2022-08-08: Greenbone OS 22.04
Current Patch Level: 22.04.28 (2025-06-18)
Lifecycle Status: End-of-Life
22.04.28 (2025-06-18):
- Greenbone OS:
- Status: the lifecycle status of GOS 22.04 was set to “end-of-life”. This means that while GOS 22.04 will remain functional and supported, it will receive a reduced number of patches that will be limited to critical fixes to core functionality and security issues. Note: GOS 22.04 will reach the final end of its lifecycle and be retired on 2026-02-01 (#GOS-2315).
- Bug fix: if the appliance models Greenbone Enterprise 150 or 35 have been installed with GOS 21.04 or earlier, the fstrim service was not enabled. It has been enabled for these cases also to resolve various disk issues (#GOS-2224).
- Security fix: the Intel microcode of the Greenbone Enterprise 6500 R2, 5400 R2, 650 R2, 600 R2, 450 R2, 400 R2 appliance models was upgraded to the current version (CVE-2024-28956, CVE-2024-43420, CVE-2024-45332, CVE-2025-20012, CVE-2025-20054, CVE-2025-20103, CVE-2025-20623, CVE-2025-24495).
- Security fix: the Linux kernel was upgraded from version 5.10.230-greenbone1 to version 5.10.237-greenbone1 for hardware appliances and from version 5.10.226-1 to version 5.10.237-1 for virtual appliances (CVE-2021-47469, CVE-2023-52530, CVE-2023-52917, CVE-2024-26921, CVE-2024-27017, CVE-2024-27072, CVE-2024-35965, CVE-2024-35966, CVE-2024-36476, CVE-2024-36899, CVE-2024-38538, CVE-2024-38544, CVE-2024-38588, CVE-2024-38591, CVE-2024-39497, CVE-2024-40953, CVE-2024-41016, CVE-2024-41060, CVE-2024-41080, CVE-2024-42315, CVE-2024-43098, CVE-2024-44931, CVE-2024-44940, CVE-2024-46695, CVE-2024-46809, CVE-2024-46841, CVE-2024-46849, CVE-2024-46853, CVE-2024-46854, CVE-2024-46858, CVE-2024-46865, CVE-2024-47143, CVE-2024-47670, CVE-2024-47671, CVE-2024-47672, CVE-2024-47674, CVE-2024-47679, CVE-2024-47684, CVE-2024-47685, CVE-2024-47692, CVE-2024-47696, CVE-2024-47697, CVE-2024-47698, CVE-2024-47699, CVE-2024-47701, CVE-2024-47705, CVE-2024-47706, CVE-2024-47707, CVE-2024-47709, CVE-2024-47710, CVE-2024-47712, CVE-2024-47713, CVE-2024-47718, CVE-2024-47723, CVE-2024-47735, CVE-2024-47737, CVE-2024-47739, CVE-2024-47740, CVE-2024-47742, CVE-2024-47748, CVE-2024-47749, CVE-2024-47756, CVE-2024-47757, CVE-2024-48881, CVE-2024-49851, CVE-2024-49858, CVE-2024-49860, CVE-2024-49863, CVE-2024-49867, CVE-2024-49868, CVE-2024-49875, CVE-2024-49877, CVE-2024-49878, CVE-2024-49879, CVE-2024-49881, CVE-2024-49882, CVE-2024-49883, CVE-2024-49884, CVE-2024-49889, CVE-2024-49890, CVE-2024-49892, CVE-2024-49894, CVE-2024-49895, CVE-2024-49896, CVE-2024-49900, CVE-2024-49902, CVE-2024-49903, CVE-2024-49907, CVE-2024-49913, CVE-2024-49930, CVE-2024-49933, CVE-2024-49936, CVE-2024-49938, CVE-2024-49944, CVE-2024-49948, CVE-2024-49949, CVE-2024-49952, CVE-2024-49955, CVE-2024-49957, CVE-2024-49958, CVE-2024-49959, CVE-2024-49962, CVE-2024-49963, CVE-2024-49965, CVE-2024-49966, CVE-2024-49969, CVE-2024-49973, CVE-2024-49974, CVE-2024-49975, CVE-2024-49977, CVE-2024-49981, CVE-2024-49982, CVE-2024-49983, CVE-2024-49985, CVE-2024-49995, CVE-2024-49996, CVE-2024-50001, CVE-2024-50006, CVE-2024-50007, CVE-2024-50008, CVE-2024-50010, CVE-2024-50013, CVE-2024-50015, CVE-2024-50024, CVE-2024-50033, CVE-2024-50035, CVE-2024-50036, CVE-2024-50039, CVE-2024-50040, CVE-2024-50044, CVE-2024-50045, CVE-2024-50046, CVE-2024-50049, CVE-2024-50055, CVE-2024-50058, CVE-2024-50059, CVE-2024-50072, CVE-2024-50074, CVE-2024-50082, CVE-2024-50083, CVE-2024-50095, CVE-2024-50096, CVE-2024-50099, CVE-2024-50103, CVE-2024-50115, CVE-2024-50116, CVE-2024-50117, CVE-2024-50121, CVE-2024-50127, CVE-2024-50131, CVE-2024-50134, CVE-2024-50142, CVE-2024-50148, CVE-2024-50150, CVE-2024-50151, CVE-2024-50153, CVE-2024-50167, CVE-2024-50171, CVE-2024-50179, CVE-2024-50180, CVE-2024-50181, CVE-2024-50184, CVE-2024-50185, CVE-2024-50188, CVE-2024-50192, CVE-2024-50193, CVE-2024-50194, CVE-2024-50195, CVE-2024-50198, CVE-2024-50199, CVE-2024-50201, CVE-2024-50202, CVE-2024-50205, CVE-2024-50208, CVE-2024-50209, CVE-2024-50210, CVE-2024-50218, CVE-2024-50229, CVE-2024-50230, CVE-2024-50233, CVE-2024-50234, CVE-2024-50236, CVE-2024-50237, CVE-2024-50251, CVE-2024-50262, CVE-2024-50264, CVE-2024-50265, CVE-2024-50267, CVE-2024-50268, CVE-2024-50269, CVE-2024-50273, CVE-2024-50278, CVE-2024-50279, CVE-2024-50282, CVE-2024-50287, CVE-2024-50290, CVE-2024-50292, CVE-2024-50295, CVE-2024-50296, CVE-2024-50299, CVE-2024-50301, CVE-2024-50302, CVE-2024-50304, CVE-2024-52332, CVE-2024-53042, CVE-2024-53052, CVE-2024-53057, CVE-2024-53059, CVE-2024-53060, CVE-2024-53061, CVE-2024-53063, CVE-2024-53066, CVE-2024-53096, CVE-2024-53097, CVE-2024-53099, CVE-2024-53101, CVE-2024-53103, CVE-2024-53104, CVE-2024-53112, CVE-2024-53119, CVE-2024-53121, CVE-2024-53124, CVE-2024-53125, CVE-2024-53127, CVE-2024-53130, CVE-2024-53131, CVE-2024-53135, CVE-2024-53136, CVE-2024-53138, CVE-2024-53140, CVE-2024-53141, CVE-2024-53142, CVE-2024-53145, CVE-2024-53146, CVE-2024-53148, CVE-2024-53150, CVE-2024-53155, CVE-2024-53156, CVE-2024-53157, CVE-2024-53158, CVE-2024-53161, CVE-2024-53164, CVE-2024-53171, CVE-2024-53172, CVE-2024-53173, CVE-2024-53174, CVE-2024-53181, CVE-2024-53183, CVE-2024-53184, CVE-2024-53194, CVE-2024-53197, CVE-2024-53198, CVE-2024-53214, CVE-2024-53217, CVE-2024-53226, CVE-2024-53227, CVE-2024-53237, CVE-2024-53239, CVE-2024-53240, CVE-2024-53241, CVE-2024-53680, CVE-2024-53685, CVE-2024-53690, CVE-2024-54031, CVE-2024-55916, CVE-2024-56531, CVE-2024-56532, CVE-2024-56533, CVE-2024-56539, CVE-2024-56548, CVE-2024-56558, CVE-2024-56562, CVE-2024-56567, CVE-2024-56568, CVE-2024-56569, CVE-2024-56570, CVE-2024-56574, CVE-2024-56576, CVE-2024-56581, CVE-2024-56586, CVE-2024-56587, CVE-2024-56589, CVE-2024-56593, CVE-2024-56594, CVE-2024-56595, CVE-2024-56596, CVE-2024-56597, CVE-2024-56598, CVE-2024-56600, CVE-2024-56601, CVE-2024-56602, CVE-2024-56603, CVE-2024-56605, CVE-2024-56606, CVE-2024-56610, CVE-2024-56615, CVE-2024-56616, CVE-2024-56619, CVE-2024-56623, CVE-2024-56629, CVE-2024-56630, CVE-2024-56631, CVE-2024-56633, CVE-2024-56634, CVE-2024-56636, CVE-2024-56637, CVE-2024-56642, CVE-2024-56643, CVE-2024-56644, CVE-2024-56645, CVE-2024-56648, CVE-2024-56650, CVE-2024-56659, CVE-2024-56661, CVE-2024-56662, CVE-2024-56670, CVE-2024-56672, CVE-2024-56681, CVE-2024-56688, CVE-2024-56690, CVE-2024-56691, CVE-2024-56694, CVE-2024-56698, CVE-2024-56700, CVE-2024-56704, CVE-2024-56705, CVE-2024-56716, CVE-2024-56720, CVE-2024-56723, CVE-2024-56724, CVE-2024-56728, CVE-2024-56739, CVE-2024-56741, CVE-2024-56747, CVE-2024-56748, CVE-2024-56754, CVE-2024-56756, CVE-2024-56759, CVE-2024-56763, CVE-2024-56766, CVE-2024-56767, CVE-2024-56769, CVE-2024-56770, CVE-2024-56779, CVE-2024-56780, CVE-2024-57791, CVE-2024-57792, CVE-2024-57802, CVE-2024-57807, CVE-2024-57850, CVE-2024-57874, CVE-2024-57884, CVE-2024-57887, CVE-2024-57889, CVE-2024-57890, CVE-2024-57892, CVE-2024-57896, CVE-2024-57900, CVE-2024-57901, CVE-2024-57902, CVE-2024-57904, CVE-2024-57906, CVE-2024-57907, CVE-2024-57908, CVE-2024-57910, CVE-2024-57911, CVE-2024-57912, CVE-2024-57913, CVE-2024-57922, CVE-2024-57929, CVE-2024-57931, CVE-2024-57938, CVE-2024-57940, CVE-2024-57946, CVE-2024-57948, CVE-2024-57951, CVE-2025-21638, CVE-2025-21639, CVE-2025-21640, CVE-2025-21646, CVE-2025-21648, CVE-2025-21653, CVE-2025-21664, CVE-2025-21666, CVE-2025-21669, CVE-2025-21678, CVE-2025-21683, CVE-2025-21687, CVE-2025-21688, CVE-2025-21689, CVE-2025-21692, CVE-2025-21694, CVE-2025-21697, CVE-2025-21699).
- Security fix: the included package openssh was upgraded from version 1:8.4p1-abomination+4 to version 1:8.4p1-abomination+5 (CVE-2025-26465, CVE-2025-32728).
- Security fix: the included package libgnutls was upgraded from version 3.7.1-5+deb11u6 to version 3.7.1-5+deb11u7 (CVE-2024-12243).
- Security fix: the included package nginx was upgraded from version 1.20.2-1~buster to version 1.26.3-1~bullseye (CVE-2024-7347, CVE-2025-23419).
- Security fix: the included package redis was upgraded from version 5:6.0.16-1+deb11u5 to version 5:6.0.16-1+deb11u6 (CVE-2025-21605).
- Security fix: the included package postgresql-13 was upgraded from version 13.18-0+deb11u1 to version 13.21-0+deb11u1 (CVE-2025-4207, CVE-2025-1094).
- Security fix: the included package libxml2 was upgraded from version 2.9.10+dfsg-6.7+deb11u5 to version 2.9.10+dfsg-6.7+deb11u7 (CVE-2022-49043, CVE-2023-39615, CVE-2023-45322, CVE-2024-25062, CVE-2024-56171, CVE-2025-24928, CVE-2025-27113, CVE-2025-32414, CVE-2025-32415).
- Security fix: the included package libcap2 was upgraded from version 1:2.44-1 to version 1:2.44-1+deb11u1 (CVE-2023-2602, CVE-2023-2603, CVE-2025-1390).
- Security fix: the included package python3.9 was upgraded from version 3.9.2-1+deb11u2 to version 3.9.2-1+deb11u3 (CVE-2022-0391, CVE-2025-0938, CVE-2025-1795).
- Security fix: the included package libxslt was upgraded from version 1.1.34-4+deb11u1 to version 1.1.34-4+deb11u2 (CVE-2024-55549, CVE-2025-24855).
- Security fix: the included package mosquitto was upgraded from version 2.0.11-1+deb11u1 to version 2.0.11-1+deb11u2 (CVE-2024-8376, CVE-2024-3935, CVE-2024-10525).
- Security fix: the included package krb5 was upgraded from version 1.18.3-6+deb11u5 to version 1.18.3-6+deb11u7 (CVE-2025-24528).
