Attack Vector Timeline
The Race to Protect from Cyber Attacks
You are being attacked, like everyone is, and it is out of our control to prevent this. No one can stop this to happen. But we protect you from the impact of cyber attacks simply by making the attacks unsuccessful even if they manage to circumvent your firewall or other defense systems. No defense system is 100% safe and it needs only one failure to result in severe damage. No one should be without defense systems, but the best defense is to be not vulnerable.
Of course, the task of making attacks unsuccessful is not a simple one. It is comprised of two central challenges: The first one is to detect an attack vector and help to close it. The second one is to do this faster than the attackers exploit your vulnerability.
So, essentially we help you win a race against the attackers. How are we doing this?
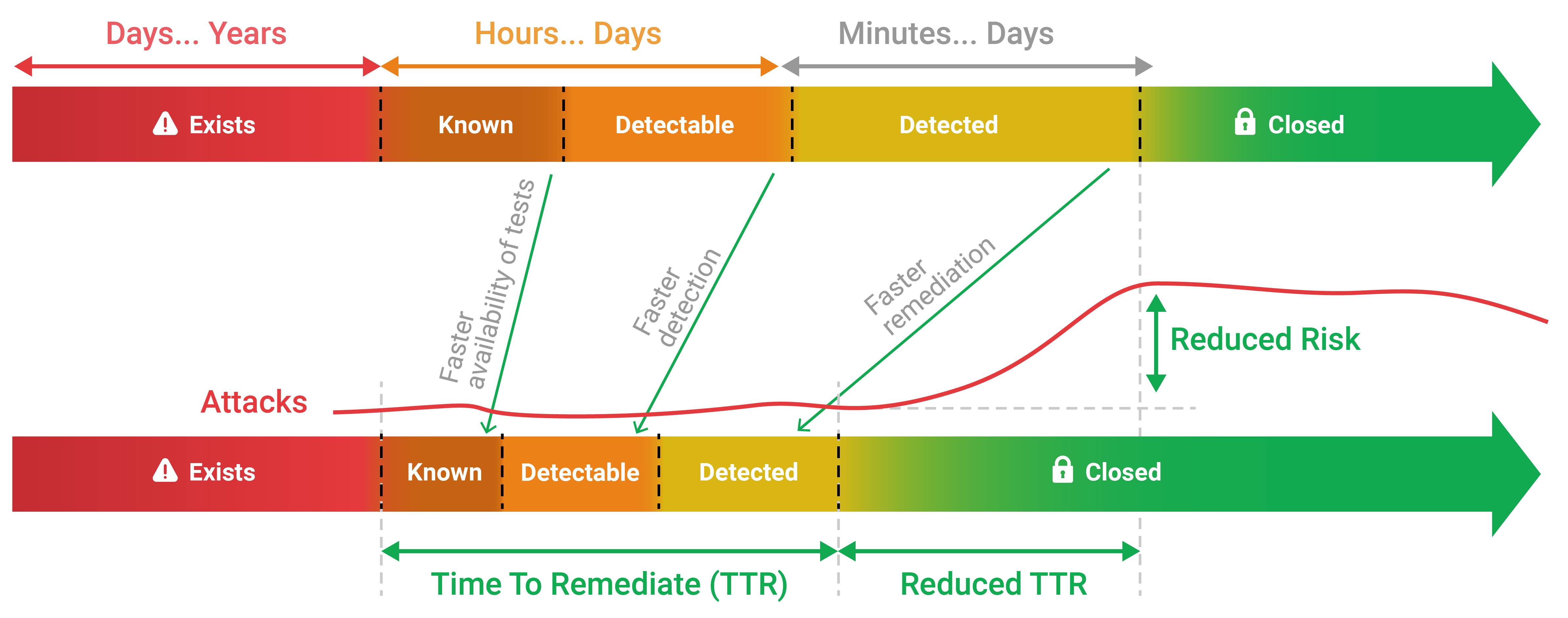
Once a vulnerability becomes known there are three things to do:
1. create a test that detects the vulnerability,
2. detect the vulnerability in case it is present in your environment,
3. close the vulnerability. So this race is a triathlon.
So, the first discipline is solely in our hands. The other 2 disciplines happen in your environment, and we support you with scanning technology and vulnerability intelligence for highest automation and prioritized detailed action plan for remediation. The attackers do almost the same, but their third discipline is exploitation not remediation.
To win the race we invest on making the availability of tests faster, improve tools to detect faster and support you for faster remediation. The goal is to come in front of the attack wave as illustrated in the chart.
Today we do have a proven and efficient process for the creation of vulnerability tests, we do collect and aggregate information about vulnerabilities and we have a full-featured scan technology. Our customers have 99% less impacts than organizations without a vulnerability management process.
But there are two unfortunate things inevitably going on: The attackers improve their tools and processes. And the number of vulnerabilities is increasingly growing. It is our job to deal with this.
In short our mission is both, simple and ambitious: Provide the best vulnerability detection.
About the Attack Vector Status over Time
| Attack Vector Status | What does it mean and what happens? | The role of Greenbone |
| Exists | A product with an vulnerability starts go into productive use. It is not being exploited for attacks because no one is aware of it. |
Greenbone recommends to use tools and processes for the software development that at least prevent standard programming mistakes. We also recommend a security-centric process when integrating third party software modules. This is what we do for our own products. |
| Known |
Someone finds a vulnerability in the product. First trial exploits may occur, but the systematic large scale exploitation will usually need some time to happen. In most cases the finder is a good guy but in rare cases a bad guy keeps the finding secret for own (criminal) exploitation purpose or for selling the knowledge to an organization with an exploitation agenda. Once exploitation happens, the good guys will of course find out and share the knowledge. |
Greenbone monitors various places where discussions about newly discovered vulnerabilities occur. We begin implementing tests for our customers that can identify the presence of the vulnerability. Even if there is no solution yet, this helps the customers with isolation or other remediation measures until the vendor can present a viable solution. |
| Detectable | A method exists that allows a user to detect the presence of the vulnerability in the IT infrastructure. | Greenbone creates one or more vulnerability tests for customers to detect the vulnerability and provide all information known so far. The information are continuously updated from now own. |
| Detected |
The user detected the vulnerability in the IT infrastructure. With this awareness decisions can be made to resolve the attack vector. In practice this phase is influenced by the presence of multiple vulnerabilities to prioritize, lack of remediation resource or lack of vendor solution. |
Greenbone provides support for prioritization directly with the actual scan report but also via managed operational services. |
| Closed | The user applied a solution and is not vulnerable to this attack vector anymore. | Greenbone’s business is to help users to get to this point as early as possible. Our processes, tools and services are all geared to minimize the duration of the phases “Known”, “Detectable” and “Detected”. |
This Could Also Interest You
From CVE to Management Feed: The Vulnerability Timeline
Here you will find the timeline for the majority of known vulnerabilities – from their discovery to the release of vulnerability tests to fix them.