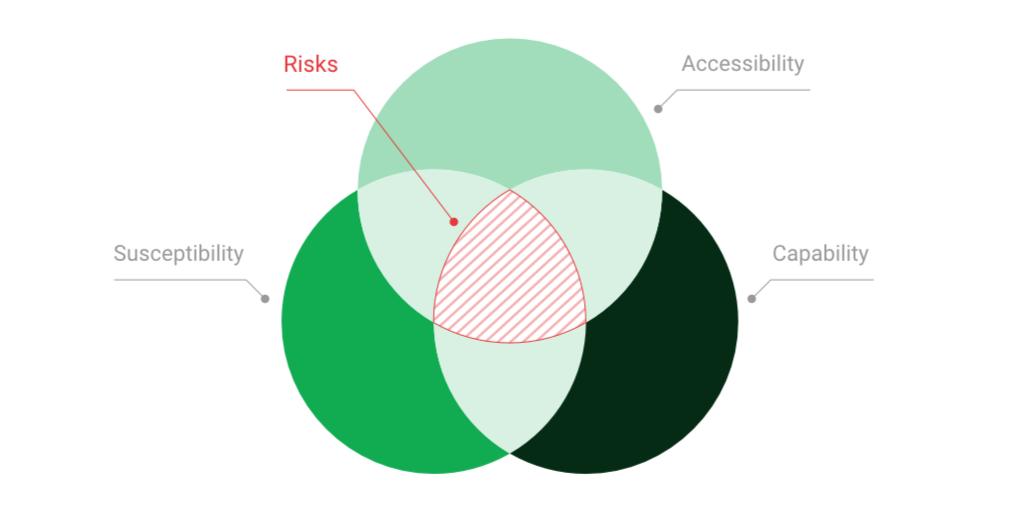
Recognize and Manage Risks
What Are the Common Causes of Vulnerabilities in IT Systems?
Any IT system is at risk of attack by skilled hackers.
Typical causes of vulnerability are improper configuration or programming errors, unauthorized installations or violations of security measures. Our Greenbone Enterprise Appliance uncovers these and countless other risks – and helps you set priorities.
Set up a Process
We’ll be happy to help you set up your own vulnerability management process. It will be tailored to your systems, structures and requirements.
Targeted Approach with Open Source Vulnerability Management
Your Greenbone solution will test your IT network and any devices connected to it for more than 150,000 vulnerabilities – automatically. You will receive a daily security status update. The vulnerability check also gives you information on the severity of the problem so that you can set priorities.
The Greenbone Enterprise Feed tests IT networks as well as any connected devices for more than 150,000 different types of vulnerabilities – automatically. You’ll get a daily status of your threat level.
Security Is a Process
Remedies are part of vulnerability management. Recognition must thus lead to a process that will eliminate detected weaknesses. Any vulnerability management process should answer three questions:
- Who gets which information about vulnerabilities and when?
- Who is responsible for what?
- What remedies are available?
Setting Priorities
Vulnerability in an online web server is riskier than in an offline system with telephone access.
Damage to machinery used in manufacturing is usually a lot more expensive to repair than damage to a web server used for image films.
That’s why setting priorities is so important. There are two important rules of thumb for prioritising measures in vulnerability management:
- Online before offline, as online generally harbours a greater risk.
- Economic prioritisation: Vulnerabilities that are easy to fix have priority.
A Patch? Important, but No Substitute for Open Source Vulnerability Management
Even carefully patched systems require careful vulnerability management. Why?
- System interdependency frequently makes patching impossible. Possible reasons: Special enterprise-critical applications may lose certification or they may malfunction.
- Not every type of vulnerability can be patched.
- Improper configuration can cause vulnerability, even with up-to-date software. Some classic examples are an administrator password like “12345678” or file system shares that are exposed to the Internet by mistake.
Full Transparency – Made in Germany
What Role Do Certifications and Compliance Play in Vulnerability Management?