- Security fix: the included package libtasn was upgraded from version 4.16.0-2+deb11u1 to version 4.16.0-2+deb11u2 (CVE-2024-12133).
- Security fix: the included package open-vm-tools was upgraded from version 4.16.0-2+deb11u1 to version 4.16.0-2+deb11u2 (CVE-2024-12133).
- Security fix: for virtual appliances, the included package open-vm-tools was upgraded from version 2:11.2.5-2+deb11u3 to version 2:11.2.5-2+deb11u4 (CVE-2025-22247).
- Security fix: for the virtual appliance models Greenbone Enterprise EXA, PETA, TERA and DECA, the included package openvpn was upgraded from version 2.5.1-3 to version 2.5.1-3+deb11u1 (CVE-2022-0547, CVE-2024-5594).
- Minor bug fix: an error was fixed where support packages did not include all expected Postgres debug information (#GOS-2190).
- Minor bug fix: an error was fixed where the console start screen of a Greenbone Enterprise 25V claimed that a web interface was available, even though this model does not have a web interface (#GOS-2092).
- Vulnerability Management:
- Minor improvement: the included appliance manual was updated to the current version from 2025-05-27 (#PR-1271).
- Vulnerability Scanning:
- Minor bug fix: an error was fixed where the IP address was missing in open_sock_tcp log messages of the scanner (#SC-1313).
22.04.27 (2025-02-03):
Note: An upgrade to this version requires a reboot of the system.
- Greenbone OS:
- Extension: the upgrade path to the next major GOS release – GOS 24.10 – has been unlocked for all supported Greenbone Enterprise Appliance models. Several requirements apply, for details see the GOS 24.10 release notes and user manual (#GOS-1803).
- Status: the models Greenbone Enterprise 150, 400 R1, 450 R1, 600 R1, 650 R1, 5300 and 6400 were set to “end-of-life”. They will be retired in the future together with GOS 22.04 and the upgrade path to GOS 24.10 is not supported on these models. Please check which Greenbone Enterprise Appliance models are supported with future GOS versions on https://www.greenbone.net/en/roadmap-lifecycle/ or contact our Sales Team directly to inquire about upgrade possibilities: sales@greenbone.net | +49-541-760278-20 (#GOS-2052).
- Status: the former “Greenbone Enterprise TRIAL” virtual appliance has been renamed to “Greenbone Free” in the web interface (#GOS-2019).
- Improvement: the packages gvm-tools and python-gvm included in GOS were updated to version 25.1.0 (#PR-1089).
- Security fix: the included package rsync was upgraded from version 3.2.3-4+deb11u1 to version 3.2.3-4+deb11u3 (CVE-2024-12085, CVE-2024-12086, CVE-2024-12087, CVE-2024-12088, CVE-2024-12747).
- Security fix: the included package redis was upgraded from version 5:6.0.16-1+deb11u4 to version 5:6.0.16-1+deb11u5 (CVE-2023-28856, CVE-2024-46981).
- Minor improvement: the log message for a failed master-sensor feed push was refined (#GOS-2012).
- Vulnerability Management:
- Improvement: the configurable reports feature has been added to GOS 22.04 (#GOS-2008).
- Minor improvement: the included appliance manual was updated to the current version from 2025-01-27 (#PR-1087).
22.04.26 (2024-12-05):
Note: An upgrade to this version requires a reboot of the system for hardware appliances.
- Greenbone OS:
- Improvement: the included package gvm-tools was updated to version 24.12.0 and the included package python-gvm was updated to version 24.11.0 (#PR-992).
- Improvement: the feed cache volume group size has been increased to 24 GB for the Greenbone Enterprise 6500 R1/5400 R1 appliance models (#GOS-2022).
- Improvement: the GOS state variables sshd_ciphers, sshd_hostkey_algorithms, sshd_kex_algorithms, sshd_macs and sshd_pubkey_accepted_keytypes were added, allowing the persistent customization of the algorithms and ciphers used by the sshd server included in GOS via the GOS shell (#PP-381, #GOS-2004, #GS-6814).
- Improvement: the GOS state variable max_concurrent_scan_updates was added, controlling the number of scan updates that can run at the same time. Per default the number is not limited, matching the behavior of previous GOS versions. The value may be adjusted via the GOS shell for performance tuning reasons (#GOS-1954).
- Improvement: the GOS state variable min_mem_feed_update was added, controlling the minimum memory in Mebibyte (MiB) that must be available for feed updates. Feed updates are skipped if less physical memory is available. Per default no limit is set and feed updates are never skipped, matching the behavior of previous GOS versions. The number may be adjusted via the GOS shell for performance tuning reasons (#GOS-1917).
- Security fix: the included package openssl was upgraded from version 1.1.1w-0+deb11u1 to version 1.1.1w-0+deb11u2 (CVE-2023-5678, CVE-2024-0727, CVE-2024-2511, CVE-2024-4741, CVE-2024-5535, CVE-2024-9143).
- Security fix: the included package postgresql-13 was upgraded from version 13.16-0+deb11u1 to version 13.17-0+deb11u1 (CVE-2024-10976, CVE-2024-10977, CVE-2024-10978, CVE-2024-10979).
- Security fix: the included package libarchive was upgraded from version 3.4.3-2+deb11u1 to version 3.4.3-2+deb11u2 (CVE-2021-36976, CVE-2022-26280, CVE-2022-36227, CVE-2024-20696).
- Security fix: the included package glib2.0 was upgraded from version 2.66.8-1+deb11u4 to version 2.66.8-1+deb11u5 (CVE-2024-52533).
- Security fix: the included package python3.9 was upgraded from version 3.9.2-1 to version 3.9.2-1+deb11u2 (CVE-2015-20107, CVE-2020-10735, CVE-2021-28861, CVE-2021-29921, CVE-2021-3426, CVE-2021-3733, CVE-2021-3737, CVE-2021-4189, CVE-2022-42919, CVE-2022-45061, CVE-2023-24329, CVE-2023-27043, CVE-2023-40217, CVE-2023-6597, CVE-2024-0397, CVE-2024-0450, CVE-2024-11168, CVE-2024-4032, CVE-2024-6232, CVE-2024-6923, CVE-2024-7592, CVE-2024-8088, CVE-2024-9287).
- Security fix: the included package redis was upgraded from version 5:6.0.16-1+deb11u2 to version 5:6.0.16-1+deb11u4 (CVE-2022-35977, CVE-2024-31228).
- Security fix: the included package dnsmasq was upgraded from version 2.85-1 to version 2.85-1+deb11u1 (CVE-2022-0934, CVE-2023-28450, CVE-2023-50387, CVE-2023-50868).
- Security fix: the included package ansible was upgraded from version 2.10.7+merged+base+2.10.17+dfsg-0+deb11u1 to version 2.10.7+merged+base+2.10.17+dfsg-0+deb11u2 (CVE-2024-8775, CVE-2024-9902).
- Security fix: the included package curl was upgraded from version 7.74.0-1.3+deb11u13 to version 7.74.0-1.3+deb11u14 (CVE-2024-8096).
- Minor improvement: the configuration files and system logs of the Postfix mail server used by GOS are now included when generating a GOS support package (#GOS-2045).
- Minor improvement: SMTP and GMP passwords could erroneously be present in GOS support packages. Both are now explicitly excluded when generating a GOS support package (#GOS-2042).
- Vulnerability Management:
- Minor improvement: the included appliance manual was updated to the current version from 2024-12-03 (#PR-993).
22.04.25 (2024-11-05):
- Greenbone OS:
- Bug fix: an error was fixed where trying to open the Maintenance menu on the appliance models Greenbone Enterprise 5400 R1/6500 R1 caused the menu to crash (#GOS-1993, #GS-6924, #GS-6939).
- Bug fix: an error was fixed where uploading a beaming image sometimes caused the GOS administration menu to crash instead of showing an appropriate message (#GOS-1976, #GOS-1992, #GS-6914).
- Bug fix: an error was fixed where an unreachable sensor in a master-sensor setup with multiple sensors stopped the feed push to subsequent sensors as well (#GOS-1978, #GS-6802).
- Bug fix: an error was fixed where deselecting all SSL protocols for the HTTPS connection of the web interface caused the GOS administration menu to crash (#GOS-1952).
- Bug fix: an error was fixed where the switch release from GOS 21.04 to GOS 22.04 failed during the installation of the package libopenvas-misc23 (#GOS-1990).
- Vulnerability Management:
- Minor improvement: the included appliance manual was updated to the current version from 2024-10-29 (#PR-972).
22.04.24 (2024-10-09):
- Greenbone OS:
- Major bug fix: an error was fixed where an upgrade to the previous GOS version 22.04.23 changed the apt configuration, which removed packages marked as optional/recommended. Since the package cryptsetup-initramfs, which is responsible for unlocking the CryptDisk during the boot process, has only been changed to be manually installed during installation of GOS 22.04, it was just “recommended” on every hardware appliance installed before GOS 22.04, and thus removed with GOS 22.04.23. For some appliances, the removal of the package could lead to the appliance not booting correctly anymore after the upgrade to GOS 22.04.23 (#GOS-1981, #GS-6596, #GS-6851, #GS-6853, #GS-6865, #GS-6866, #GS-6868, #GS-6869, #GS-6825, #GS-6862, #GS-6857).
- Vulnerability Management:
- Minor improvement: the included appliance manual was updated to the current version from 2024-10-09 (#PR-965).
22.04.23 (2024-10-07):
Note: An upgrade to this version requires a reboot of the system.
- Greenbone OS:
- Improvement: the RAM limit was increased to 24 GB for the appliance model 5400 R2, 14 GB for the appliance models DECA and TERA, 12 GB for the appliance models CENO and ONE, and 8 GB for the appliance models 25V and 35 (#GOS-1916).
Note: For virtual appliances, manual adjustments are required for the change to take effect. Further information and instructions can be found here.
- Improvement: the disk size for all virtual appliances was extended to 500 GB (#GOS-1788).
Note: Manual adjustments are required for the change to take effect. Further information and instructions can be found here.
- Improvement: the size of the feed partition was increased to 24 GB for the appliance models CENO, DECA, TERA, PETA, EXA, ONE, 25V, 400 R1/450 R1/600 R1/650 R1 and 5400 R1/6500 R1 (#GOS-1793).
Note: Manual adjustments are required for the change to take effect. Further information and instructions can be found here.
- Improvement: the size of the root partition was increased to 55 GB for the appliance models 150 and 35 (#GOS-1793).
Note: Manual adjustments are required for the change to take effect. Further information and instructions can be found here.
- Improvement: the packages gvm-tools and python-gvm included in GOS were updated to version 24.8.0 (#PR-949).
- Security fix: the Linux kernel was upgraded from version 5.10.222-greenbone1 to version 5.10.225-greenbone1 for hardware appliances and from version 5.10.221-1 to version 5.10.223-1 for virtual appliances (CVE-2022-48666, CVE-2024-36484, CVE-2024-36901, CVE-2024-36938, CVE-2024-39487, CVE-2024-40947, CVE-2024-41007, CVE-2024-41009, CVE-2024-41012, CVE-2024-41015, CVE-2024-41017, CVE-2024-41020, CVE-2024-41022, CVE-2024-41034, CVE-2024-41035, CVE-2024-41040, CVE-2024-41041, CVE-2024-41044, CVE-2024-41046, CVE-2024-41049, CVE-2024-41055, CVE-2024-41059, CVE-2024-41063, CVE-2024-41064, CVE-2024-41065, CVE-2024-41068, CVE-2024-41070, CVE-2024-41072, CVE-2024-41077, CVE-2024-41078, CVE-2024-41081, CVE-2024-41090, CVE-2024-41091, CVE-2024-42101, CVE-2024-42102, CVE-2024-42104, CVE-2024-42105, CVE-2024-42106, CVE-2024-42115, CVE-2024-42119, CVE-2024-42120, CVE-2024-42121, CVE-2024-42124, CVE-2024-42127, CVE-2024-42131, CVE-2024-42137, CVE-2024-42143, CVE-2024-42145, CVE-2024-42148, CVE-2024-42152, CVE-2024-42153, CVE-2024-42154, CVE-2024-42157, CVE-2024-42161, CVE-2024-42223, CVE-2024-42224, CVE-2024-42229, CVE-2024-42232, CVE-2024-42236, CVE-2024-42244, CVE-2024-42247).
- Security fix: the included package libexpat1 was upgraded from version 2.2.10-2+deb11u5 to version 2.2.10-2+deb11u6 (CVE-2023-52425, CVE-2024-45490, CVE-2024-45491, CVE-2024-45492).
- Security fix: the included package postgresql-13 was upgraded from version 13.15-0+deb11u1 to version 13.16-0+deb11u1 (CVE-2024-7348).
- Security fix: the Intel microcode of the Greenbone Enterprise 650 R2/600 R2/450 R2/400 R2 appliance models was upgraded to the current version from 2024-08-19 (#GOS-1935).
- Bug fix: during GOS upgrades, system services are regularly stopped and restarted. This led to situations where the Postgres database was shut down before the gvmd service. Since the gvmd service depends on a working connection to Postgres, this could cause SQL error messages. gvmd is now stopped before Postgres during GOS upgrades (#GOS-1923).
- Bug fix: an error was fixed where feed updates permanently took up SWAP storage space, which could result in a performance decrease in the long run (#GOS-1911, #GS-3661, #GS-5113).
