Exposure Management
Reading time: 12 minutes
What Is the “Exposure Management” Approach to Cyber Security?
- Vulnerability Management is the traditional cyber security control for mitigating technical vulnerabilities across IT infrastructure
- As IT infrastructure evolves and adversaries develop new techniques, new attack surfaces emerge
- Exposure Management and Continuous Threat Exposure Management (CTEM) expand the concept of attack surface to include new types of risk
- A comprehensive attack surface map is critical for reducing an organization’s cyber risk
- Greenbone’s OPENVAS PRODUCTS help manage attack surface at all stages of an Exposure Management program
What Is Exposure Management and Continuous Threat Exposure Management (CTEM)?
Exposure Management is a cyber security framework that extends the fundamental concept of Vulnerability Management. Vulnerability Management has traditionally focused on identifying and remediating known software vulnerabilities within an IT environment. Exposure Management expands threat mitigation to a wider range of attack surfaces and prioritizes mitigation activities based on the real contextual risk that a security weakness could have on an organization’s operational resilience.
The concept of Continuous Threat Exposure Management (CTEM) was defined by Gartner in a 2022 whitepaper, Implement a Continuous Threat Exposure Management (CTEM) Program. CTEM further develops the Exposure Management approach into a continuous and iterative cyber security activity. By using an iterative process, CTEM accounts for changes to an organization’s operational IT environment and novel attacker behaviors.
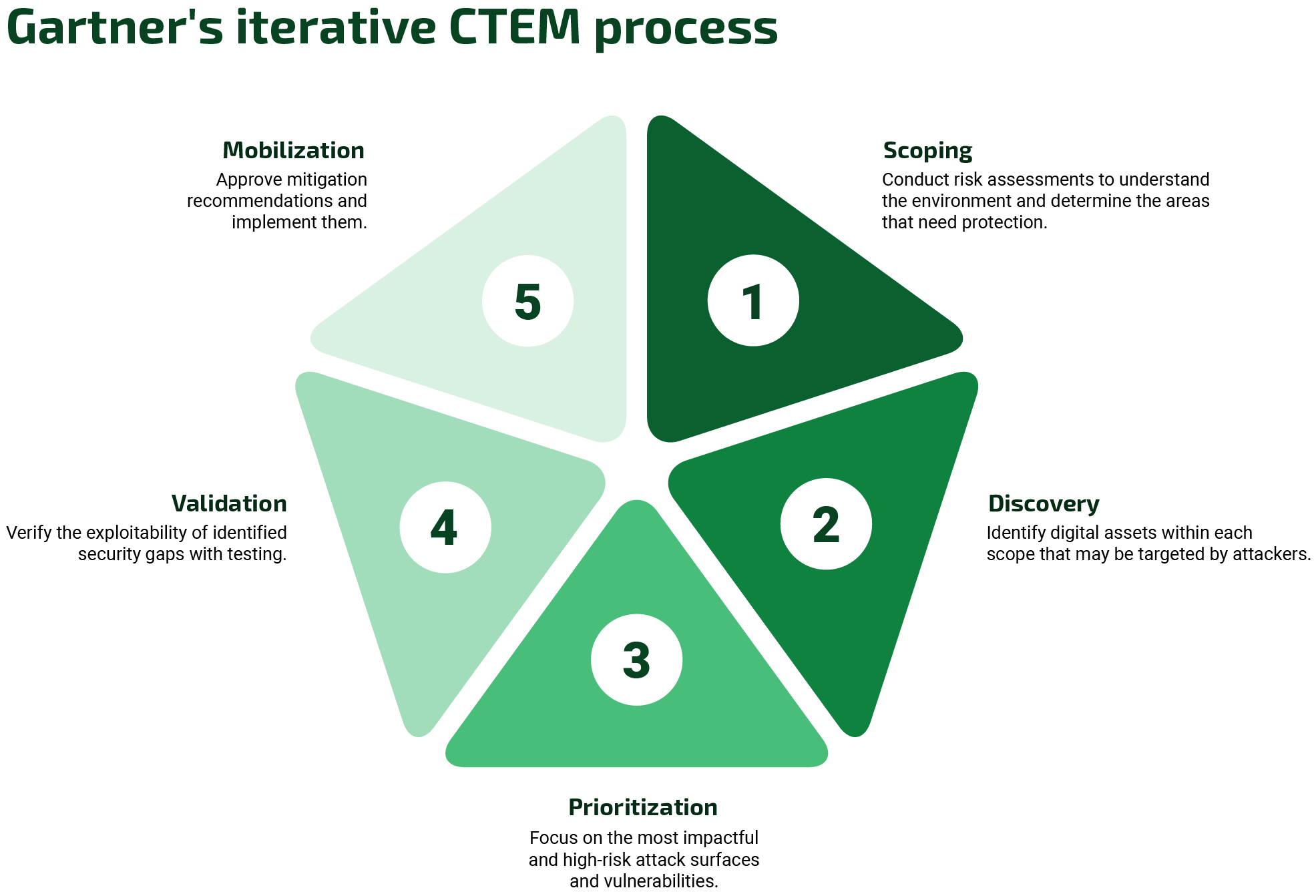
Gartner’s iterative CTEM process:
- Scoping: Conduct risk assessments to understand the environment and determine the areas that need protection.
- Discovery: Identify digital assets within each scope that may be targeted by attackers.
- Prioritization: Focus on the most impactful and high-risk attack surfaces and vulnerabilities.
- Validation: Verify the exploitability of identified security gaps with testing.
- Mobilization: Approve mitigation recommendations and implement them.
The iterative process flow of a Continuous Threat Exposure Management (CTEM) program
Test Us!
OPENVAS BASIC
Our entry-level enterprise product for 2,524 € per year
Run for cover – it’s the right reaction, even in cyberspace. But have a plan first. Vulnerability management is the answer.
You can reduce your attack surface by 99%
Exposure Management’s Role within a Comprehensive Cyber Security Program
