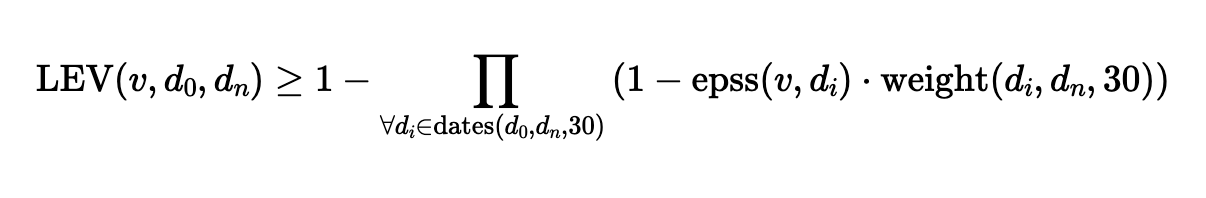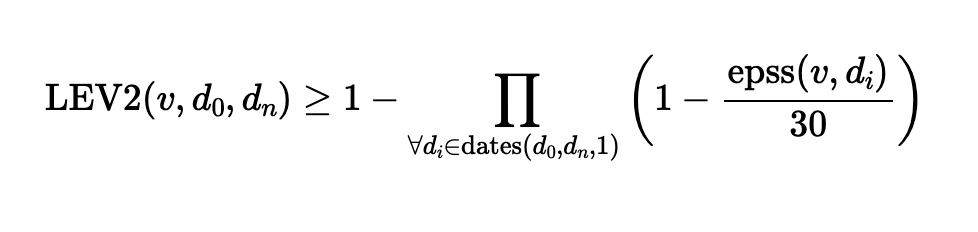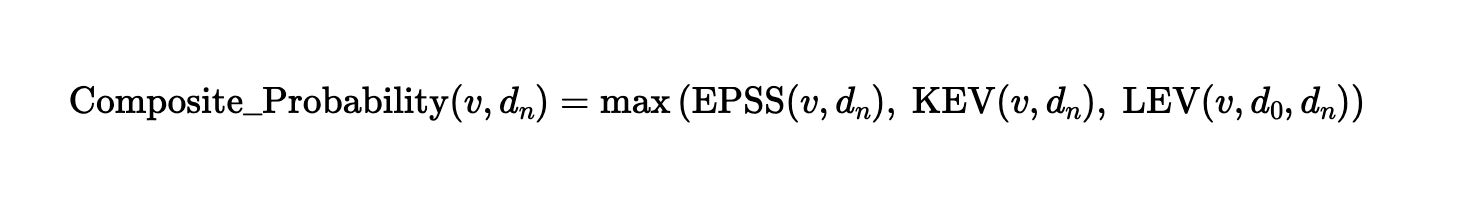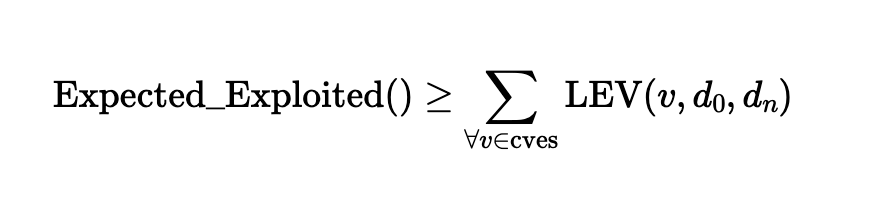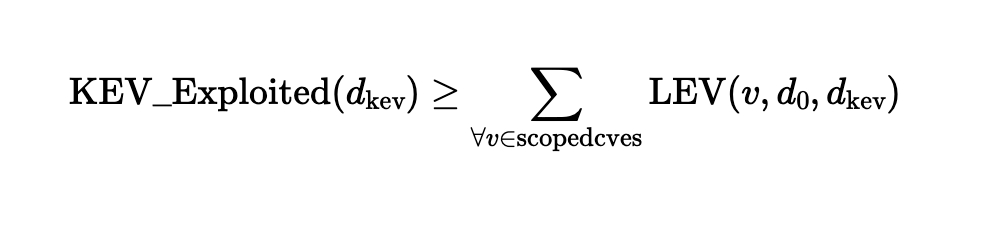When it comes to protecting your organization from digital threats, who should you trust? Reality dictates that high-resilience IT security is forged from a network of strong partnerships, defense in depth; layered security controls, and regular auditing. Defensive posture needs to be monitored, measured and continuously improved. While vulnerability management has always been a core security control, it is nonetheless a fast moving target. In 2025, continuous and prioritized mitigation of security threats can have a big impact on security outcomes as adversarial time-to-exploit diminishes.

In March 2025’s monthly Threat Report, we will highlight the importance of vulnerability management and Greenbone’s industry leading vulnerability detection by reviewing the most recent critical threats. But these new threats only scratch the surface. In March 2025, Greenbone added 5,283 new vulnerability tests to our Enterprise Feed. Let’s jump into some of the important insights from a highly active threat landscape.
The US Treasury Breach: How Did It Happen?