- Vulnerability Management:
- Minor improvement: the included appliance manual was updated to the current version from 2024-09-24 (#PR-948).
- Bug fix: an error was fixed where date and time information was displayed in an incorrect format on the web interface when the language was set to German (#GEA-667).
- Bug fix: an error was fixed where too many simultaneous user logins to the web interface could result in database deadlocks (#GEA-655).
- Bug fix: an error was fixed where indexes for VTs could be missing after feed updates (#GEA-579).
- Bug fix: an error was fixed where the HTML hexadecimal code of the special character
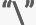 in a TLS certificate resulted in report exports to fail (#GEA-607, #GS-6328).
in a TLS certificate resulted in report exports to fail (#GEA-607, #GS-6328).
- Bug fix: an error was fixed where the custom SSH port set in the Advanced Task Wizard was ignored (#GEA-668, #GS-6609).
- Minor bug fix: an error was fixed where some texts on the page CVSS Calculator were not translated into German (#GEA-654).
- Vulnerability Scanning:
- Bug fix: an error was fixed where the versions of Debian packages were parsed incorrectly, leading to false-positive results for the MariaDB Server product for example (#SC-1121).
22.04.22 (2024-07-31):
- Greenbone OS:
- Improvement: the packages gvm-tools and python-gvm included in GOS were updated to version 24.7.0 (#PR-881).
- Change: the Greenbone Community Feed can no longer be downloaded on the Greenbone Basic Appliance (#GOS-1899).
- Change: the setup wizard dialog for adding a Greenbone Enterprise subscription key was updated for the Greenbone Basic Appliance (#GOS-1919).
- Change: the dialog for deleting a Greenbone Enterprise Feed subscription key was changed on the Greenbone Basic Appliance to reflect the change that the Greenbone Community Feed can no longer be downloaded (#GOS-1920).
- Security fix: the Linux kernel was upgraded from version 5.10.216-greenbone1 to version 5.10.222-greenbone1 for hardware appliances and from version 5.10.216-1 to version 5.10.221-1 for virtual appliances (CVE-2021-4440, CVE-2022-48655, CVE-2023-52585, CVE-2023-52882, CVE-2024-26900, CVE-2024-27398, CVE-2024-27399, CVE-2024-27401, CVE-2024-35848, CVE-2024-35947, CVE-2024-36017, CVE-2024-36031, CVE-2024-36883, CVE-2024-36886, CVE-2024-36889, CVE-2024-36902, CVE-2024-36904, CVE-2024-36905, CVE-2024-36916, CVE-2024-36919, CVE-2024-36929, CVE-2024-36933, CVE-2024-36934, CVE-2024-36939, CVE-2024-36940, CVE-2024-36941, CVE-2024-36946, CVE-2024-36950, CVE-2024-36953, CVE-2024-36954, CVE-2024-36957, CVE-2024-36959, CVE-2022-43945, CVE-2022-48772, CVE-2024-25741, CVE-2024-26629, CVE-2024-27019, CVE-2024-31076, CVE-2024-33621, CVE-2024-33847, CVE-2024-34027, CVE-2024-35247, CVE-2024-36014, CVE-2024-36015, CVE-2024-36016, CVE-2024-36270, CVE-2024-36286, CVE-2024-36288, CVE-2024-36489, CVE-2024-36894, CVE-2024-36971, CVE-2024-36974, CVE-2024-36978, CVE-2024-37078, CVE-2024-37353, CVE-2024-37356, CVE-2024-38381, CVE-2024-38546, CVE-2024-38547, CVE-2024-38548, CVE-2024-38549, CVE-2024-38552, CVE-2024-38555, CVE-2024-38558, CVE-2024-38559, CVE-2024-38560, CVE-2024-38565, CVE-2024-38567, CVE-2024-38578, CVE-2024-38579, CVE-2024-38582, CVE-2024-38583, CVE-2024-38586, CVE-2024-38587, CVE-2024-38589, CVE-2024-38590, CVE-2024-38596, CVE-2024-38597, CVE-2024-38598, CVE-2024-38599, CVE-2024-38601, CVE-2024-38605, CVE-2024-38607, CVE-2024-38612, CVE-2024-38613, CVE-2024-38615, CVE-2024-38618, CVE-2024-38619, CVE-2024-38621, CVE-2024-38627, CVE-2024-38633, CVE-2024-38634, CVE-2024-38635, CVE-2024-38637, CVE-2024-38659, CVE-2024-38661, CVE-2024-38662, CVE-2024-38780, CVE-2024-39276, CVE-2024-39292, CVE-2024-39301, CVE-2024-39467, CVE-2024-39468, CVE-2024-39469, CVE-2024-39471, CVE-2024-39475, CVE-2024-39476, CVE-2024-39480, CVE-2024-39482, CVE-2024-39484, CVE-2024-39488, CVE-2024-39489, CVE-2024-39493, CVE-2024-39495, CVE-2024-39499, CVE-2024-39501, CVE-2024-39502, CVE-2024-39503, CVE-2024-39505, CVE-2024-39506, CVE-2024-39509, CVE-2024-40901, CVE-2024-40902, CVE-2024-40904, CVE-2024-40905, CVE-2024-40912, CVE-2024-40916, CVE-2024-40929, CVE-2024-40931, CVE-2024-40932, CVE-2024-40934, CVE-2024-40941, CVE-2024-40942, CVE-2024-40943, CVE-2024-40945, CVE-2024-40958, CVE-2024-40959, CVE-2024-40960, CVE-2024-40961, CVE-2024-40963, CVE-2024-40968, CVE-2024-40971, CVE-2024-40974, CVE-2024-40976, CVE-2024-40978, CVE-2024-40980, CVE-2024-40981, CVE-2024-40983, CVE-2024-40984, CVE-2024-40987, CVE-2024-40988, CVE-2024-40990, CVE-2024-40993, CVE-2024-40995, CVE-2024-41000, CVE-2024-41004, CVE-2024-41005, CVE-2024-41006).
- Minor improvement: mere recommended packages are now uninstalled if the GOS upgrade action removes packages that were automatically installed to satisfy dependencies for other packages, but are now no longer needed (#GOS-1806, #GOS-1807).
- Minor improvement: on the About page on the web interface, the copyright year was updated to 2024 (#GOS-1832).
- Vulnerability Management:
- Improvement: an in-progress indicator was added to the
 (“Delete”) action on the pages Reports, Hosts, Operating Systems and TLS Certificates (#GEA-327).
(“Delete”) action on the pages Reports, Hosts, Operating Systems and TLS Certificates (#GEA-327).
- Improvement: the page CVSS Calculator now contains a calculator for CVSS v4 in addition to the calculators for CVSS v2 and CVSS v3 (#GEA-532).
- Improvement: the performance of CVE feed updates was improved (#GEA-557).
- Bug fix: an error was fixed where duplicate results generated during scans were not filtered out before adding them to a report (#GEA-525, #GS-5962).
- Bug fix: an error was fixed where using the “&” character in the comment field of a target resulted in an internal error and in the target not being created (#GEA-562, #GS-6211).
- Bug fix: an error was fixed where schedules with a fixed end date could sometimes not be created (#GEA-523).
- Bug fix: an error was fixed where the dates selected for a schedule were sometimes not correctly applied (#GEA-610).
- Bug fix: an error was fixed where searching for specific strings on the NVT list page resulted in an error (#GEA-448).
- Minor improvement: the performance of the Trashcan page was improved (#GEA-457).
- Minor improvement: various small changes, from memory leak fixes to code cleanups and improvements were implemented for the gvmd service (#GEA-585).
- Minor improvement: the included appliance manual was updated to the current version from 2024-07-29 (#PR-918).
- Vulnerability Scanning:
- Minor improvement: the compatibility of the ICMP Ping alive test with target systems not following the RFC 792 specification was improved (#SC-1064).
22.04.21 (2024-06-03):
- Greenbone OS:
- Extension: the new Greenbone Enterprise 6500 R2 and Greenbone Enterprise 5400 R2 appliance models were added (#GOS-1625).
- Security fix: the included package glib2.0 was upgraded from version 2.66.8-1+deb11u1 to version 2.66.8-1+deb11u3 (CVE-2024-34397).
- Bug fix: an error was fixed where the ospd-openvas service could not connect to the mosquitto service after moving network interfaces from the Management namespace to the Scan1 namespace (#GOS-1863).
- Minor improvement: an anonymized count of the number of hosts that were scanned within the last 90 days has been added to the GOS support package for statistical evaluations (#GOS-1839).
- Minor bug fix: an error was fixed where the most current run of the GOS selfcheck was not logged in the GOS support package (#GOS-1854).
- Minor bug fix: an error was fixed where the raid-rebuild script showed a syntax warning (#GOS-1744).
- Vulnerability Management:
- Minor improvement: the included appliance manual was updated to the current version from 2024-05-29 (#PR-875).
22.04.20 (2024-05-13):
- Greenbone OS:
- Security fix: the Linux kernel was upgraded from version 5.10.209-greenbone1 to version 5.10.216-greenbone1 for hardware appliances and from version 5.10.209-2 to version 5.10.216-1 for virtual appliances (CVE-2023-28746, CVE-2023-47233, CVE-2023-52429, CVE-2023-52434, CVE-2023-52435, CVE-2023-52447, CVE-2023-52458, CVE-2023-52482, CVE-2023-52486, CVE-2023-52488, CVE-2023-52489, CVE-2023-52491, CVE-2023-52492, CVE-2023-52493, CVE-2023-52497, CVE-2023-52498, CVE-2023-52583, CVE-2023-52587, CVE-2023-52594, CVE-2023-52595, CVE-2023-52597, CVE-2023-52598, CVE-2023-52599, CVE-2023-52600, CVE-2023-52601, CVE-2023-52602, CVE-2023-52603, CVE-2023-52604, CVE-2023-52606, CVE-2023-52607, CVE-2023-52614, CVE-2023-52615, CVE-2023-52616, CVE-2023-52617, CVE-2023-52618, CVE-2023-52619, CVE-2023-52620, CVE-2023-52622, CVE-2023-52623, CVE-2023-52627, CVE-2023-52635, CVE-2023-52637, CVE-2023-52642, CVE-2023-52644, CVE-2023-52650, CVE-2023-6270, CVE-2023-7042, CVE-2024-0340, CVE-2024-0565, CVE-2024-0607, CVE-2024-0841, CVE-2024-1151, CVE-2024-22099, CVE-2024-23849, CVE-2024-23850, CVE-2024-23851, CVE-2024-24857, CVE-2024-24858, CVE-2024-24861, CVE-2024-26581, CVE-2024-26593, CVE-2024-26600, CVE-2024-26601, CVE-2024-26602, CVE-2024-26606, CVE-2024-26610, CVE-2024-26614, CVE-2024-26615, CVE-2024-26622, CVE-2024-26625, CVE-2024-26627, CVE-2024-26635, CVE-2024-26636, CVE-2024-26640, CVE-2024-26641, CVE-2024-26642, CVE-2024-26643, CVE-2024-26644, CVE-2024-26645, CVE-2024-26651, CVE-2024-26654, CVE-2024-26659, CVE-2024-26663, CVE-2024-26664, CVE-2024-26665, CVE-2024-26671, CVE-2024-26673, CVE-2024-26675, CVE-2024-26679, CVE-2024-26684, CVE-2024-26685, CVE-2024-26687, CVE-2024-26688, CVE-2024-26689, CVE-2024-26695, CVE-2024-26696, CVE-2024-26697, CVE-2024-26698, CVE-2024-26702, CVE-2024-26704, CVE-2024-26707, CVE-2024-26712, CVE-2024-26720, CVE-2024-26722, CVE-2024-26727, CVE-2024-26733, CVE-2024-26735, CVE-2024-26736, CVE-2024-26743, CVE-2024-26744, CVE-2024-26747, CVE-2024-26748, CVE-2024-26749, CVE-2024-26751, CVE-2024-26752, CVE-2024-26753, CVE-2024-26754, CVE-2024-26763, CVE-2024-26764, CVE-2024-26766, CVE-2024-26771, CVE-2024-26772, CVE-2024-26773, CVE-2024-26776, CVE-2024-26777, CVE-2024-26778, CVE-2024-26779, CVE-2024-26781, CVE-2024-26782, CVE-2024-26787, CVE-2024-26788, CVE-2024-26790, CVE-2024-26791, CVE-2024-26793, CVE-2024-26795, CVE-2024-26801, CVE-2024-26804, CVE-2024-26805, CVE-2024-26808, CVE-2024-26809, CVE-2024-26810, CVE-2024-26812, CVE-2024-26813, CVE-2024-26814, CVE-2024-26816, CVE-2024-26817, CVE-2024-26820, CVE-2024-26825, CVE-2024-26833, CVE-2024-26835, CVE-2024-26839, CVE-2024-26840, CVE-2024-26843, CVE-2024-26845, CVE-2024-26846, CVE-2024-26848, CVE-2024-26851, CVE-2024-26852, CVE-2024-26855, CVE-2024-26857, CVE-2024-26859, CVE-2024-26861, CVE-2024-26862, CVE-2024-26863, CVE-2024-26870, CVE-2024-26872, CVE-2024-26874, CVE-2024-26875, CVE-2024-26877, CVE-2024-26878, CVE-2024-26880, CVE-2024-26882, CVE-2024-26883, CVE-2024-26884, CVE-2024-26885, CVE-2024-26889, CVE-2024-26891, CVE-2024-26894, CVE-2024-26895, CVE-2024-26897, CVE-2024-26898, CVE-2024-26901, CVE-2024-26903, CVE-2024-26906, CVE-2024-26907, CVE-2024-26910, CVE-2024-26917, CVE-2024-26920, CVE-2024-26922, CVE-2024-26923, CVE-2024-26924, CVE-2024-26925, CVE-2024-26926, CVE-2024-26931, CVE-2024-26934, CVE-2024-26935, CVE-2024-26937, CVE-2024-26950, CVE-2024-26951, CVE-2024-26955, CVE-2024-26956, CVE-2024-26957, CVE-2024-26958, CVE-2024-26960, CVE-2024-26961, CVE-2024-26965, CVE-2024-26966, CVE-2024-26969, CVE-2024-26970, CVE-2024-26973, CVE-2024-26974, CVE-2024-26976, CVE-2024-26978, CVE-2024-26979, CVE-2024-26981, CVE-2024-26984, CVE-2024-26988, CVE-2024-26993, CVE-2024-26994, CVE-2024-26997, CVE-2024-26999, CVE-2024-27000, CVE-2024-27001, CVE-2024-27004, CVE-2024-27008, CVE-2024-27013, CVE-2024-27020, CVE-2024-27024, CVE-2024-27025, CVE-2024-27028, CVE-2024-27030, CVE-2024-27038, CVE-2024-27043, CVE-2024-27044, CVE-2024-27045, CVE-2024-27046, CVE-2024-27047, CVE-2024-27051, CVE-2024-27052, CVE-2024-27053, CVE-2024-27059, CVE-2024-27065, CVE-2024-27073, CVE-2024-27074, CVE-2024-27075, CVE-2024-27076, CVE-2024-27077, CVE-2024-27078, CVE-2024-27388, CVE-2024-27437).
