Greenbone Is Preparing For The Post Quantum Age
Q-Day marks the moment when quantum computers will render classical cryptography standards obsolete. The risks posed by quantum computers demand a migration to Post Quantum Cryptography (PQC). Greenbone is proactively preparing for this future—upgrading our internal infrastructure, auditing partners, and enhancing the OPENVAS SECURITY INTELLIGENCE platform with upgraded detection and new auditing features. The goal is to ensure that our digital operations and our customers’ can achieve Post Quantum Security (PQS). Greenbone is becoming quantum-ready—inside and out. We are taking vulnerability detection and management to a new level—the quantum level.

Quantum computing promises unprecedented and almost unfathomable computing power [1]. The quantum singularity (known as “Q-Day”) represents the transition from a theoretical quantum threat to real, operational risk—when a quantum enabled adversary can cause irreparable harm to an organization [2][3]. For high-security applications, Germany’s BSI works under the hypothesis that Q-Day will become relevant in the early 2030s [4]. Efforts to develop and standardize PQC have been underway for more than a decade. While quantum R&D has been a global effort, NIST is leading the charge to finalize global standards by 2027 [5][6].
The primary goal for cyber defenders is to achieve PQS by migrating high-security systems to the new globally qualified PQC standards. In some cases, this requires phasing out support for pre-quantum algorithms. In other cases, it simply means increasing the key-length for established classical algorithms. By upgrading to PQS standards, organizations will be ready in advance of Q-Day’s arrival.
As both a consumer of digital products and a vendor of the OPENVAS SECURITY INTELLIGENCE platform, Greenbone is preparing for Q-Day and the post quantum age. Our responsibilities are two-fold: firstly, our internal operations and digital products must be resilient against attack. Secondly, we must outfit our security products with new capabilities; adding new detection, auditing, and reporting capabilities to support our customers’ push for PQS compliance. Read on to learn about the PQS future and how Greenbone is preparing for the post quantum age!
Greenbone Is Getting Quantum Ready – Inside and Out
As a vendor of digital products, Greenbone must implement the established PQC standards to protect both our own IT operations and help our customers defend their own. Internally, Greenbone’s journey toward PQS is governed by several factors. Among these are our commitments to the highest standards for IT security; our ISO/IEC 27001 and ISO 9001:2025 achievements [1]. Our exceptional detection coverage also motivates our efforts to maintain our leadership role.
Technical guidelines published by accredited government bodies, such as the TR-02102 series from Germany’s BSI, define the scope of the PQS landscape; other national governments have published their own forecasts and guidelines [2][3][4][5][6]. Our team at Greenbone analyzes such forecasts to architect PQS compliance across our digital infrastructure and plan upgrades to our OPENVAS SECURITY INTELLIGENCE line of products and the OPENVAS ENTERPRISE FEED. Our efforts also extend to auditing third-party ICT providers to ensure full compliance across our digital operations. As the quantum threat advances, we remain committed to keeping pace with evolving PQS standards.
Upgrading OPENVAS SCAN’s Detection and Compliance Profiles
As an industry-leading vulnerability scanning and management platform, Greenbone needs to detect non-compliance with established PQS standards. To meet these expectations, we are adding new detection tests to our OPENVAS ENTERPRISE FEED. This includes new NASL scripts for auditing the implementation of PQC and provisioning a dedicated PQS compliance scan. Other upgrades include a Cryptography Bill of Materials (CBOM) for tracking all identified encryption methods per IT asset, providing improved visibility, and specialized reporting in a structured format.
These upgrades will outfit our customers with clear proof of PQS compliance and report non-compliant services. Following the guidance from NIST CSWP 48, OPENVAS SCAN detection will support network services, cloud services, end-user systems and servers, applications, and software packages and libraries. By implementing discovery for PQS, organizations can achieve compliance with the IT security standards that govern their operational requirements.