In late December 2024, the U.S. Treasury Department disclosed that its network was breached by Chinese state-backed hackers and subsequently leveraged sanctions in early January 2025. Forensic investigations have tracked the root-cause to a stolen BeyondTrust API key. The vendor has acknowledged 17 other customers breached by this flaw. Deeper investigation has revealed that the API key was stolen via a flaw in a PostgreSQL built-in function for escaping untrusted input.
When invalid two-byte UTF-8 characters are submitted to a vulnerable PostgreSQL function, only the first byte is escaped, allowing a single quote to pass through unsanitized which can be leveraged to trigger an SQL Injection [CWE-89] attack. The exploitable functions are PQescapeLiteral(), PQescapeIdentifier(), PQescapeString() und PQescapeStringConn(). All versions of PostgreSQL before 17.3, 16.7, 15.11, 14.16, and 13.19 are affected as well as numerous products that depend on these functions.
CVE-2024-12356, (CVSS 9.8) and CVE-2024-12686, (CVSS 7.2) have been issued for BeyondTrust Privileged Remote Access (PRA) and Remote Support (RS) and CVE-2025-1094 (CVSS 8.1) addresses the flaw in PostgreSQL. The issue is the subject of several national CERT advisories including Germany’s BSI Cert-Bund (WID-SEC-2024-3726) and the Canadian Centre for Cybersecurity (AV25-084). The flaw has been added to CISA’s known exploited vulnerabilities (KEV) list, and a Metasploit module that exploits vulnerable BeyondTrust products is available, increasing the risk. Greenbone is able to detect the CVEs (Common Vulnerabilities and Exposures) discussed above both in BeyondTrust products or instances of PostgreSQL vulnerable to CVE-2025-1094.
Advanced fined 3.1 Million Pound for Lack of Technical Controls
This month, the UK’s Information Commissioner’s Office (ICO) imposed a 3.07 million Pound fine on Advanced Computer Software Group Ltd. under the UK GDPR for security failures. The case is evidence of how the financial damage caused by a ransomware attack can be further exacerbated by regulatory fines. The initial proposed amount was even higher at 6.09 million Pound. However, since the victim exhibited post-incident cooperation with the NCSC (National Cyber Security Centre), NCA (National Crime Agency) and NHS (National Health Service), a voluntary settlement of 3,076,320 Pound was approved. While operational costs and extortion payments have not been publicly disclosed, they likely add between 10 to 20 million Pound to the incident’s total costs.
Advanced is a major IT and software provider to healthcare organizations including the NHS. In August 2022, Advanced was compromised, attackers gained access to its health and care subsidiary resulting in a serious ransomware incident. The breach disrupted critical services including NHS 111 and prevented healthcare staff from accessing personal data on 79,404 individuals, including sensitive care information.
The ICO concluded that Advanced had incomplete MFA coverage, lacked comprehensive vulnerability scanning and had deficient patch management practices at the time of the incident – factors that collectively represented a failure to implement appropriate technical and organizational measures. Organizations processing sensitive data must treat security controls as non-negotiable. Inadequate patch management remains one of the most exploited gaps in modern attack chains.
Double Trouble: Backups Are Critical to Ransomware Mitigation
Backups are an organization’s last defense against ransomware and most sophisticated advanced persistent threat (APT) actors are known to target their victim’s backups. If a victim’s backups are compromised, submission to ransom demands is more likely. In 2025, this could mean multi-million Dollar losses. In March 2025, two new significant threats to backup services were revealed; CVE-2025-23120, a new critical severity flaw in Veeam was disclosed, and campaigns targeting CVE-2024-48248 in NAKIVO Backup & Replication were observed. Identifying affected systems and patching them is therefore an urgent matter.
In October 2024, our threat report alerted about another vulnerability in Veeam (CVE-2024-40711) being used in ransomware attacks. Overall, CVEs in Veeam Backup and Replication have a high conversion rate for active exploitation, PoC (Proof of Concept) exploits, and use in ransomware attacks. Here are the details for both emerging threats:
- CVE-2024-48248 (CVSS 8.6): Versions of NAKIVO Backup & Replication before 11.0.0.88174 allow unauthorized Remote Code Execution (RCE) via a function called getImageByPath which allows files to be read remotely. This includes database files containing cleartext credentials for each system that NAKIVO connects to and backs up. A full technical description and proof-of-concept is available and this vulnerability is now tracked as actively exploited.
- CVE-2025-23120 (CVSS 9.9): Attackers with domain user access can trigger deserialization of attacker-controlled data through the .NET Remoting Channel. Veeam attempts to restrict dangerous types via a blacklist, but researchers discovered exploitable classes (xmlFrameworkDs and BackupSummary) not on the list. These extend .NET’s DataSet class – a well-known RCE vector – allowing arbitrary code execution as SYSTEM on the backup server. The flaw is the subject of national CERT alerts globally including HK, CERT.be, and CERT-In. As per Veeam’s advisory, upgrading to version 12.3.1 is the recommended way to mitigate the vulnerability.
Greenbone is able to detect vulnerable NAKIVO and Veeam instances. Our Enterprise Feed has an active check [1] and version check [2] for CVE-2024-48248 in NAKIVO Backup & Replication, and a remote version check [3] for the Veeam flaw.