- Security fix: the included package glibc was upgraded from version 2.31-13+deb11u8 to version 2.31-13+deb11u10 (CVE-2024-2961, CVE-2024-33599, CVE-2024-33600, CVE-2024-33601, CVE-2024-33602).
- Security fix: the included package util-linux was upgraded from version 2.36.1-8+deb11u1 to version 2.36.1-8+deb11u2 (CVE-2024-28085).
- Security fix: the included package less was upgraded from version 551-2 to version 551-2+deb11u2 (CVE-2022-48624, CVE-2024-32487).
- Vulnerability Management:
- Major bug fix: an error was fixed where, if an alert with compose data but with no filter selected was added to a task, the task would be interrupted when the alert was triggered (#GEA-526, #GS-5859, #GS-6002, #GS-6022, #GS-6023, #GS-6025, #GS-6046, #GS-6055, #GS-6064, #GS-6067, #GS-6078, #GS-6103, #GS-6112, #GS-6113, #GS-6116, #GS-6118, #GS-6120, #GS-6123, #GS-6130, #GS-6137, #GS-6138, #GS-6147, #GS-6148, #GS-6159, #GS-6166, #GS-6170, #GS-6178, #GS-6197).
- Bug fix: an error was fixed where the appliance could sometimes become unresponsive when filtering results or refreshing the authentication (#GEA-505, #GS-5903).
- Bug fix: an error was fixed where it was not possible to delete a user without selecting an inheriting user (#GEA-542).
- Bug fix: an error was fixed where the location “package” was not accepted for the configuration of overrides and notes (#GEA-534, #GS-6039).
- Minor improvement: the info messages used to identify duplicate results and duplicate host details were changed to debug messages (#GEA-509).
- Minor improvement: the included appliance manual was updated to the current version from 2024-05-07 (#PR-867).
22.04.19 (2024-04-03):
- Greenbone OS:
- Extension: the new Greenbone BASIC Appliance model was added (#GOS-1727).
- Improvement: the package gvm-tools included in GOS was updated to version 24.3.0 (#PR-834).
- Security fix: as a hardening measure, the MAC algorithms “umac-64@openssh.com” and “hmac-sha1” have been deactivated for the sshd server used by GOS. One of the following MAC algorithms now has to be used to connect to GOS via the SSH protocol: “hmac-sha2-512-etm@openssh.com”, “hmac-sha2-256-etm@openssh.com”, “hmac-sha2-512” or “hmac-sha2-256” (#GOS-1786, #GS-5677, #GS-5845).
- Security fix: the included package samba was upgraded from version 2:4.13.13+dfsg-1~deb11u5 to version 2:4.13.13+dfsg-1~deb11u6 (CVE-2022-2127, CVE-2022-3437, CVE-2023-34966, CVE-2023-34967, CVE-2023-34968, CVE-2023-4091).
- Vulnerability Management:
- Improvement: the included appliance manual was updated to the current version from 2024-03-25. The design and layout of the manual was improved through clearer tables of contents on the side and a light-dark-theme option (#PR-847).
- Improvement: the XML parser used by the gvmd service to process CPE data was improved, reducing the amount of memory used during feed updates (#GEA-488).
- Improvement: the XML parser used by the gvmd service to process CVE data was improved, reducing the amount of memory used during feed updates (#GEA-498).
- Bug fix: a memory leak was fixed for the processing of CPE and CVE data by the gvmd service, significantly reducing peak memory usage during feed updates (#GEA-490).
- Bug fix: an error was fixed where the gvmd service could potentially be stuck in a loop during feed updates because of malformed CPE data (#GEA-419).
- Bug fix: an error was fixed where the gvmd service could potentially be stuck in a loop during feed updates because of malformed CVE data (#GEA-512).
- Bug fix: an error was fixed where delta reports were broken if one of the reports had multiple results that were the same except for the description (#GEA-471).
- Bug fix: an error was fixed where delta reports could not be exported in the formats “GSR HTML”, “GSR PDF”, “PDF”, “TXT”, “Vulnerability Report HTML” and “Vulnerability Report PDF” (#GEA-442, #GS-5575).
- Bug fix: an error was fixed where configuring a vulnerability scan to check for file checksum patterns did not work as expected (#GEA-450).
- Bug fix: an error was fixed where the Exclude Hosts setting in a CVE scan was ignored (#GEA-463, #GS-5674).
- Bug fix: an error was fixed where, if an alert with compose data but with no filter selected was added to a task, reports sent via the alert would be incomplete (#GEA-504).
- Bug fix: an error was fixed where alerts using the method TippingPoint SMS were not triggered after the scan was finished (#GEA-472, #GS-5706).
- Vulnerability Scanning:
- Improvement: support for the Network Configuration Protocol (NETCONF) over SSH was added (#SC-1019).
- Bug fix: an error was fixed where using the Exclude Hosts setting while scanning vhosts could cause the scan to be interrupted (#SC-964).
- Minor improvement: the parsing of “$Date” strings in vulnerability tests was deprecated, and a warning will be logged if such vulnerability tests are loaded. The vulnerability tests in the current versions of the Greenbone Enterprise Feed and the Greenbone Community Feed have been updated accordingly (#SC-903).
22.04.18 (2024-02-20):
Note: An upgrade to this version requires a reboot of the system.
- Greenbone OS:
- Improvement: the RAM limit of the appliance model Greenbone Enterprise 400 (revision 1) was increased from 6 GB to 8 GB. A reboot after the upgrade is required for this change to take effect (#GOS-1762).
- Improvement: the expiration dates for the feed signing and support package encryption keys used by GOS have been extended until 2026-12-31 (#GOS-1756, #GOS-1757).
- Security fix: the included package postgresql-13 was upgraded from version 13.13-0+deb11u1 to version 13.14-0+deb11u1 (CVE-2024-0985).
- Security fix: the Linux kernel was upgraded from version 5.10.208-greenbone1 to version 5.10.209-greenbone1 for hardware appliances and from version 5.10.205-2 to version 5.10.209-2 for virtual appliances (CVE-2024-1086).
- Bug fix: NTLM has been deactivated for the use of all e-mail functionality in GOS to prevent problems with some Microsoft Exchange servers (#GOS-1715, #GS-5533).
- Vulnerability Management:
- Major bug fix: an error was fixed where granting read or write permissions for objects to other users did not work as expected (#GEA-477, #GS-5720, #GS-5781).
- Bug fix: an error was fixed where Vulnerability Report PDF and Vulnerability Report HTML reports that were attached to or included in e-mail alerts and for which overrides were active had no contents (#GEA-408, #GEA-482, #GS-5431, #GS-5447, #GS-5530).
- Minor improvement: the included appliance manual was updated to the current version from 2024-02-15 (#PR-823).
22.04.17 (2024-02-01):
- Greenbone OS:
- Major bug fix: an error was fixed where pushing the feed from the master appliance to the sensor appliance in a master-sensor setup resulted in sensor feed synchronization issues (#GOS-1705).
- Improvement: the package gvm-tools and python-gvm included in GOS were updated to version 24.1.0. Note: Due to API changes at least these versions are required to access the GMP API of GOS 22.04.17. (#PR-792).
- Improvement: the processes of creating and importing a beaming image are now system operations. While a system operation is in progress, no other system operation can be started. This is to ensure the integrity and stability of the system (#GOS-1677).
- Security fix: the included package libssh was upgraded from version 0.9.7-0+deb11u1 to version 0.9.8-0+deb11u1 (CVE-2023-48795, CVE-2023-6004, CVE-2023-6918).
- Security fix: the included package curl was upgraded from version 7.74.0-1.3+deb11u10 to version 7.74.0-1.3+deb11u11 (CVE-2023-46218).
- Security fix: the included package openssh was upgraded from version 1:8.4p1-abomination+3 to version 1:8.4p1-5+deb11u3 (CVE-2021-41617, CVE-2023-28531, CVE-2023-48795, CVE-2023-51384, CVE-2023-51385).
- Security fix: the Linux kernel was upgraded from version 5.10.197-1 to version 5.10.205-2 for virtual appliances (CVE-2021-44879, CVE-2023-5178, CVE-2023-5197, CVE-2023-5717, CVE-2023-6121, CVE-2023-6531, CVE-2023-6817, CVE-2023-6931, CVE-2023-6932, CVE-2023-25775, CVE-2023-34324, CVE-2023-35827, CVE-2023-45863, CVE-2023-46813, CVE-2023-46862, CVE-2023-51780, CVE-2023-51781, CVE-2023-51782).
- Security fix: the Linux kernel was upgraded from version 5.10.201-greenbone1 to version 5.10.208-greenbone1 for hardware appliances (CVE-2021-44879, CVE-2023-5178, CVE-2023-5197, CVE-2023-5717, CVE-2023-6121, CVE-2023-6531, CVE-2023-6817, CVE-2023-6931, CVE-2023-6932, CVE-2023-25775, CVE-2023-34324, CVE-2023-35827, CVE-2023-45863, CVE-2023-46813, CVE-2023-46862, CVE-2023-51780, CVE-2023-51781, CVE-2023-51782).
- Bug fix: an error was fixed where formatting a GOS USB backup stick did not work in several cases (#GOS-1714).
- Bug fix: an error was fixed where some links in the feed had the wrong permissions which could lead to pushing the feed from a master appliance to a sensor appliance in a master-sensor setup to fail (#GOS-1708).
- Vulnerability Management:
- Improvement: an option to filter for the compliance status was added to the Results page and to the Results tab of a report. The filter keyword is compliance_levels and the possible values are y (yes/compliant), n (no/not compliant), i (incomplete) and u (undefined) (#GEA-391).
- Improvement: in addition to the IP address, the host name is now displayed in the header of each host section, in the list at the host section beginning, and in the details of the results in the report formats Vulnerability Report PDF and Vulnerability Report HTML (#GEA-378, #GS-3372)
- Improvement: due to improvements the GMP API version has been increased to 22.5. When accessing the GMP API of GOS 22.04.17 via clients, up-to-date, compatible versions have to be used, for example gvm-tools 24.1.0 (#GEA-407).
- Improvement: the performance of loading of a large number of tag resource has been significantly improved (#GEA-380).
- Improvement: the performance of the Results and Vulnerabilities pages was improved for setups with multiple users and large amounts of results (#GEA-385).
- Security fix: the strength of the encryption key for credentials stored in the database has been increased from 2048-bit RSA to 3072-bit RSA. Existing credentials are automatically re-encrypted with the new key when upgrading to GOS 22.04.17 or later (#GOS-1678, #GEA-193).
- Bug fix: an error was fixed where – when deleting a user via the web interface, the command line or the GOS administration menu – no users who inherit the objects of the deleted user could be selected (#GEA-381).
- Bug fix: an error was fixed where the table on the page Vulnerabilities showed the date and time of the newest result instead of the oldest result in the column Oldest Result (#GEA-414).
- Bug fix: an error was fixed where editing VT families of custom compliance policies was not possible (#GEA-415).
- Bug fix: an error was fixed where reports in the report formats CPE and TLS Map where empty when sent via the Test Alert functionality using the method E-mail (#GEA-358).
- Minor improvement: the included appliance manual was updated to the current version from 2024-01-15 (#PR-793).
- Minor improvement: the credential type Client Certificate was retired because it was not used for any type of target, alert or scanner anymore. Existing credentials of this type will not be affected or removed. They can still be accessed, but they are of no use anymore, and can be deleted manually (#GEA-333).
