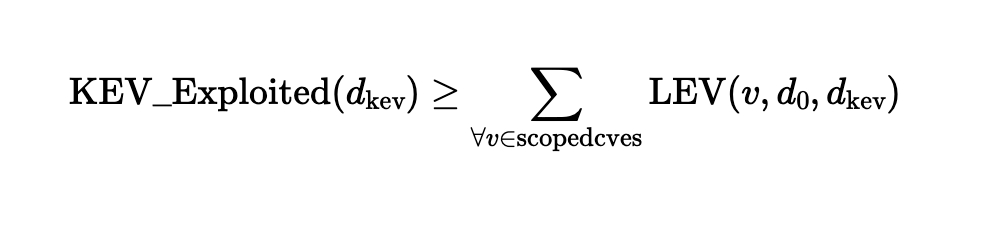The July 2025 Threat Report takes a broad approach, covering some of the top cyber threats from the past month. The Microsoft SharePoint flaw titles “ToolShell” dominated the headlines; see our alert on ToolShell for a detailed analysis. Over 4,000 CVEs were published last month; almost 500 of them were rated Critical, with CVSS over 9.0. Managing this volume of risk is truly a battle of attrition for defenders. In response, Greenbone published almost 5,000 new detection tests. These detection tests allow defenders to find known software flaws in their environment, confirm patch levels, and prevent cyber attackers from gaining the upper hand.

Critical Cisco ISE Flaws Offer Unauthenticated RCE as Root and More
Cisco has confirmed active exploitation of Cisco Identity Services Engine (ISE) and Cisco ISE-PIC (Passive Identity Connector) versions 3.3 and 3.4. The highest severity CVEs are: CVE-2025-20281, CVE-2025-20337, and CVE-2025-20282; all CVSS 10. CVE-2025-20281 and CVE-2025-20337 have been added to CISA KEV (catalog of known exploited vulnerabilities). Each flaw can be exploited to execute code with root privileges by submitting a malicious API request. Several national CERT agencies have issued alerts: EU-CERT, CSA Singapore, NHS UK, and NCSC Ireland. Cisco advises immediate patching; no workarounds are available. Version detection tests are included in the OPENVAS ENTERPRISE FEED [1][2][3].
Another critical severity CVE in Cisco Unified Communications Manager made waves in early July. CVE-2025-20309 (CVSS 10) allows remote root account access via static SSH credentials. Alerts were issued from Belgium’s CERT.be, NSSC Ireland, and the flaw was featured on the AUSCERT Week in Review.
CrushFTP and WingFTP Servers Under Active Attack
High severity CVEs in CrushFTP and WingFTP were published and quickly added to CISA KEV, with global CERT advisories being issued [1][2][3]. FTP servers are often exposed to the public Internet, but instances within a local network could also offer hackers an opportunity for persistence and lateral movement [4]. Also, FTP servers often store sensitive data, which could represent a high risk of being ransomed.
- CVE-2025-54309 (CVSS 9.8, EPSS ≥ 91st pctl): If the DMZ proxy feature is not used, CrushFTP is susceptible to an unprotected alternate channel vulnerability [CWE-420]. The software mishandles AS2 validation allowing remote HTTPS admin access. The OPENVAS ENTERPRISE FEED includes a remote banner detection test to identify vulnerable instances. Users should upgrade to CrushFTP 10.8.5_12 (or later) or 11.3.4_23 (or later).
- CVE-2025-47812 (CVSS 10, EPSS ≥ 99th pctl): Unsanitized null-byte characters in the web-interface of WingFTP prior to version 7.4.4 allow remote execution of arbitrary Lua code with the privileges of the FTP service (root or SYSTEM by default). Greenbone includes an active check and version check to identify vulnerable instances. Users are urged to update to version 7.4.4 or later.
Node.js Patch Bypass Exposes Arbitrary File Access
CVE-2025-27210 (CVSS 7.5) is a bypass for CVE-2025-23084 (CVSS 5.6), a previously patched flaw in Node.js Windows platforms, published in January 2025. An estimated 4.8% of global web servers run Node.js, which also powers many on-premises and cloud-native applications. National CERT advisories have been released warning of high risk [1][2]. At least one proof-of-concept (PoC) has been published [3]. OPENVAS ENTERPRISE FEED and COMMUNITY FEED both include a version detection check.