IngressNightmare: Unauthenticated Takeover in 43% of Kubernetes Clusters
Kubernetes is the most popular enterprise container orchestration tool globally. Its Ingress feature is a networking component that manages external access to services within a cluster, typically HTTP and HTTPS traffic. A vulnerability dubbed IngressNightmare has exposed an estimated 43% of Kubernetes clusters to unauthenticated remote access – approximately 6,500 clusters, including Fortune 500 companies.
The root-cause is excessive default privileges [CWE-250] and unrestricted network accessibility [CWE-284] in the Ingress-NGINX Controller tool, based on NGINX reverse proxy. IngressNightmare allows attackers to gain complete unauthorized control over workloads, APIs or sensitive resources in multi-tenant and production-grade clusters. A full technical analysis is available from the researchers at Wiz, who pointed out that K8 Admission Controllers are directly accessible without authentication by default, presenting an appealing attack surface to hackers.
The full attack trajectory to achieve arbitrary RCE against an affected K8 instance requires exploiting Ingress-NGINX. First, CVE-2025-1974 (CVSS 9.8) to upload a binary payload as the request body. It should be larger than 8kb in size while specifying a Content-Length header larger than the actual content size. This triggers NGINX to store the request body as a file, and the incorrect Content-Length header means the file will not be deleted as the server waits for more data [CWE-459].
The second stage of this attack requires exploiting CVE-2025-1097, CVE-2025-1098, or CVE-2025-24514 (CVSS 8.8). These CVEs all similarly fail to properly sanitize input [CWE-20] submitted to Admission Controllers. Ingress-NGINX converts Ingress objects to configuration files and validates them with the nginx -t command, allowing attackers to execute a limited set of NGINX configuration directives. Researchers found the ssl_engine module can be triggered to load the shared library binary payload uploaded in the first stage. Although exploitation is not trivial and no public PoC code exists yet, sophisticated threat actors will easily convert the technical analysis into effective exploits.
The Canadian Centre for Cyber Security has issued a CERT advisory (AV25-161) for IngressNightmare. Patched Ingress-NGINX versions 1.12.1 and 1.11.5 are available and users should upgrade as soon as possible. If upgrading the Ingress NGINX Controller is not immediately possible, temporary workarounds can help reduce risk. Strict network policies can restrict access to a cluster’s Admission Controllers allowing access to only the Kubernetes API Server. Alternatively, the Admission Controller component of Ingress-NGINX can be disabled entirely.
Greenbone is able to detect IngressNightmare vulnerabilities with an active check that verifies the presence of all CVEs mentioned above [1][2].
CVE-2025-29927: Next.js Framework Under Attack
A new vulnerability in Next.js, CVE-2025-29927 (CVSS 9.4) is considered high risk due the framework’s popularity and the simplicity of exploitation [1][2]. Adding to the risk, PoC exploit code is publicly available and Akamai researchers have observed active scans probing the Internet for vulnerable apps. Several national CERTs (Computer Emergency Response Teams) have issued alerts for the issue including CERT.NZ, Australian Signals Directorate (ASD), Germany’s BSI Cert-Bund (WID-SEC-2025-062), and the Canadian Centre for Cyber Security (AV25-162).
Next.js is a React middleware framework for building full-stack web applications. Middleware refers to components that sit between two or more systems and handle communication and orchestration. For web-applications, middleware converts incoming HTTP requests into responses and is often also responsible for authentication and authorization. Due to CVE-2025-29927, attackers can bypass Next.js middleware authentication and authorization simply by setting a malicious HTTP header.
If using HTTP headers seems like a bad idea for managing a web application’s internal process flow, CVE-2025-29927 is the evidence. Considering user-provided headers were not correctly distinguished from internal ones, this vulnerability should attain the status of egregious negligence. Attackers can bypass authentication by simply adding the `x‑middleware‑subrequest` header to a request and overloading it with at least as many values as the MAX_RECURSION_DEPTH which is 5. For example:
`x-middleware-subrequest: middleware:middleware:middleware:middleware:middleware`
The flaw is fixed in Next.js versions 15.2.3, 14.2.25, 13.5.9 and 12.3.5, and users should follow the vendor’s upgrade guide. If upgrading is infeasible, it is recommended to filter the `x-middleware-subrequest` header from HTTP requests. Greenbone is able to detect vulnerable instances of Next.js with an active check and a version check.
Summary
The March 2025 threat landscape was shaped by vulnerable and actively exploited backup systems, unforgivably weak authentication logic, high-profile regulatory fines and numerous other critical software vulnerabilities. From the U.S. Treasury breach to the Advanced ransomware fallout, the theme is clear: trust doesn’t grow on trees. Cybersecurity resilience must be earned; forged through layered security controls and backed up by accountability.
Greenbone continues to play a vital role by providing timely detection tests for new emerging threats and standardized compliance audits that support a wide array of enterprise architectures. Organizations that want to stay ahead of cyber crime need to proactively scan their infrastructure and close security gaps as they appear.