- Minor improvement: the VT families AlmaLinux Local Security Checks and Amazon Linux Local Security Checks are no longer editable when creating or editing a scan configuration (#GEA-387).
- Minor bug fix: an error was fixed where the tool tips showed and linked false filters when hovering over the columns for N/A and 1 in a “by CVSS” diagram (#GEA-370).
22.04.16 (2023-12-04):
- Greenbone OS:
- Improvement: support for limiting the number of simultaneous web sessions for web users was added. The configuration can be found in the GOS menu under Setup > Users > Users > User sessions. By default, no limit is applied, which reflects the behavior of GOS 22.04.15 and earlier (#GOS-1621, #GEA-288, #GS-4982).
- Improvement: the package gvm-tools included in GOS was updated to version 23.11.0 (#PR-753).
- Improvement: the package python-gvm included in GOS was updated to version 23.11.0 (#PR-753).
- Bug fix: an error was fixed where SNMP passphrases containing the character “!” were not working in GOS (#GOS-1623, #GS-4924).
- Security fix: SSL 3.0, TLS 1.0 and TLS 1.1 have been disabled for the remote logging feature of GOS. TLS 1.2 or TLS 1.3 must be used now (#GOS-1613, RFC 7568, RFC 8996).
- Security fix: the included package openssh was upgraded from version 1:8.4p1-abomination+2 to version 1:8.4p1-abomination+3 (CVE-2023-38408).
- Security fix: the included package postgresql-13 was upgraded from version 13.11-0+deb11u1 to version 13.13-0+deb11u1 (CVE-2023-5868, CVE-2023-5869, CVE-2023-5870, CVE-2023-39417).
- Security fix: for virtual appliances, the included package open-vm-tools was upgraded from version 2:11.2.5-2+deb11u2 to version 2:11.2.5-2+deb11u3 (CVE-2023-34058, CVE-2023-34059).
- Minor improvement: an outdated “gsm” reference in the GOS administration menu has been corrected (#GOS-1650).
- Vulnerability Management:
- Major improvement: the delta report functionality was overhauled. Delta reports are no longer dependent on the sorting order of the results, providing a much more intuitive user experience, tool tips have been added to delta reports to show exactly what has changed, e.g., the severity or the quality of detection (QoD), and the performance of generating delta reports was considerably improved (#GEA-271).
- Improvement: scan configurations, report formats, port lists, and compliance policies can now be marked deprecated on the web interface. If a report is exported in a deprecated report format, the downloaded file may be empty or otherwise not suitable for use (#GEA-6).
- Improvement: when viewing TLS certificates of a scan report, the certificates’ Subject DN can now be clicked to show more information about the certificate (#GEA-308).
- Improvement: the new task status Processing is now also supported for container tasks. It is displayed there after the report upload is completed, indicating that the appliance is busy processing data in the backend (#GEA-353).
- Improvement: the performance when editing scan configurations or compliance policies in the web interface was further improved (#GEA-341).
- Improvement: the performance when paging through list pages with “Created” or “Modified” dates on the web interface, e.g., the “SecInfo > NVTs” page, was improved (#GEA-362).
- Bug fix: an error was fixed where CVE scans did not detect the expected CVEs due to incorrect case sensitivity for CPEs (#GEA-8, #GS-2451).
- Bug fix: an error was fixed where it was not possible to link a large number of tags to an object because the corresponding menu became unusable. Note that the menu is still limited to a maximum of 200 tags. If more tags are to be linked to an object, the “Apply to …” functionality on list pages can be used (#GEA-251, #GS-908).
- Bug fix: incorrectly encoded TLS certificate data in the database, which could cause errors when viewing certificates on the web interface, is now cleaned up when upgrading to GOS 22.04.16 or later. Note that with the current GOS versions, the recurrence of such incorrectly encoded data should no longer occur (#GEA-3, #GOS-1648, #GS-2337).
- Minor improvement: the included appliance manual was updated to the current version from 2023-11-28 (#PR-780).
- Minor improvement: the drop-down menu used in various dialogs on the web interface can now also be oriented upwards, if there is not enough free space at the bottom to display the entire content (#GEA-303).
- Minor improvement: the Start button (
 ) for scan tasks on the web interface is now inactive if a schedule with an end date is configured for the task. Trying to start such tasks was never supported, and tasks would stop at 0 % progress in this case (#GEA-379, #GS-699).
) for scan tasks on the web interface is now inactive if a schedule with an end date is configured for the task. Trying to start such tasks was never supported, and tasks would stop at 0 % progress in this case (#GEA-379, #GS-699).
- Minor improvement: the informational message “The reports database is currently busy, please try again later” was added for cases where scan reports could not be deleted due to an ongoing database lock (#GEA-327, #GS-2073).
- Minor improvement: when editing scan configurations or compliance policies, it is no longer possible to edit individual vulnerability tests for various vulnerability test families that should only be selected as a whole (#GEA-331).
- Minor improvement: the report format ITG was deprecated (#GEA-6, #GS-586, #GS-4121).
- Minor improvement: the CVSS ranges for dashboard diagrams were improved (#GEA-266).
- Minor improvement: the error message shown when trying to create an invalid credential was improved to be more specific (#GEA-341).
- Minor improvement: the error message shown when the gvmd database cannot be migrated was improved to be more specific (#GEA-362).
- Minor improvement: when using the GMP API, “creation_time” and “modification_time” information is now returned in the user’s local time zone instead of UTC (#GEA-362).
- Minor bug fix: an error was fixed where duplicate “Timeout” NVT preferences could appear when editing scan configurations or compliance policies (#GEA-362).
- Minor bug fix: an error was fixed where two German translations – in the “Compose” dialog when creating or editing an alert, and on the “TLS Certificates” list page – were missing (#GEA-332, #GEA-334).
- Vulnerability Scanning:
- Bug fix: an error was fixed where vulnerability scans were interrupted when the target setting “Reverse Lookup Only” was set to “Yes” and a host was excluded from the target (#SC-929, #GS-5146).
- Bug fix: an error was fixed where the Boreas alive scanner performed alive tests even if the alive test option “Consider Alive” was used (#SC-934).
22.04.15 (2023-10-17):
- Greenbone OS:
- Improvement: the package gvm-tools included in GOS was updated to version 23.9.0 (#PR-740).
- Bug fix: an error was fixed where monitoring the HDD via SNMPv3 sometimes failed (#GOS-1612, #GS-4243).
- Bug fix: an error was fixed where enabling the SSH service on a Greenbone Enterprise TRIAL sometimes failed (#GOS-1564).
- Security fix: the included package openssl was upgraded from version 1.1.1n-0+deb11u5 to version 1.1.1w-0+deb11u1 (CVE-2023-3446, CVE-2023-3817).
- Security fix: the included package curl was upgraded from version 7.74.0-1.3+deb11u7 to version 7.74.0-1.3+deb11u10 (CVE-2023-38545, CVE-2023-38546, CVE-2023-27533, CVE-2023-27535, CVE-2023-27536, CVE-2023-27538).
- Security fix: the included package libwebp was upgraded from version 0.6.1-2.1+deb11u1 to version 0.6.1-2.1+deb11u2 (CVE-2023-4863, #GS-5145).
- Security fix: the included package mosquitto was upgraded from version 2.0.11-1 to version 2.0.11-1+deb11u1 (CVE-2021-34434, CVE-2021-41039, CVE-2023-0809, CVE-2023-3592, #GS-5082).
- Vulnerability Management:
- Major bug fix: an error was fixed where scan tasks sometimes got stuck at 100 % when a large number of host details needed to be processed (#GEA-273).
- Improvement: the new task status Processing was added. It is displayed after 100 % scan progress, indicating that the appliance is busy processing data in the backend, while any scan activity is completed as expected (#GEA-274).
- Improvement: for CVEs for which a severity score is not yet available, “N/A” is now displayed instead of the misleading severity “0.0” (#GEA-224, #GS-1160, #GS-4648, #GS-1118, #GS-1144).
- Improvement: override texts of up to 300 characters are now also included in the report formats GSR PDF, GXR PDF, Vulnerability Report HTML, and Vulnerability Report PDF (#GEA-85).
- Improvement: the limit for override texts included in the report formats Anonymous XML, XML and TXT was increased from 60 to 300 characters (#GEA-86).
- Improvement: the Assets > TLS Certificates list page now lists the TLS certificates by their subject distinguished name (“Subject DN”) instead of their issuer (#GEA-202).
- Improvement: it is now possible to specify the port used for an SCP alert. A corresponding input box was added to the dialog (#GEA-280, #GS-1555).
- Improvement: an option to ignore pagination was added to the report content composer for alerts (#GEA-124, #GS-3911, #GS-4271).
- Improvement: when changing the user password for the web interface, an error message is now displayed if the old password is incorrect or missing (#GEA-175).
- Bug fix: an error was fixed where downloading a report in the report formats Vulnerability Report HTML and Vulnerability Report PDF sometimes resulted in empty files (#GEA-209, #GS-1308).
- Bug fix: an error was fixed where scheduled tasks sometimes did not run at the correct time when the time zone PST/PDT was used (#GEA-114).
- Bug fix: an error was fixed where delta reports contained results that could not be accessed (#GEA-247, #GS-958).
- Bug fix: an error was fixed where e-mail alerts with the condition “Severity Level changed”, “Severity Level increased” or “Severity Level decreased” caused an SQL error in the logs if the task had no previous reports (#GEA-246).
- Bug fix: an incomplete sub-page that should not have been available but could be accessed by entering a URL directly has been removed (#GEA-177, #GS-4392)
- Minor improvement: the included appliance manual was updated to the current version from 2023-10-09 (#PR-746).
- Minor bug fix: an error was fixed where dashboard diagrams showing a resource “by CVSS” (e.g., “Hosts by CVSS”) displayed 10.9 as the highest severity when hovering over the associated column (#GEA-265).
- Minor bug fix: an error was fixed where the process title of gvmd displayed a duplicated “gvmd: gvmd:” (#GEA-240).
- Vulnerability Scanning:
- Minor improvement: the system log message indicating when the Notus scanner is running has been simplified and is now only displayed when the requirements for Notus scanner operation are met (#SC-902).
22.04.14 (2023-08-31):
- Greenbone OS:
- Improvement: the the company name displayed in the GOS administration menu and the SNMP MIBs was updated to show the new company name „Greenbone AG“ (#GOS-1494).
- Improvement: the RAM limit of the appliance model Greenbone Enterprise 150 was increased from 6 GB to 8 GB (#GOS-1584).
- Bug fix: on the sensor appliances, Greenbone Enterprise 35 and Greenbone Enterprise 25V, an error was fixed where gos-grub was missing a dependency to e2fsprogs which resulted in an error message when starting the appliance (#GOS-1576).
- Security fix: the microcode included in the hardware kernels of the appliance models Greenbone Enterprise 6500/5400/650 R2/600 R2/450 R2/400 R2 were upgraded to the state of the release microcode-20230808 (CVE-2022-40982).
- Security fix: the Linux kernel was upgraded from version 5.10.179-1 to version 5.10.191-1 for virtual appliances (CVE-2022-4269, CVE-2022-39189, CVE-2022-40982, CVE-2023-1206, CVE-2023-1380, CVE-2023-2002, CVE-2023-2007, CVE-2023-2124, CVE-2023-2156, CVE-2023-2269, CVE-2023-2898, CVE-2023-3090, CVE-2023-3111, CVE-2023-3212, CVE-2023-3268, CVE-2023-3269, CVE-2023-3338, CVE-2023-3389, CVE-2023-3390, CVE-2023-3609, CVE-2023-3610, CVE-2023-3611, CVE-2023-3776, CVE-2023-3863, CVE-2023-4004, CVE-2023-4128, CVE-2023-4132, CVE-2023-4147, CVE-2023-4194, CVE-2023-4273, CVE-2023-20588, CVE-2023-20593, CVE-2023-21255, CVE-2023-21400, CVE-2023-31084, CVE-2023-31248, CVE-2023-32250, CVE-2023-32254, CVE-2023-34319, CVE-2023-35001, CVE-2023-35788, CVE-2023-40283).
- Security fix: the Linux kernel was upgraded from version 5.10.186-greenbone1 to version 5.10.192-greenbone-1 for hardware appliances (CVE-2022-4269, CVE-2022-39189, CVE-2022-40982, CVE-2023-1206, CVE-2023-1380, CVE-2023-2002, CVE-2023-2007, CVE-2023-2124, CVE-2023-2156, CVE-2023-2269, CVE-2023-2898, CVE-2023-3090, CVE-2023-3111, CVE-2023-3212, CVE-2023-3268, CVE-2023-3269, CVE-2023-3338, CVE-2023-3389, CVE-2023-3390, CVE-2023-3609, CVE-2023-3610, CVE-2023-3611, CVE-2023-3776, CVE-2023-3863, CVE-2023-4004, CVE-2023-4128, CVE-2023-4132, CVE-2023-4147, CVE-2023-4194, CVE-2023-4273, CVE-2023-20588, CVE-2023-20593, CVE-2023-21255, CVE-2023-21400, CVE-2023-31084, CVE-2023-31248, CVE-2023-32250, CVE-2023-32254, CVE-2023-34319, CVE-2023-35001, CVE-2023-35788, CVE-2023-40283).