The flaw, classified as path traversal [CWE-22], is due to built-in functions path.join() and path.normalize() not properly filtering Windows device names like CON, PRN, and AUX, which are reserved names for special system devices [4]. This can be exploited remotely to bypass path protections when user input is passed into these functions. Node.js versions 20.x prior to 20.19.4, as well as 22.x before 22.17.1 and 24.x before 24.4.1 are affected.
CVE-2025-37099: Total Remote Compromise for HPE Insight Remote Support
New vulnerabilities in HPE Insight Remote Support pose an extreme risk of full system compromise within enterprise infrastructure. IRS is used in enterprise local network environments to automate hardware health checks, infrastructure monitoring, and support ticket generation.
CVE-2025-37099 (CVSS 9.8) permits unauthenticated remote code execution (RCE) at SYSTEM level due to improper input validation [CWE-20] in processAttachmentDataStream logic, allowing malicious payloads to be executed as code [CWE‑94][1]. This allows attackers to execute malware across managed systems. While not explicitly documented, SYSTEM-level access could also enable attackers to manipulate or delete monitoring logs to conceal activity. Since the affected service often communicates with devices like servers and iLO controllers, compromise may facilitate pivoting laterally within a network. [2]
Users should upgrade immediately to 7.15.0.646 or newer. The coordinated disclosure also included two additional CVEs; CVE-2025-37098 and CVE-2025-37097, both CVSS 7.5. OPENVAS ENTERPRISE FEED includes a version detection test to identify vulnerable instances and verify patch level to meet compliance.
Critical Patches for DELL CVEs with Elevated EPSS Scores
Cumulative patches for a wide number of Dell Technologies products were released to patch various component vulnerabilities. Canadian Cyber CSE has issued three alerts in July addressing these updates [1][2][3]. Here are some of the most critical CVEs from this batch, all of which can be detected with the OPENVAS ENTERPRISE FEED [1][2][3][4][5]:
- CVE-2024-53677 (CVSS 9.8, EPSS ≥ 99th pctl): Dell Avamar Data Store and Avamar Virtual Edition have received updates to address a flaw in Apache Struts. No mitigations or workarounds are available. See the vendor’s advisory for affected product lists.
- CVE-2025-24813 (CVSS 9.8, EPSS ≥ 99pctl): Dell Secure Connect Gateway versions prior to 5.30.0.14 are affected by an Apache Tomcat flaw and other critical CVEs. Dell has classified this update as critical.
- CVE-2004-0597 (CVSS 10, EPSS ≥ 99pctl): Dell Networker is affected by critical buffer overflow flaws in libpng that allow remote attackers to execute arbitrary code via maliciously manipulated PNG images among other vulnerabilities. See vendor advisories for more information [1][2][3][4].
- CVE-2016-2842 (CVSS 9.8, EPSS ≥ 98pctl): Dell Data Protection Advisor is affected by flaws in numerous components including CVE-2016-2842 in OpenSSL which does not properly verify memory allocation, allowing DoS or possibly RCE. See the vendor advisory for more information.
- CVE-2025-30477 (CVSS 4.4): Dell PowerScale uses a risky cryptographic algorithm, potentially leading to information disclosure. In June 2025, PowerScale patched critical severity flaws. See vendor advisories for more information [1][2].
A Cumulative Summary of 2025 D-Link Flaws
OPENVAS ENTERPRISE FEED and COMMUNITY FEED currently include 27 vulnerability tests covering the majority of CVEs affecting D-Link products published so far in 2025. Given the importance of network edge security, users should pay particular attention to vulnerabilities in routers and other gateway devices. After the settlement of a U.S. regulatory action involving D‑Link and the Federal Trade Commission, in 2019 D‑Link agreed to implement a comprehensive security program. However, proponents for accountability may ask whether intervention should be more widespread. Ivanti products, for example, have been inundated with numerous high severity flaws in recent years [1][2][3][4][5], many leveraged in ransomware attacks.