OPENVAS SCAN will detect PQS compliance for many common protocols, including:
|
Protocol / Family |
Industry Usage |
Quantum Threats |
|
TLS |
DNS over HTTPS (DoH) & DNS over TLS (DoT) provide secure resolution; TLS/mTLS underpins secure communications at OSI application layer. |
Certificate private key compromise, passive decryption of recorded TLS sessions after quantum breakthrough, and impersonation through signature forgery. |
|
SSH |
Enabling secure network channel for operating system administration, file transfer, and remote execution. |
Client credential exposure, compromise of user key material, and loss of forward secrecy through quantum key recovery. |
|
IPSec/IKEv2 |
A VPN protocol suite that provides network-layer encryption and authentication via Encapsulating Security Payload (ESP) and Authentication Header (AH). |
The exchange is handled by IKE using RSA or ECDH, which are vulnerable to quantum attacks using Shor’s algorithm. |
|
Kerberos |
Authentication system using symmetric cryptography for secure key exchange between clients and services. |
Post-quantum attacks could break pre-shared keys or compromise ticket-granting services if weak encryption is used. |
|
PGP |
Enables end-to-end e-mail encryption and digital signing between individuals and organizations. |
Compromise of private keys through quantum attacks could expose historical encrypted correspondence. |
|
OAUTH/OpenID Connect |
Provides delegated authorization and federated identity management across web applications and APIs. |
Exposure of tokens and signatures to quantum attacks could allow unauthorized access or identity forgery. |
|
DNSSEC |
Provides integrity and authenticity for DNS responses through cryptographic signing. |
Quantum attacks will break RSA/ECDSA-based DNSSEC signatures, allowing domain spoofing or redirection. |
|
S/MIME |
Encrypts and signs e-mail messages for enterprise communication security. |
Quantum attacks could decrypt stored e-mails and forge sender signatures if RSA or ECC keys are used. |
|
Hardware Security Modules (HSMs) |
Provide tamper-resistant cryptographic key storage and secure operations for PKI and signing. |
Vulnerable to stored-key extraction if classical algorithms (RSA, ECC) are compromised by quantum computing. |
Timeline for Implementing PQS Standards
The UK’s National Cyber Security Centre (NCSC) has provided a generalized timeline for migrating IT infrastructure to PQS compliant standards [1].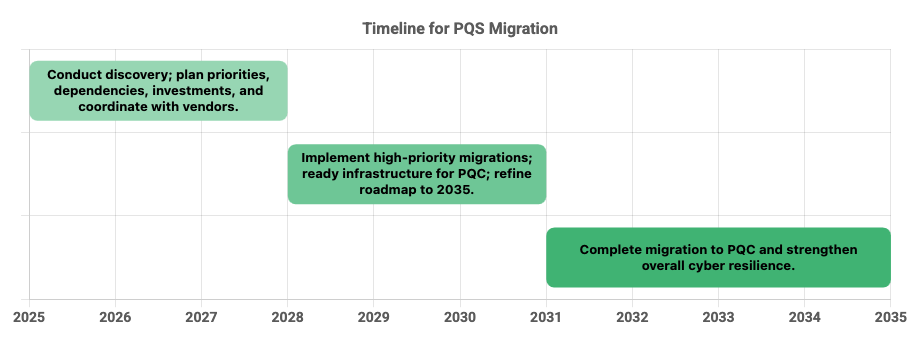
Figure 1: A generalized timeline for migrating to PQS
|
Timeline |
Activities |
|
To 2028 |
Conduct discovery and assessment of all cryptographic implementations. Develop a migration plan with priorities, dependencies, investments, and hardware root of trust updates. Communicate requirements to suppliers and third-party ICT providers.
|
|
From 2028 to 2031 |
Implement high-priority migrations and prepare infrastructure for PQC readiness. Refine the roadmap for full migration by 2035. |
|
From 2031 to 2035 |
Finalize the transition to PQC while strengthening overall cybersecurity resilience across systems. |
The Impact of Quantum Compute on Cryptographic Primitives
Cryptographic primitives are the basic building blocks of secure digital communication. Each cryptographic function has a different role in maintaining safe online transactions: remote authentication, ensuring the confidentiality, integrity, and authenticity of data-in-transit and data-at-rest, and non-repudiation. Although well-established standards exist for defending against classical silicon-based cryptographic attacks, adversarial quantum technologies are expected to significantly impact their resilience. As a result, quantum capable adversaries will be able to conduct covert espionage campaigns and digital impersonation of both human and non-human entities against mechanisms that don’t meet new PQS standards.