- Minor bug fix: an error was fixed where setting the GOS state variable max_ips_per_target to 0 in the GOS shell caused the gvmd service to fail. The minimum input value for max_ips_per_target is now 1 (#GOS-1539).
- Minor bug fix: a superfluous GnuPG key ring file for the OpenVAS scanner was removed from GOS (#GOS-1572).
- Minor security fix: a missing kernel-side mitigation for the ‘Processor MMIO Stale Data’ and ‘SRBDS – Special Register Buffer Data Sampling’ hardware appliance vulnerabilities was added for the appliance models Greenbone Enterprise 650 R2/600 R2/450 R2/400 R2 (#GOS-1541).
- Vulnerability Management:
- Improvement: the product logo on the web interface was replaced to show the correct product name “Greenbone Enterprise Appliance” (#GOS-1538).
- Improvement: the error message displayed when clicking a CPE name that does not have a linked CPE entry was reworded to clarify the reasons for a missing CPE entry (#GEA-207, #GS-43).
- Improvement: the performance when editing scan configurations or policies on the web interface has been improved (#GEA-235).
- Improvement: the performance of gvmd rebuilds has been further improved (#GEA-235).
- Bug fix: an error was fixed where the setting Use workaround default certificate for an alert with the TippingPoint SMS method was not saved (#GEA-181, #GEA-230, #GS-4209).
- Bug fix: an error was fixed where uploading an unsupported certificate file format for an alert with the TippingPoint SMS method did not show a warning but silently corrupted the alert data used by gmvd (#GEA-254).
- Bug fix: an error was fixed where IP addresses were cropped in the Top 10 Hosts overview of the report formats Vulnerability Report PDF and Vulnerability Report HTML (#GEA-46, #GS-3693).
- Bug fix: an error was fixed where in rare cases scan reports could not be deleted (#GEA-2, #GS-2073).
- Bug fix: an error was fixed where in rare cases only a partial response would be received via the GMP API (#GEA-235).
- Minor bug fix: an error was fixed where the “?” icon on the page SecInfo > NVTs did not lead to the correct user manual section (#GEA-262).
- Minor bug fix: an error was fixed where the browser tab of the web interface showed incorrect and changing text when logging in and out of the web interface (#GEA-1543).
- Minor improvement: when a user with the Super Admin role changes their own user settings, a warning is now displayed explaining that saving the changes will log the user out immediately (#GEA-37).
- Minor improvement: the included appliance manual was updated to the current version from 2023-08-14 (#PR-718).
- Vulnerability Scanning:
- Bug fix: an additional error was fixed where not every JSON string was parsed correctly during inter-process communication (#SC-886).
22.04.13 (2023-07-17):
- Vulnerability Management:
- Major bug fix: another error was fixed where scan tasks appeared to be frozen on gvmd side/the web interface, while they were actually progressing or even finishing on ospd/ospd-openvas side. This problem could occur when both error messages (e.g., from VT timeouts) and duplicated scan results occurred at the same time during a scan (#GEA-250, #GS-4727, #GS-4734, #GS-4780).
- Bug fix: an error was fixed where a gvmd rebuild could cause a segmentation fault when VT preference names in old scan configurations were updated (#GEA-245).
- Minor improvement: the included appliance manual was updated to the current version from 2023-07-14 (#PR-696).
22.04.12 (2023-07-10):
- Greenbone OS:
- Improvement: the package python-gvm included in GOS was updated to version 23.5.1 (#PR-644).
- Security fix: the Linux kernel was upgraded from version 5.10.180-greenbone1 to version 5.10.186-greenbone1 for hardware appliances (CVE-2023-35788).
- Security fix: the included package openssl was upgraded from version 1.1.1n-0+deb11u4 to version 1.1.1n-0+deb11u5 (CVE-2023-0464, CVE-2023-0465, CVE-2023-0466, CVE-2023-2650).
- Vulnerability Management:
- Major bug fix: an error was fixed where scan tasks appeared to be frozen on gvmd side/the web interface, while they were actually progressing or even finishing on ospd/ospd-openvas side. This problem could occur when unexpected characters were contained in the scan results (#GEA-223, #GS-4639, #GS-4672, #GS-4679, #GS-4727, #GS-4706, #GS-4698, #GS-4712, #GS-4721).
- Major bug fix: an error was fixed where a gvmd rebuild, which can occur due to hash value mismatches during feed updates, caused failed scan task requests, and missing VT and result names in the SecInfo menu and in scan reports (#GEA-49, #GEA-50, #GS-3459, #GS-3346, #GS-2947, #GS-3367).
- Security fix: an issue was fixed where scan tasks could cause an SQL error due to missing SQL quoting, potentially allowing a denial of service (DoS) attack against the scan task that triggered the error via SQL-Injection, causing the task to be interrupted (#GEA-226, #GS-4596, #GS-4639, #GS-4672, #GS-4679, #GS-4727, #GS-4706, #GS-4698, #GS-4712, #GS-4721).
- Improvement: the performance of gvmd rebuilds, which can occur due to hash value mismatches during feed updates, has been improved, and rebuilds should now finish noticeably faster (#GEA-49, #GEA-50).
- Improvement: the performance of the GMP command get_targets has been improved, which should noticeably speed up the use of menus and dialogs with links to a large number of targets (#GEA-241).
- Improvement: the usability of the dialog for creating permissions was improved by making it clearer which object the permission refers to and which the related resources are (#GEA-74, #GS-50, #GS-2948).
- Bug fix: an error was fixed where scan tasks were interrupted at 100 %, if the scan used an alert with the “Filter … matches at least … results more than previous scan” condition (#GEA-146, #GS-4112).
- Bug fix: an error was fixed where running a CVE scan could sometimes cause subsequent OpenVAS scans to fail (#GEA-211).
- Bug fix: an error was fixed where the details of TippingPoint alerts did not show any information about the saved TLS certificate (#GEA-180, #GS-4209).
- Bug fix: an error was fixed where the usage_type element contained the value “(null)” instead of “policy” or “config” when using the GMP command get_configs, which could, for example, cause scan configurations and policies to appear under the wrong menus when manually imported or when moved to the trashcan (#GEA-204, #GEA-225, #GS-4653).
- Minor improvement: the placeholder subject for an e-mail alert now shows the new, correct product name “Greenbone Enterprise Appliance” instead of the formerly used abbreviation “GSM” (#GOS-1491).
- Minor improvement: a log message has been added explaining the reason why scans will not run when no feed has been synced on the appliance yet (#GEA-49).
- Minor improvement: the included appliance manual was updated to the current version from 2023-07-03 (#PR-681).
- Minor bug fix: an error was fixed where two German translations – in the LDAP authentication dialog and in the SMB alert drop-down menu – were missing (#GEA-163).
- Vulnerability Scanning:
- Bug fix: an error was fixed where scans were interrupted if a host was reached for which scanner access had been denied via the user settings, so that further, allowed hosts were not scanned (#SC-837).
22.04.11 (2023-05-31):
- Greenbone OS:
- Improvement: the package gvm-tools included in GOS was updated to version 23.4.0 (#PR-615).
- Improvement: the package python-gvm included in GOS was updated to version 23.4.2 (#PR-615).
- Security fix: the included package libxml2 was upgraded from version 2.9.10+dfsg-6.7+deb11u3 to version 2.9.10+dfsg-6.7+deb11u4 (CVE-2023-28484, CVE-2023-29469).
- Security fix: the included package libssh was upgraded from version 0.9.5-1+deb11u1 to version 0.9.7-0+deb11u1 (CVE-2023-1667, CVE-2023-2283).
- Security fix: the included package postgresql-13 was upgraded from version 13.10-0+deb11u1 to version 13.11-0+deb11u1 (CVE-2023-2454, CVE-2023-2455).
- Security fix: the Linux kernel was upgraded from version 5.10.162-1 to version 5.10.179-1 for virtual appliances (CVE-2022-2196, CVE-2022-3424, CVE-2022-3707, CVE-2022-4129, CVE-2022-4379, CVE-2023-0045, CVE-2023-0458, CVE-2023-0459, CVE-2023-0461, CVE-2023-1073, CVE-2023-1074, CVE-2023-1076, CVE-2023-1077, CVE-2023-1078, CVE-2023-1079, CVE-2023-1118, CVE-2023-1281, CVE-2023-1513, CVE-2023-1611, CVE-2023-1670, CVE-2023-1829, CVE-2023-1855, CVE-2023-1859, CVE-2023-1872, CVE-2023-1989, CVE-2023-1990, CVE-2023-1998, CVE-2023-2162, CVE-2023-2194, CVE-2023-22998, CVE-2023-23004, CVE-2023-23559, CVE-2023-25012, CVE-2023-26545, CVE-2023-28328, CVE-2023-28466, CVE-2023-30456, CVE-2023-0386, CVE-2023-31436, CVE-2023-32233).
- Security fix: the Linux kernel was upgraded from version 5.10.155-greenbone1 to version 5.10.180-greenbone1 for hardware appliances (CVE-2022-2873, CVE-2022-3545, CVE-2022-3623, CVE-2022-4696, CVE-2022-36280, CVE-2022-41218, CVE-2022-45934, CVE-2022-47929, CVE-2023-0179, CVE-2023-0266, CVE-2023-0394, CVE-2023-23454, CVE-2023-23455, CVE-2022-2196, CVE-2022-3424, CVE-2022-3707, CVE-2022-4129, CVE-2022-4379, CVE-2023-0045, CVE-2023-0458, CVE-2023-0459, CVE-2023-0461, CVE-2023-1073, CVE-2023-1074, CVE-2023-1076, CVE-2023-1077, CVE-2023-1078, CVE-2023-1079, CVE-2023-1118, CVE-2023-1281, CVE-2023-1513, CVE-2023-1611, CVE-2023-1670, CVE-2023-1829, CVE-2023-1855, CVE-2023-1859, CVE-2023-1872, CVE-2023-1989, CVE-2023-1990, CVE-2023-1998, CVE-2023-2162, CVE-2023-2194, CVE-2023-22998, CVE-2023-23004, CVE-2023-23559, CVE-2023-25012, CVE-2023-26545, CVE-2023-28328, CVE-2023-28466, CVE-2023-30456, CVE-2023-0386, CVE-2023-31436, CVE-2023-32233).
- Vulnerability Management:
- Major bug fix: an error was fixed where new CPEs could not be processed during feed updates, causing the gvmd service to be stuck in a loop (#GEA-208).
- Improvement: the company name displayed in the footer of the web interface was updated to show the new company name “Greenbone AG” (#GEA-147).
- Improvement: the Operating Systems list page now shows two columns for Hosts: All and Best OS, making it possible to differentiate between hosts for which the operating system was found at all and hosts for which the operating system is the most suitable operating system (#GEA-117).
- Bug fix: an error was fixed where subsequent scans against the same scan target sometimes resulted in duplicated scan results (#GEA-51, #GS-169. #GS-3697, #GS-3739).
- Bug fix: an error was fixed where tasks were set from the scan status “Requested” to “Stopped” when starting a scheduled task manually, but the scanner started the scan nonetheless (#GEA-12, #GS-173, #GS-2919).
- Bug fix: an error was fixed where the “Product Detection Result” section was missing for results of reports that were imported into a container task (#GEA-135).
- Bug fix: an error was fixed where false-positive result counts were not shown in the reports overview (#GEA-79).
- Bug fix: an error was fixed where TippingPoint SMS alerts did not save the specified credentials and used the alphabetically first credentials instead (#GEA-158, #GS-4209).
- Bug fix: an error was fixed where the line chart on the web interface (e.g., on the CVE page) did not show any lines (#GEA-143, #GS-4105, #GS-4390).
- Bug fix: an error was fixed where using an alert for the event New CVEs did not work and resulted in SQL errors in the logs (#GEA-129).
- Bug fix: an error was fixed where an operating system asset was shown to be “in use” and therefore could not be deleted even though no hosts for the operating system were shown in the counter (#GEA-117, #GS-837).
- Bug fix: an error was fixed where setting the correct permissions for data-objects during feed updates failed for custom roles (#GEA-116, #GS-3860).
- Bug fix: an error was fixed where successful SNMP authentication was shown as unsuccessful on the web interface if the authentication was successful with one protocol version (e.g., SNMPv3) but unsuccessful with another protocol version (e.g., SNMPv1) (#GEA-131, #GS-3967).
- Bug fix: an error was fixed where the authentication type LDAP was not correctly displayed in the details preview of a user and on the details page of a user (#GEA-27, #GS-625).
- Minor improvement: a new info message to identify duplicate host details was added for the gvmd service (#GEA-182).
- Minor improvement: when creating an SMB alert, the menu option for using the latest supported SMB version is now called “Default” to avoid confusion (#GEA-161).
- Minor improvement: the included appliance manual was updated to the current version from 2023-05-15 (#PR-627).
22.04.10 (2023-04-19):
- Greenbone OS:
- Bug fix: an error was fixed where after adding a temporary upgrade key, GOS upgrades did not work as expected (#GOS-1082).
- Bug fix: an error was fixed where GOS upgrades would fail when remote syslog was enabled (#GEA-148, #GS-4153, #GS-4120).
- Improvement: the package gvm-tools included in GOS was updated to version 23.3.0 (#PR-596).