As IT defenders look for new ways to imagine the evolving cyber threat landscape, Exposure Management has emerged as a well-established concept. Other modern frameworks for visualizing cyber security posture include Attack Surface Posture Management (ASPM), Risk-Based Vulnerability Management (RBVM), and Cyber Asset Attack Surface Management (CAASM).
While these paradigms have different names, they share some primary goals:
- Defining an organization-wide scope to identify high-risk attack surfaces
- Implementing effective security controls in a prioritized manner
- Continuously monitoring attack surfaces to ensure that existing mitigations protect against emerging security risks
Exposure Management aims to provide a holistic view of an organization’s digital risk, continuously monitor for new emerging attack surfaces, and to prioritize security efforts based on the threat to operational resilience.
Does your organization have the high-degree cybersecurity assurance it needs?
Contact Greenbone’s sales team for a product consultation and to learn more about how our products support your Exposure Management and CTEM goals!
What Is “Attack Surface” Anyway?
Attack surfaces are entry points that attackers could use to gain unauthorized access to a digital device or sensitive data. Every digital device typically has a network attack surface and host attack surface. Network attack surface refers to active network services that an attacker can interact with remotely via a network connection. This includes wireless protocols such as Wi-Fi and Bluetooth. Host attack surface refers to user accounts, applications, processes, directories, files, and other elements that an attacker could access if they were logged in to a device or in control of a service account. Other attack vectors can also be associated with a device’s attack surface, such as human and physical factors.
The Exposure Management framework for cyber security aims to consider all potential ways that an organization’s digital assets could be breached and apply appropriate security controls based on risk level. Some additional forms of attack surface are:
- Cloud Attack Surface: Cloud resources require special security considerations because they often physically exist outside of an organization’s premises and may involve third-party service providers. Improper access controls, misconfigured cloud assets, and exposed APIs are the most common vulnerabilities that impact cloud attack surface.
- Third-Party Service Providers and Supply Chain Attack Surface: When organizations depend on third parties for digital services or software an implicit trust bond is created. This dependence on security controls outside of the organization is often an inflection point for cyber breaches.