Further complicating security posture, Harvest Now Decrypt Later (HNDL) attacks allow adversaries to record messages now and decrypt them later — when the attacker obtains sufficiently advanced quantum technology. HNDL attacks make timely implementation of PQC more important, especially for highly sensitive data. According to the NIST Post-Quantum Cryptography Standardization, here’s how quantum computers are expected to impact each cryptographic primitive:
The Impact of Q-Day on Symmetric Encryption (AES, ChaCha20)
Threat level: Moderate — reduced effective key strength
Quantum computers using Grover’s algorithm are capable of searching a key space in roughly √N time, instead of N required by conventional brute force cryptographic attacks [1]. This effectively halves the strength of symmetric key security; a 128-bit key offers only ≈64 bits of post-quantum security, and a 256-bit key results in ≈128 bits.
The following table provides an overview of how symmetric keys are affected by Grover’s algorithm [2][3][4].
|
Algorithm / Key Length |
Classical Security |
Quantum-Equivalent (Grover’s algorithm) |
PQS Status |
|
AES-128 |
128-bit security |
≈ 64-bit equivalent |
Vulnerable — not sufficient for PQS. |
|
AES-192 |
192-bit security |
≈ 96-bit equivalent |
Vulnerable — not sufficient for PQS. |
|
AES-256 |
256-bit security |
≈ 128-bit equivalent
|
The minimum recommended bit strength for PQS. |
|
ChaCha20 |
256-bit security |
≈ 128-bit equivalent |
Comparable to AES-256. |
Furthermore, while experts agree that current encryption algorithms like AES become sufficiently quantum-resistant by simply increasing the bit-strength of secret keys, this approach places increased burden on classical silicone-based CPUs. Therefore, there is a need to develop new algorithms that are both efficient for silicon-based computing and robust against quantum-based cryptographic analysis.
The Impact of Q-Day on Asymmetric Encryption and Digital Signatures (RSA, DSA, ECC)
Threat level: Severe — completely broken
Shor’s algorithm allows quantum computers to efficiently factor large integers and solve discrete logarithms [1][2] — the mathematical foundation of RSA, the Digital Signature Algorithm (DSA), and Elliptic Curve Cryptography (ECC). Therefore, the classical algorithms relied upon for asymmetric encryption and digital signatures must be completely replaced with quantum resilient ones. In August 2024, NIST published FIPS 204 to finalize ML-DSA (CRYSTALS-Dilithium) and FIPS 205 for SLH-DSA (SPHINCS+) as US federal standards. FIPS 206 to formally standardize FN-DSA (Falcon) is in development [3][4][5].
The following table provides an overview of how classical and PQC asymmetric cryptographic algorithms are affected by Shor’s algorithm [6][7][8].
|
Algorithm |
PQS Status |
|
RSA (1024 / 2048 / 4096-bit)
|
Vulnerable — use only in hybrid transition period.
|
|
Digital Signature Algorithm (DSA)
|
Vulnerable — not recommended even in hybrid configurations.
|
|
ML-DSA
|
NIST-standardized for digital signatures. Recommended for general-purpose authentication.
|
|
FN-DSA
|
NIST-standardized for digital signatures. Recommended for general-purpose authentication.
|
|
SLH-DSA
|
NIST-standardized for digital signatures in high-security environments.
|
The Impact of Q-Day on Real-Time Key Establishment
Threat level: Severe — Diffie–Hellman and ECC are broken
Since pre-quantum real-time key establishment mechanisms like Diffie–Hellman (DH) and Elliptic-Curve Diffie–Hellman (ECDH) rely on public-key cryptography, they are also impacted by Shor’s algorithm. Therefore, these classical mechanisms must be replaced by post-quantum Key Encapsulation Mechanisms (KEM). By definition, KEM differs from other key exchange mechanisms because one party generates a random symmetric key, then encapsulates it using the other party’s public key. Contrastingly, in DH and ECDH, both sides independently compute part of the final shared symmetric key and both sides are responsible for combining these parts into a final shared key.