- Improvement: the package python-gvm included in GOS was updated to version 23.4.0 (#PR-596).
- Vulnerability Management:
- Major bug fix: an error was fixed where opening the details page of a CPE that has associated CVEs caused all RAM and swap to be occupied, leading to gvmd and the web interface being unresponsive (#GEA-138, #GS-4088, #GS-4044, #GS-4115).
- Major bug fix: an error was fixed where opening the details page of a CPE that has associated CVEs would fail with the error “e.entry.cvss is undefined” or “Cannot read properties of undefined (reading ‘base_metrics’)” (#GEA-157, #GS-4088, #GS-4044, #GS-4115).
- Bug fix: an error was fixed where reports from CVE scans, both on the web interface and in downloaded reports, only displayed the IP addresses of the scanned hosts and not the host names (#GEA-4, #GS-2458).
- Improvement: an option to set the maximum SMB version used for an SMB alert was added (#GEA-38, #GS-1588).
- Improvement: an option to enforce LDAPS for the LDAP authentication was added (#GEA-82, #GS-3777).
- Minor improvement: the included appliance manual was updated to the current version from 2023-04-14 (#PR-598).
- Vulnerability Scanning:
- Minor bug fix: an error was fixed where a traceback occurred if the ospd-openvas service could not locate the scanner binary (#SC-789).
- Minor improvement: the detection of unreachable (dead) hosts in the end_denial function of the scanner has been improved (#SC-772).
- Minor improvement: the option sign is now set as a default for the wmi_connect function of the scanner (#SC-779, #GS-1771, #GS-3756, #GS-3628).
- Minor improvement: support for epoch in RPM package version comparison was added (#SC-795, #GS-3272).
22.04.9 (2023-03-08):
- Greenbone OS:
- Improvement: the package gvm-tools included in GOS was updated to version 23.2.0 (#PR-568).
- Improvement: the package python-gvm included in GOS was updated to version 23.2.0 (#PR-568).
- Security fix: the included package syslog-ng was upgraded from version 3.28.1-2 to version 3.28.1-2+deb11u1 (CVE-2022-38725).
- Minor improvement: if a custom value for the maximum number of concurrent connections to the PostgreSQL database has been configured, it is now included in the GOS support package for debugging purposes (#GEA-25).
- Vulnerability Management:
- Bug fix: an error was fixed where creating a downloadable Debian (.deb) credential package was not possible (#GEA-45, #GS-1253, #GS-1628).
- Bug fix: an error was fixed where the appliance caused re-authentications with RADIUS-2FA every 5 minutes (#GEA-36, #GS-224).
- Bug fix: an error was fixed where the performance graphs could sometimes not be created (#GEA-28, #GS-3507).
- Security fix: an issue was fixed where the shared key for RADIUS authentication was stored in plain text (without encryption) in the database and included in the GMP responses (#GEA-41).
- Security fix: for the included package gsm-greenbone-security-assistant, multiple vulnerabilities in the build dependencies were fixed (#GEA-53).
- Minor improvement: the included appliance manual was updated to the current version from 2023-02-28 (#PR-581).
- Vulnerability Scanning:
- Bug fix: an error was fixed where simultaneously started scans erroneously had the same position in the scan queue (#SC-755, #GS-3450).
- Bug fix: two potential memory leaks in the misc/bpf_share.c and nasl/nasl_packet_forgery.c functions were fixed (#SC-769).
22.04.8 (2023-02-15):
- Greenbone OS:
- Extension: the SNMP service (GOS menu Setup > Services > SNMP) and the automatic time synchronization via NTP (GOS menu Setup > Timesync) are made available for the appliance model Greenbone Enterprise CENO. To access the newly enabled features it is required to log out and then log back in to the GOS menu (#GEA-31, #GS-3658).
- Bug fix: an error was fixed where the airgap FTP functionality did not work and the folder /tmp was filled with unwanted data, potentially causing the file system to run out of free space (#GEA-23, #GS-3032).
- Bug fix: an error was fixed where the optional package gsm-debug could not be installed due to a broken dependency (#GEA-81).
- Security fix: the included package openssl was upgraded from version 1.1.1n-0+deb11u3 to version 1.1.1n-0+deb11u4 (CVE-2022-2097, CVE-2022-4304, CVE-2022-4450, CVE-2023-0215, CVE-2023-0286).
- Security fix: the Linux kernel was upgraded from version 5.10.158-2 to version 5.10.162-1 for virtual appliances (CVE-2022-2873, CVE-2022-3545, CVE-2022-3623, CVE-2022-4696, CVE-2022-36280, CVE-2022-41218, CVE-2022-45934, CVE-2022-47929, CVE-2023-0179, CVE-2023-0266, CVE-2023-0394, CVE-2023-23454, CVE-2023-23455).
- Vulnerability Management:
- Minor improvement: the included appliance manual was updated to the current version from 2023-02-14 (#PR-572).
22.04.7 (2023-01-26):
- Greenbone OS:
- Bug fix: an error was fixed where formatting a USB drive to serve as a GOS backup device was not possible (#GOS-1287, #GS-3610).
- Security fix: the included package libksba8:amd64 was upgraded from version 1.5.0-3+deb11u1 to version 1.5.0-3+deb11u2 (CVE-2022-47629).
- Minor improvement: the gos-network-manager self-check now fails only when an error occurs for the corresponding service. Previously, it failed if an error or warning occurred for the service. Warnings are still logged in the system log for debugging purposes, however (#GOS-1266, #GS-3437).
- Vulnerability Management:
- Bug fix: an error was fixed where many special characters were not accepted in the names and comments of multiple web interface objects (#DEVOPS-475, #DEVOPS-477, #GS-3509, #GS-3549, #GS-3608, #GS-3629, #GS-3649).
- Bug fix: an error was fixed where reports sent via alerts did not contain all results they were supposed to contain according to the configured filter (#T4-420, #GS-3458).
- Bug fix: an error was fixed where manually triggering an alert for a report always sent the report for the latest scan run of that task and not for the triggered one (#T4-411).
- Bug fix: an error was fixed where the LDAP version could get wrongly set to 2 instead of 3 when STARTTLS was disabled, resulting in the LDAPS connection not being possible (#T4-398).
- Security fix: the attribute “SameSite=Strict” was set for the cookies used by the web interface (#T3-509).
- Minor improvement: the included appliance manual was updated to the current version from 2023-01-16 (#PR-557).
- Vulnerability Scanning:
- Bug fix: an error was fixed where the OpenVAS scanner was still processing vulnerability tests after the corresponding scan task was stopped (#SC-744).
- Bug fix: an error was fixed where the Notus package comparison was not working correctly for packages containing a “~” in the version, causing false-positive results (#SC-752, #SC-754, #GS-3051, #GS-3499).
- Bug fix: an error was fixed where the ospd-openvas service could not start normally when a corresponding empty .pid file existed (#SC-746).
- Bug fix: an error was fixed where the Notus scanner could not start normally when a corresponding empty .pid file existed (#SC-748).
- Bug fix: an error was fixed where not every JSON string was parsed correctly during inter-process communication, potentially causing interrupted scan tasks (#SC-747).
- Minor improvement: the openvas-wmiclient library was updated to provide better Windows Management Instrumentation (WMI) support when scanning Windows Server 2022 targets (#SC-645).
22.04.6 (2022-12-15):
- Vulnerability Management:
- Major improvement: the new WID-SEC format of the CERT-Bund advisories which has been available since June 2022, is now also supported. Numerous new WID-SEC advisories have been added to the feed and are visible on the web interface under SecInfo > CERT-Bund Advisories (#DEVOPS-355).
- Minor improvement: the included appliance manual was updated to the current version from 2022-12-13 (#PR-541).
- Vulnerability Scanning:
- Improvement: if a database inconsistency is detected while performing a vulnerability test, the vulnerability test is now aborted immediately, since the result is lost anyway. In addition, the method for detecting such inconsistencies has been improved (#SC-647).
- Bug fix: an error was fixed where JSON strings were not parsed correctly during inter-process communication, causing interrupted scan tasks (#SC-738).
22.04.5 (2022-12-01):
- Greenbone OS:
- Status: The lifecycle status of GOS 22.04 was set to “mature”. (#GOS-1267).
- Bug fix: an error was fixed where copying files via SCP to or from the appliance was not possible as the openssh server configuration of GOS was not compatible with newer openssh versions (#GOS-883).
- Security fix: the Linux kernel was upgraded from version 5.10.140-1 to version 5.10.155-greenbone1 for hardware appliances and to version 5.10.149-2 for virtual appliances (CVE-2021-4037, CVE-2022-0171, CVE-2022-1184, CVE-2022-2602, CVE-2022-2663, CVE-2022-3061, CVE-2022-3176, CVE-2022-3303, CVE-2022-20421, CVE-2022-39188, CVE-2022-39842, CVE-2022-40307, CVE-2022-41674, CVE-2022-42719, CVE-2022-42720, CVE-2022-42721, CVE-2022-42722).
- Security fix: the included package libxml2:amd64 was upgraded from version 2.9.10+dfsg-6.7+deb11u2 to version 2.9.10+dfsg-6.7+deb11u3 (CVE-2022-40303, CVE-2022-40304).
- Security fix: the included package libexpat1:amd64 was upgraded from version 2.2.10-2+deb11u4 to version 2.2.10-2+deb11u5 (CVE-2022-43680).
- Security fix: the included package isc-dhcp-client was upgraded from version 4.4.1-gos2110+1 to version 4.4.1-2.3+deb11u1 (CVE-2022-2928, CVE-2022-2929).
- Security fix: the included packages libkrb5-3:amd64, libkrb5support0:amd64 and libgssapi-krb5-2:amd64 were upgraded from version 1.18.3-6+deb11u2 to version 1.18.3-6+deb11u3 (CVE-2022-42898).
- Vulnerability Management:
- Bug fix: an error was fixed where selecting the permission scope, i.e., whether it should be created only for the resource, for related resources as well or only for related resources, was not possible when creating a permission via the object’s details page (#T4-276).
- Minor improvement: the included appliance manual was updated to the current version from 2022-11-25 (#PR-536).
- Vulnerability Scanning:
- Major bug fix: an error was fixed where scans would get stuck for no apparent reason (#SC-741).
- Bug fix: an error was fixed where RPM packages for Mageia were not detected correctly, causing false-negative results (#SC-722).
22.04.4 (2022-11-01):
- Greenbone OS:
- Improvement: the package gvm-tools included in GOS was updated to version 22.9.0 (#PR-499).
- Improvement: the package python-gvm included in GOS was updated to version 22.9.1 (#PR-499).
- Security fix: the included package libksba8:amd64 was upgraded from version 1.5.0-3 to version 1.5.0-3+deb11u1 (CVE-2022-3515).
- Security fix: the included package python3-django was upgraded from version 2:2.2.28-1 to version 2:2.2.28-1~deb11u1 (CVE-2022-22818, CVE-2022-23833, CVE-2022-28346, CVE-2022-28347, CVE-2022-34265, CVE-2022-36359, CVE-2022-41323).
- Security fix: the included package libdbus-1-3:amd64 was upgraded from version 1.12.20-2 to version 1.12.24-0+deb11u1 (CVE-2022-42010, CVE-2022-42011, CVE-2022-42012).
- Bug fix: an error was fixed where the switch release from GOS 21.04 to GOS 22.04 would fail if the PostgreSQL package was updated to version 13.8.0 or later (#GOS-1143).
- Vulnerability Management:
- Bug fix: an error was fixed where the migration of the gvmd database would fail if the PostgreSQL package was updated to version 13.8.0 or later (#T3-364).
- Minor improvement: the included appliance manual was updated to the current version from 2022-10-24 (#PR-506).
- Vulnerability Scanning:
- Improvement: support for Slackware Linux packages was added to the Notus scanner (#SC-637).
- Improvement: the list of default TCP ports which the Boreas Alive Scanner uses for the alive test was improved and now contains the Nmap top 20 ports (#SC-663).
- Improvement: the new scanner preference alive_test_ports was added to configure the TCP ports used by the Boreas Alive Scanner for the alive test. The setting only has an effect on the alive tests TCP-ACK Service Ping and TCP-SYN Service Ping (#SC-689).
- Improvement: the new scanner preference test_alive_wait_timeout was added to configure the timeout of the Boreas Alive Scanner (#SC-680).
- Improvement: the Redis caches for OpenVAS and Notus were separated, the nvticache module now only handles OpenVAS VTs and the Notus cache module now only handles Notus advisories (#SC-692).
- Improvement: a fork observing mechanism was added which makes it possible to track every fork within a parent process, to manage forked children and to set limits to the number of possible forks (#SC-565).
- Bug fix: an error was fixed where the values set for Maximum concurrently scanned hosts and Maximum concurrently executed NVTs per host were limited to 15 and 10 respectively, even if the appliance model supported larger values (#SC-696).
- Bug fix: an error was fixed where the Quality of Detection (QoD) was incorrectly displayed on the web interface and in scan reports for Notus VTs (#SC-683).
- Bug fix: an error was fixed where tasks were interrupted when the severity_vector tag of a VT contained additional metrics other than the base score metrics (#SC-706).
- Bug fix: an error was fixed where version ranges defined for a lower version bound were ignored by the Notus scanner leading to a broken version range comparison for RPM packages (#SC-694).