As a German manufacturer, Greenbone is committed to German data protection standards, which are among the strictest in the world. This means that we also fulfil compliance guidelines at European and international level, such as those set out in the GDPR (General Data Protection Regulation). In addition, Greenbone cloud services always fulfil all GDPR requirements 100 percent. In Germany, the IT baseline protection of the Federal Office for Information Security (BSI) serves as a guideline for information security. An important building block is the establishment of an Information Security Management System (ISMS). For this reason, Greenbone is certified for both its ISMS (ISO 27001) and its quality management (ISO 9000). Users of our solutions also benefit from comprehensive, high-quality support and service offerings.
The combination of security, quality, trust and innovation makes Greenbone solutions “Made in Germany” the first choice worldwide for companies and institutions that want to significantly increase the security of their IT infrastructures.
More about Greenbone certifications here.
Test Us!
Greenbone Basic
Our entry-level enterprise product for 2,450 € per year
Frequently Asked Questions about Open Source Vulnerability Management
What does Open Source Vulnerability Management mean?
Open Source Vulnerability Management is an IT security process that aims to find vulnerabilities in the IT infrastructure, classify their severity and, in addition, provides a list of actions to be taken to address the vulnerabilities. The goal is to eliminate vulnerabilities so that they can no longer pose a risk.
What are the advantages of Open Source Vulnerability Management?
999 out of 1,000 vulnerabilities have been known for more than a year. With Open Source Vulnerability Management, these vulnerabilities can therefore be detected and eliminated before they are exploited by an attacker. This greatly reduces the attack surface of the IT infrastructure.
Vulnerability management systems are fully automated and, through features such as schedules and custom scan configurations, offer users the ability to create complete Open Source Vulnerability Management processes that constantly scan for vulnerabilities. The end result is that Open Source Vulnerability Management ensures more resilient systems in the long term.
How does Open Source Vulnerability Management work?
Open Source Vulnerability Management is a process in IT-security aimed at finding weaknesses in an IT-infrastructure, evaluating their severity and proposing measures to eliminate them. The goal is is ultimately to eliminate weaknesses so cyber criminals can not exploit them.
The Greenbone Enterprise Alliances as well as the Greenbone Cloud Service use the Greenbone Enterprise Feed. The feed consists of over 150.000 vulnerability tests (VTs). Simply put, there is a vulnerability test for every known weakness, able to recognize exactly that particular weakness on all active elements of a given IT-infrastructure – be it desktop-PCs, Servers, Alliances and intelligent components like routers or VoIP-devices.
The scanner runs the tests on the target network and finds existing security gaps. These are then ranked by severity, enabling prioritization of extermination-measures.
For which companies is Open Source Vulnerability Management suitable?
Every company derives significant benefits from the use of Open Source Vulnerability Management, as proactive security can be achieved.
Greenbone’s Open Source Vulnerability Management solutions are suitable for businesses and government agencies of all sizes. Solutions are available for both micro-enterprises, where only a few IP addresses need to be scanned, and large enterprises with many branch offices.
What are the costs of Open Source Vulnerability Management from Greenbone?
The price of our solution is always based on the environment to be scanned. Depending on whether you are interested in a virtual appliance, a physical appliance or our cloud solution, our solutions cost between a few euros per month to several hundred thousand euros.
How much time does Open Source Vulnerability Management take?
Open Source Vulnerability Management is not a one-off operation, but an ongoing process that is firmly integrated into IT security. The steps from the detection to the elimination of vulnerabilities run continuously in a constant cycle.
The duration of a scan always depends on the number of systems to be scanned or IP addresses to be scanned. Open Source Vulnerability Management makes sense for any size of system, but can run for several hours as a background activity depending on the complexity of the respective scan.
What are the advantages of Open Source Vulnerability Management from Greenbone?
With solutions from Greenbone, you receive a daily update of vulnerability tests. Since new vulnerabilities are found every day, it is important to continuously develop new tests. With the Greenbone Enterprise Feed as part of the Greenbone solutions, you are always up to date.
Another advantage is that with Greenbone solutions you directly receive a classification of vulnerabilities according to their severity as well as possible measures for remediation. This allows for prioritization and targeted remediation of the vulnerabilities.
In addition, when you choose Greenbone, you get technology from a trusted German manufacturer. All Greenbone solutions always comply 100 % with the specifications of the highest data protection standards such as the DSGVO.
What prior knowledge does Open Source Vulnerability Management require?