Hybrid key exchanges are preferred during the transitional phase towards full post-quantum key establishment. Hybrid key exchanges employ both a classical algorithm such as ECDH and a post-quantum KEM. That way, even if an attack is discovered for one algorithm, session establishment remains secure.
In August 2024, NIST finalized FIPS-203 standardizing ML-KEM (based on the CRYSTALS-Kyber algorithm) for quantum-resilient key establishment. Most recently, in 2025 NIST added the Hamming Quasi-Cyclic (HQC) algorithm to the list of PQS key establishment standards [1].
The following table describes the quantum threat to classical real-time key establishment mechanisms, and the PQS compliant hybrid, and ML-KEM algorithms [4][5][6].
|
Algorithm |
PQS Status |
|
Diffie–Hellman (DH) |
Vulnerable — replace or use only in hybrid with a PQ KEM during transition. |
|
Elliptic-Curve Diffie–Hellman (ECDH) |
Vulnerable — replace or use only within a hybrid ECDH+PQ KEM until full PQ migration. |
|
Hybrid key establishment (e.g., ECDH + ML-KEM) |
Strongly recommended during migration to hedge against unforeseen breaks. Remains secure if one component is broken. |
|
ML-KEM (512, 768, and 1024 bit strengths) |
NIST-standardized for key establishment. ML-KEM-512 is recommended for classical 128-bit level use cases. ML-KEM-768 is recommended for higher security in enterprise profiles and ML-KEM-1024 is recommended for the highest security scenarios. |
|
HQC (128, 192, and 256 relative bit-strengths) |
NIST-standardized for key establishment. HQC-128, HQC-192, and HQC-256 correspond to NIST security levels 1, 3, and 5. Each provides quantum-resilient protection roughly equivalent to AES-128, AES-192, and AES-256 security strengths, respectively. |
The Impact of Q-Day on Hashing Algorithms (SHA-2, SHA-3)
Threat level: Low — mildly weakened
Quantum attacks, such as Grover’s and the Brassard–Høyer–Tapp (BHT) algorithms, effectively cut collision resistance to roughly one-third of its classical strength [1]. Similar to symmetric key encryption, no special functions have been developed with intrinsic properties for PQS. Therefore, the effective strategy will be to increase output length. For hashing, bit strength refers to how many computational operations (on average) are required to break either preimage resistance or collision resistance [2].
The following table provides an overview of how hashing algorithms are impacted by Grover’s algorithm using a quantum computer [3][4][5].
|
Hash Function |
Quantum-Equivalent (Grover’s algorithm) |
Status |
|
SHA-256 |
≈ 85-bit collision equivalent
|
Acceptable short-term, but not recommended for long-term PQS |
|
SHA-384 |
≈ 128-bit collision equivalent |
Medium-term PQS resilience. |
|
SHA-512 |
≈ 171-bit collision equivalent |
Recommended baseline for PQS resilience. |
|
SHA-3-256 |
≈ 85-bit collision equivalent |
Medium-term PQS resilience. |
|
SHA-3-512 |
≈ 171-bit collision equivalent |
Recommended as the most resilient hash function for PQS. |
Summary
As Q-Day approaches, organizations must migrate to new PQC standards to maintain resilience in the form of privacy for their online communication and data loss protection. Greenbone is taking decisive steps to achieve full PQS compliance—modernizing internal operations, aligning with established standards, and equipping our OPENVAS SECURITY INTELLIGENCE platform with PQC detection and robust compliance auditing tools. Greenbone is becoming quantum-ready—inside and out. We are taking vulnerability detection and management to a new level—the quantum level.