- Bug fix: an error was fixed where comparing the two RPM packages for Oracle Linux did not work correctly due to “1.1.1c” being parsed as “1.1.1rc0”, leading to false-positive results (#SC-691, #GS-3085).
- Bug fix: an error was fixed where comparing RPM packages for Oracle Linux that contain fips or ksplice did not work correctly and led to false-positive results (#SC-690, #GS-3085).
- Bug fix: an error was fixed where Debian packages containing a “-” were parsed incorrectly, leading to false-positive results (#SC-682, #SC-684, #GS-3034, #GS-3051, #GS-3188, #GS-3189).
- Bug fix: an error was fixed where the comparison for Debian packages was not correct, as the single parts of the version were not compared part by part, but as a whole, leading to false-positive results (#SC-677).
- Minor improvement: the error message issued when chdir fails has been reworded from “Not able to open nor to locate it in include paths” to “Not able to change working directory to” to avoid confusion (#PR-500).
22.04.3 (2022-10-06):
- Greenbone OS:
- Security fix: the included package libexpat1:amd64 was upgraded from version 2.2.10-2+deb11u3 to version 2.2.10-2+deb11u4 (CVE-2022-40674).
- Security fix: the included packages libgdk-pixbuf-2.0-0:amd64 and libgdk-pixbuf2.0-common were upgraded from version 2.42.2+dfsg-1 to version 2.42.2+dfsg-1+deb11u1 (CVE-2021-44648, CVE-2021-46829).
- Minor improvement: if it exists, the superfluous file /var/lib/redis/dump.rdb is removed automatically when upgrading to GOS 22.04.3 or later (#GOS-1141).
- Vulnerability Management:
- Improvement: a problem was fixed where the filter keyword first was used twice for different filter functions and thus, filtering for tasks having a first report within a certain period of time was not possible. To filter for the time of the first or last report respectively, the new filter keywords first_report_created and last_report_created have been added. These replace the previously documented keywords first and last, which are thereby deprecated for this use case (#T3-226).
- Minor improvement: the included appliance manual was updated to the current version from 2022-10-05 (#PR-482).
- Vulnerability Scanning:
- Major bugfix: an error was fixed where Redis occupied an increasing amount of RAM and disk space after every reboot or VT reload, which could negatively affect system stability and scan performance (#SC-675, #SC-679, #GS-2809, #GS-2836, #GS-3000, #GS-3021).
- Bugfix: an error was fixed where Notus used the Redis namespace 0 for the advisories and not an own namespace (#SC-678).
22.04.2 (2022-09-12):
- Greenbone OS:
- Major bug fix: an error was fixed where activating the SNMP service was not possible and thus, no SNMP connection to the appliance could be established (#GOS-1081).
- Improvement: a file system check is now run by default when booting a virtual appliance (#GOS-880, #GS-2111, #GS-1986, #GS-2170, #GS-2324).
- Security fix: the kernel of the hardware appliances was upgraded from version 5.10.127 to version 5.10.136 (CVE-2022-2585, CVE-2022-2586, CVE-2022-2588, CVE-2022-26373, CVE-2022-29900, CVE-2022-29901, CVE-2022-36879 and CVE-2022-36946).
- Improvement: the included package python-gvm was upgraded from version 22.6.1 to version 22.8.0 to assure full compatibility with GOS 22.04/GVM 22.4 (#GOS-1084).
- Security fix: the included package libxslt was upgraded from version 1.1.34-4+deb11u1 to version 1.1.34-4+deb11u1 (CVE-2021-30560).
- Security fix: the included package open-vm-tools was upgraded from version 2:11.2.5-2 to version 2:11.2.5-2+deb11u1 (CVE-2022-31676).
- Security fix: the included package zlib was upgraded from version 1:1.2.11.dfsg-2+deb11u1 to version 1:1.2.11.dfsg-2+deb11u2 (CVE-2022-37434).
- Vulnerability Management:
- Minor improvement: the included appliance manual was updated to the current version from 2022-08-30 (#GOS-1084).
- Vulnerability Scanning:
- Improvement: ospd-openvas now tries to connect to the MQTT broker every 10 seconds if the last attempt failed to ensure that there is a broker connection even if ospd-openvas was started without a broker running (#SC-651).
- Bug fix: an error was fixed where duplicate results or results of other scans appeared in the scan report (#SC-378, #SC-34, #GS-403).
- Bug fix: an error was fixed where scans were continued in the background although they were stopped by the user (#SC-624, #GS-1864).
- Bug fix: an error was fixed where nmap continued scanning although the scan was stopped by the user (#SC-626, #GS-1654).
- Bug fix: an error was fixed where, in case no MQTT broker was running, notus-scanner ended with a ConnectionRefuseError as an exception (#SC-650).
- Bug fix: an error was fixed where ospd-openvas data-pickle-files were not cleaned up properly, causing the root volume to fill up (#SC-643, #GS-2457).
- Bug fix: an error was fixed where ospd-openvas stopped working instead of showing an error message when the sha256sums files were missing (#SC-646, #DEVOPS-314).
- Bug fix: an error was fixed where Notus-based VTs did not include references in the vulnerability and result detail overviews (#SC-648).
- Bug fix: an error was fixed where ospd-openvas got stuck when starting the appliance (#SC-662).
- Bug fix: an error was fixed where SSL/TLS enabled services were not detected correctly (#SC-659, #GS-2774, #GS-2803, #GS-2836).
- Minor improvement: a case where a missing scan_id threw an error with stacktrace in the logs was changed to a warning message, as this does not block the execution of ospd-openvas (#SC-285, #GS-156).
- Minor improvement: the socket_negotiate_ssl called() logs now also show the target host’s IP addresses (#SC-625).
22.04.1 (2022-08-19):
- Greenbone OS:
- Major bugfix: an error was fixed where the checksum file signature verification of the Greenbone Enterprise Feed failed, which also impeded the scanning functionality (#GOS-1079).
- Security fix: the RPC library libtirpc that is included in GOS was upgraded from version 3_1.3.1-1 to version 1.3.1-1+deb11u1 (CVE-2021-46828).
- Security fix: the library GnuTLS was upgraded from version 3.7.1-5+deb11u1 to version 3.7.1-5+deb11u2 (CVE-2022-2509).
- Security fix: the included InfoZIP’s unzip program version was upgraded from version 6.0-26 to version 6.0-26+deb11u1 (CVE-2022-0529 and CVE-2022-0530).
- Security fix: the package samba that is included in GOS was upgraded from version 2:4.13.13+dfsg-1~deb11u4 to version 2:4.13.13+dfsg-1~deb11u5 (CVE-2022-2031, CVE-2022-32742, CVE-2022-32744, CVE-2022-32745 and CVE-2022-32746).
- Security fix: the packages libldb and python3-ldb were upgraded from version 2:2.2.3-2~deb11u1 to version 2:2.2.3-2~deb11u2 (CVE-2022-32745).
- Security fix: the included package openssl was upgraded from version openssl_1.1.1n-0+deb11u2 to version openssl_1.1.1n-0+deb11u3 (CVE-2022-2068).
- Vulnerability Management:
- Minor improvement: the included appliance manual was updated to the current version from 2022-08-18 (#GOS-1065).
22.04.0 (2022-08-08):
Notus Scanner
With GOS 22.04, the new Notus Scanner is implemented. It scans after every regular scan, so no user interaction is necessary.
The Notus Scanner offers better performance due to less system resource consumption and thus, faster scanning.
When creating a scan configuration manually and the Notus Scanner is supposed to work, the VT Determine OS and list of installed packages via SSH login (OID: 1.3.6.1.4.1.25623.1.0.50282) must be activated.
The Notus Scanner replaces the logic of potentially all NASL-based local security checks (LSCs). A comparison of installed software on a host against a list of known vulnerable software is done instead of running a VT script for each LSC.
The regular OpenVAS Scanner loads each NASL LSC individually and executes it one by one for every host. A single known vulnerability is then compared to the installed software. This is repeated for all LSCs.
With the Notus Scanner, the list of installed software determined during a scan is directly compared to all known vulnerabilities. This eliminates the need to run the LSCs because the information about the known vulnerable software is collected in one single list and not distributed in individual NASL scripts.
Currently, Notus data exists for the following LSC VT families:
- AlmaLinux Local Security Checks
- Amazon Linux Local Security Checks
- Debian Local Security Checks
- EulerOS Local Security Checks
- Mageia Linux Local Security Checks
- Oracle Linux Local Security Checks
- Red Hat Linux Local Security Checks
- Rocky Linux Local Security Checks
- Slackware Local Security Checks
- SuSE Local Security Checks
- Ubuntu Local Security Checks
The setting Report vulnerabilities of inactive Linux kernel(s) separately in the VT Options for Local Security Checks is deprecated. However, the setting is still visible, but no longer functional.
Appliance Feature Set
With GOS 22.04, the feature set for some appliances is extended:
- The SNMP service (GOS menu Setup > Services > SNMP) is made available for the appliance models Greenbone Enterprise 150, Greenbone Enterprise 35 and Greenbone Enterprise 25V.
- The automatic time synchronization via NTP (GOS menu Setup > Timesync) is made available for the appliance model Greenbone Enterprise 25V.
- The remote and local backup functionality (GOS menus Setup > Backup, Maintenance > Backup > Incremental Backup and Maintenance > Backup > List) is made available for the appliance model Greenbone Enterprise CENO.
Virtual Appliances
With GOS 22.04, the virtual hard disk sizes for virtual appliances are changed.
The new sizes are:
- Greenbone Enterprise EXA: 225 GB
- Greenbone Enterprise DECA/PETA/EXA: 220 GB
- Greenbone Enterprise CENO: 135 GB
- Greenbone Enterprise ONE: 130 GB
- Greenbone Enterprise 25V: 70 GB
The new sizes are only relevant for newly installed virtual appliances. Upgraded appliances keep their partition layout and thus, their required disk size.
HTTP Web Interface Access
With GOS 22.04, unencrypted HTTP access for the web interface is not supported anymore. HTTPS must be used instead.
A valid HTTPS certificate (either self-signed, or signed by a CA) must now be configured on the appliance to use the web interface.
Backups
Password for Remote Backup Repository
With GOS 22.04, it is possible to change the password of the remote backup repository. For this, the menu option Setup > Backup > Backup Password is added to the GOS administration menu. The menu option is only visible if the backup location is configured as remote.
Changing the backup password is recommended.
If multiple appliances use the same remote backup repository, it is recommended that each appliance uses its own unique backup password.
obnam
With GOS 20.08, the backend for managing backups in GOS was changed from obnam to restic. However, obnam remained available in GOS 20.08 and 21.04 as did the backups created with obnam in GOS 6 or earlier.
With GOS 22.04, obnam and all backups created with obnam are removed. Incremental backups created with GOS 6 and earlier will be removed due to incompatibility and to reclaim disk space.
If these old backups should be kept, a copy of the files must be made before upgrading to GOS 22.04. If there are any questions, contact the Greenbone Enterprise Support.
Mailhub
With GOS 22.04, a new option for enforcing the usage of SMTPS for e-mails sent by a Greenbone Enterprise Appliance is added.
For this, the GOS administration menu contains the new menu Setup > Mail > SMTP Enforce TLS.
Web Interface
Business Process Map
With GOS 22.04, the Business Process Map (BPM) functionality is removed from the web interface. Existing Business Process Maps will be deleted and will not be recoverable. If the information contained in a Business Process Map is to be saved, this must be done in GOS 21.04.
Task Setting Network Source Interface
With GOS 22.04, the task setting Network Source Interface is removed. If this setting was previously configured for a task, it will be ignored.
User Setting Interface Access
As the task setting Network Source Interface is removed with GOS 22.04, the user setting Interface Access is removed as well. If this setting was previously configured for a user, it will be ignored.
OVAL Definitions
With GOS 22.04, the OVAL definitions are removed from the SecInfo management in the web interface. The previous OVAL definitions were outdated and no longer served any purpose.
OSP Scanners
With GOS 22.04, the scanner type OSP Scanner is removed. It is no longer possible to create OSP scanners and select them to run scans.
This only affects the scanner type OSP Scanner, not the OSP protocol in general. The scanner type Greenbone Sensor will continue to use OSP.
The credential type Client Certificate that was used for (custom) OSP scanners was removed as well. Existing credentials of this type will not be affected or removed. They can still be accessed, but they are of no use anymore, and can be deleted manually.
Quality of Detection (QoD)
With GOS 22.04, the new quality of detection (QoD) level package_unreliable is implemented with a QoD of 30 %. It is used for authenticated package-based checks which are not always fully reliable for, e.g., Linux(oid) systems.
Vulnerability References
With GOS 22.04, the tag script_bugtraq_id(); which references a BID of Bugtraq is no longer supported. For VTs with such tag, the BID was displayed under References on the web interface. Since bugtraq.securityfocus.com is not maintained anymore, the reference only led to confusion.
All existing BID references were migrated to Other references and will appear there as URLs on the web interface. To access the contents of the URLs, common services such as archive.org can be used.
Greenbone Management Protocol (GMP)
The Greenbone Management Protocol (GMP) has been updated to version 22.04 and the API has been adjusted slightly. The usage of some commands has changed and several commands, elements and attributes have been deprecated. The complete reference guide and the list of changes are available here.