The basis of Open Source Vulnerability Management is general awareness of the fact that IT-systems have weaknesses and the willingness to do something about that.
Merely implementing our Open Source Vulnerability Management solution is comparatively easy. However, to derive meaningful benefits from it, IT knowledge at admin level is an advantage.
We are already using firewalls etc. Is Open Source Vulnerability Management still useful?
We are already using firewalls etc. Is Open Source Open Source Vulnerability Management still useful?Definitely. Firewalls and most other common measures focus on attack patterns – viewing the target system from the inside out. The goal is defending against attacks that are actually occurring. For this reasons, these systems only engage once an attack is already on the way.
In comparison to this, Open Source Vulnerability Management views the IT-infrastructure from the outside in – just like a potential attacker. The goal here is to eliminate attack surfaces in order to stop any attacks from happening in the first place.
High grade firewall systems can occasionally detect vulnerabilities, however contrary to Open Source Vulnerability Management they will not propose any measures to eliminate them. Additionally, firewalls, IDS- or IPS-systems can only detect weaknesses if the system they are running on allows them to do so in the first place, and even then they will be restricted to a range of traffic correlating to the respective system security.
Traffic which does not pass through the security system will not be analyzed either. If a Greenbone solution is implemented in the network, every component that can be reached via an IP-connection can be probed for weaknesses, no matter the type of device. This, for example, also includes industrial components, robots and production plants.
A combination of firewalls etc. and Open Source Vulnerability Management is certainly the best solution. With the insight Open Source Vulnerability Management provides, the use of other systems can be focused on important hot spots.
What is the difference between Patch-Management and Open Source Vulnerability Management?
In patch-management, systems, applications and products get updated continually in order to close weaknesses.
Open Source Vulnerability Management serves to find existing weaknesses, rank and prioritize them and to propose measures to eliminate them. A patch is one example of such a measure.
In this sense, patch-management presupposes Open Source Vulnerability Management. Patching a vulnerability only makes sense when you are aware of the vulnerability.
Additionally, most patch managers only work in IT-components but not in industrial plants or controllers for example.
Finally, patch-management systems require exhaustive and controlling admin interventions, since not every patch is necessarily sensible or uncritical for the system. New patches often bring along new vulnerabilities which the patch management system can not recognize.
Patch-management is a sensible addition to Open Source Vulnerability Management, since they can automate patches. In some cases, our systems can even communicate information to the patch management system, allowing it to patch based on critical security information.
Do I need Open Source Vulnerability Management although I update my systems regularly?
Yes, even with regular updates and patches, it still makes sense to have a Open Source Vulnerability Management solution.
For example, system dependencies often prohibit going for the most recent patch. Certain critical applications could lose their certification or might even lose some functionality when upgrading to the latest patch uncritically.
Not every vulnerability receives a patch either, or even worse, some updates even introduce new vulnerabilities into the system. Without a Open Source Vulnerability Management system in place probing all areas of the system, these vulnerabilities often go unnoticed.
Furthermore, even in an optimally patched system, vulnerabilities can arise due to misconfiguration. A classic example would be the admin-password “12345678” or accidental file-sharing to the internet instead of the local network.
OT-components have the additional drawback of prohibiting automatic updates in the first place.
Does Open Source Vulnerability Management improve with continuous patching?
Yes, continuous vulnerability management combined with patch-management delivers a severely more resilient system over time.
What is the biggest challenge in Open Source Vulnerability Management?
The biggest challenge is the initial installation and implementation into the network. But the way our solution is designed makes it as quick and straightforward as possible. You will also receive additional support from Greenbone if needed.
Since working with a multitude of scan-plans is recommended, comprehensive asset-management is required prior to implementing Open Source Vulnerability Management in order to differentiate critical and non-critical assets from each other.
What are the most important prerequisites for Open Source Vulnerability Management?
All companies, no matter the sector, are in the focus of attackers these days. The most important prerequisite for Open Source Vulnerability Management is a keen awareness of this fact and a willingness of those who are responsible to put preventive measures in place.
As a customer, it is also very important for you to make an informed decision: View a demonstration of the product to see how it performs in a test-situation and chart out initial- and running costs. Further technical knowledge is not required, as the mere implementation is very easy.