- Shadow IT and IoT Attack Surface: IoT and personal devices connected to a corporate network introduce additional cyber risk. When an organization is unaware that these devices exist it is known as Shadow IT. IoT vendors may not prioritize cyber security in their products, leaving an opportunity for attackers to gain a persistent foothold on an organization’s network. Similarly, personal devices may have rogue apps installed or be missing critical security updates.
- Human Attack Surface: Phishing and other social engineering techniques, inadequately trained employees, or even malicious insiders are all forms of human attack surface. Exploitation can result from even simple actions such as clicking on a malicious file or accidentally misconfiguring a system.
- Identity and Access Management (IAM) Attack Surface: Legitimate user and service accounts are an attractive target for adversaries because they give privileges to the credential holder. Other IAM risks include rogue accounts created by attackers for covert, persistent access, and account sprawl: when unused accounts are not deprovisioned appropriately. The principle of least privilege dictates that each account should be limited to its functional requirements and granular account segmentation can be used to isolate critical functions. Additional security measures such as Multi-Factor Authentication (MFA) and Zero-Trust Architecture (ZTA) provide additional protection to prevent unauthorized access.
- Operational Technology (OT) Attack Surface: Industrial Control Systems (ICS) and other OT environments are increasingly connected to corporate IT networks and the internet. Vulnerabilities in these systems can have significant operational and safety impacts.
- Physical Attack Surface: Physical access to unattended workstations, servers, and other devices can allow an attacker to bypass logical controls. Attackers could potentially steal a device outright or the sensitive data it contains, or tamper with hardware or software to implant malware.
Greenbone Supports a CTEM Approach To Cyber Security
Greenbone’s OPENVAS PRODUCTS help cyber defenders operationalize CTEM activities with continuous, automated discovery and reporting of vulnerabilities across multiple attack surfaces and through flexible integration with other security platforms. Greenbone’s IT security products assist with all stages of the CTEM process, from scoping, discovery, and prioritization to validation and mobilization.
Our OPENVAS SCAN can penetrate all corners of an organization’s IT infrastructure to identify risks including known CVEs and general IT misconfigurations. OPENVAS SCAN can monitor the traditional network and host attack surfaces. However, Greenbone’s support for CTEM also goes beyond simply scanning a local network for known vulnerabilities. Our products help organizations achieve resilience across many attack surfaces, including supply chain risk management, cloud infrastructure, container scanning, and more.
Frequently Asked Questions about Exposure Management
What is Exposure Management?
A cyber security activity that seeks to reduce an organization’s attack surface comprehensively across all types of digital assets and against all types of threats.
What is Continuous Threat Exposure Management (CTEM)?
A continuous, iterative process that implements the Exposure Management approach to cyber security.
Why is Exposure Management important?
Organizations need to consider all potential cyber threats across a diverse set of attack surfaces and potential risks.
Why is Continuous Threat Exposure Management (CTEM) important?
Cyber threats are highly dynamic. New attack tactics and techniques are continuously developed by adversaries and each organization’s digital business operations can evolve over time, exposing new attack surfaces. Continuous reassessment is critical for strong security assurances.
How does Exposure Management work?
Through continuous external discovery, prioritization, and guided remediation.
Is Exposure Management the same as Vulnerability Management?
No – it identifies a wider scope of risks, including external attack surfaces, cloud and SaaS, Identity and Access Management (IAM), third-party services and software supply chains, configurations, control gaps, and other potential attack paths.
Does our organization need Exposure Management if we patch regularly?
Yes – many types of exposures can still reside after software updates are applied such as misconfigurations, account and identify risks, and cloud resource sprawl.
How is prioritization determined?
Potential attack vectors should be prioritized by the business impact that exploitation could have, the probability of exploitation, reachability, and cyber security intelligence about current attacker trends.
Does Exposure Management improve security posture over time?
Yes – each iteration reduces exposure and improves an organization’s security posture.