Adobe Patches Critical Flaws for ColdFusion
Security updates for ColdFusion 2025, 2023, and 2021 address 13 new CVEs; five critical severity issues including XXE (CVE-2025-49535, CVSS 9.3), hard-coded credentials (CVE-2025-49551, CVSS 8.8), OS command injection, XML injection, and SSRF. In 2023, the ColdFusion flaw CVE‑2023‑26360 (CVSS 9.8) was used by threat actors to gain initial access to US federal civilian agencies.
OPENVAS ENTERPRISE FEED includes a remote version check to identify unpatched instances. Immediate patching to Update 3 (ColdFusion 2025), Update 15 (2023), or Update 21 (2021) is strongly recommended.
Splunk Enterprise Updates Critical Severity Components
Cumulative updates for Splunk Enterprise patch several third-party components in Splunk Enterprise including golang, postgres, aws-sdk-java, idna, and others. Some of these were Critical CVSS severity flaws such as CVE-2024-45337 (CVSS 9.1) with an EPSS percentile of ≥ 97%, indicating a high likelihood of exploit activity. CERT-FR and the Canadian Cyber CSE have published alerts related to Splunk’s July advisories. Users can verify patch status with a version check in the OPENVAS ENTERPRISE FEED. The feed also includes vulnerability checks for previous Splunk security advisories and CVEs.
Oracle Patches Row of High Severity VirtualBox Flaws
Several CVEs published in mid‑July 2025 affecting Oracle VM VirtualBox version 7.1.10 permit a high‑privileged local attacker (with access to the host infrastructure or guest VM execution environment) to compromise VirtualBox, potentially escalating privileges or achieving full control of the hypervisor core component. CVE‑2025‑53024 (CVSS 8.2) is an integer overflow bug in the VMSVGA virtual device due to insufficient validation of user‑supplied data, leading to memory corruption with potential for full hypervisor compromise. [1] OPENVAS ENTERPRISE FEED and COMMUNITY FEED include version detection tests for Windows, Linux, and macOS.
Post Authentication Flaw Allows RCE in SonicWall SMA100
CVE-2025-40599 (CVSS 9.1) is an authenticated arbitrary file upload vulnerability in SonicWall SMA 100 series appliances. It allows a remote attacker with administrative privileges to gain arbitrary code execution and persistent access. The risk posed by this flaw is increased by weak or stolen credentials. The flaw affects models SMA 210, 410, and 500v, versions 10.2.1.15-81sv and earlier. As per the vendor advisory, no workaround is effective. OPENVAS ENTERPRISE FEED includes a remote version check to identify the affected devices.
New MySQL CVEs Allow Authenticated DoS Attacks
Amidst the abundance of vulnerabilities offering unauthorized RCE, it’s easy to overlook ones that merely cause Denial of Service (DoS). A swath of DoS vulnerabilities and related patches were issued for MySQL 8 and MySQL 9 in July [1]. Although the flaws require privileged access to exploit, Managed Service Providers (MSP) may provide shared MySQL hosting for small-to-medium businesses (SMBs), government agencies, or non-profits that don’t want the overhead of managing their own database infrastructure. In this scenario, tenants are given access to separate databases on the same MySQL server instance. When that happens, an unpatched instance could allow a user to impact other organizations. These flaws also highlight the importance of strong passwords and mitigating the threat from brute-force and password spraying attacks.
Remote version detection tests are available for all CVEs referenced below. These are included in both the OPENVAS ENTERPRISE FEED and COMMUNITY FEED. Tests cover both Linux and Windows MySQL installations.
| CVE ID | Affected Versions | Impact | Access Vector | Patch Status |
|
(CVSS 6.5) |
8.0.0–8.0.42, 8.4.0–8.4.5, 9.0.0–9.3.0 | DoS (hang/crash) | Remote authenticated access | Patched (July 2025) |
|
(CVSS 6.5) |
8.0.0–8.0.42, 8.4.0–8.4.5, 9.0.0–9.3.0 | DoS (crash) | Remote authenticated access | Patched (July 2025) |
|
(CVSS 6.5) |
8.0.0–8.0.42, 8.4.0–8.4.5, 9.0.0–9.3.0 | DoS (crash) | Remote authenticated access | Patched (July 2025) |