More than 100,000 Vulnerability Tests in the Greenbone Security Feed
The goal of vulnerability management is to detect all security gaps in an IT network before an attacker does so. The Greenbone Security Feed (GSF) provides the vulnerability tests (VTs) that the scanner of the Greenbone solutions performs for this purpose. As a component of the Greenbone Security Manager (GSM) and the Greenbone Cloud Services (GCS), it is updated daily and provides protection against major and well-known vulnerabilities such as SUPERNOVA, BlueKeep and PrintNightmare.
We are happy to announce that the success story is growing steadily and that since this month our Greenbone Security Feed contains more than 100,000 vulnerability tests!
Let’s take a look at the history of the feed.
In 2005, the development of the Nessus vulnerability scanner decided to stop working under open source licenses and switch to a proprietary business model. By that time, members from Intevation and DN-Systems – the two companies that would later found Greenbone – were already contributing developments to Nessus. In 2006, several forks of Nessus were created in response to the discontinuation of the open source solution. Of these forks, only one remains active: OpenVAS, the Open Vulnerability Assessment System.
In late 2008, Greenbone was formed to push OpenVAS. In the same year, two other companies became active: Secpod from India and Security Space from Canada. Both focused on providing vulnerability testing and partnered with Greenbone to create a reliable and up-to-date feed of vulnerability tests.
This started with the removal of source code and vulnerability tests where the license was unclear or incompatible. Several thousand vulnerability tests were eliminated to get a clean baseline with just under 3000 vulnerability tests at the time.
Shortly after, the content of the feed grew rapidly and steadily to over 10,000 vulnerability tests. 50,000 tests were then contained in the feed after about 8 years of development in 2016. The next 50,000 followed after only 5 more years and represent the current state with more than 100,000 vulnerability tests.
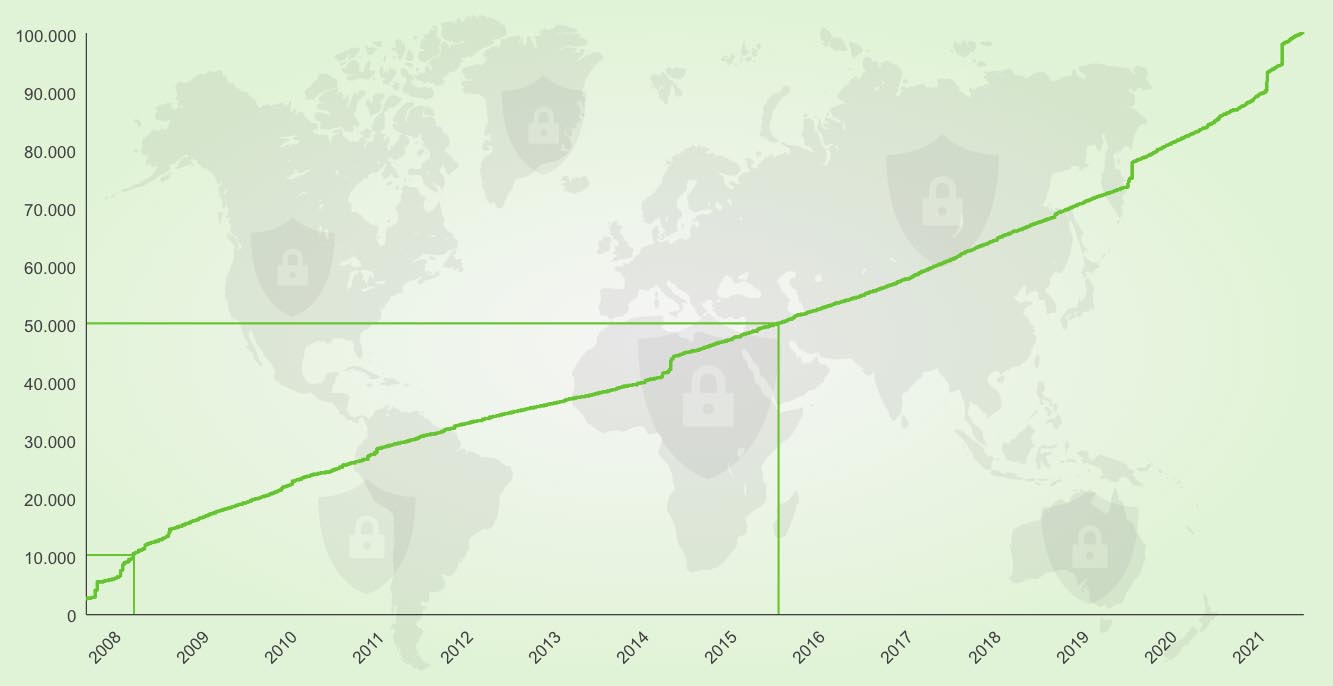
Number of VTs over time
How Is the Feed Composed Anyway?
It is also interesting to see how these 100,000 vulnerability tests in the feed are put together. In our SecInfo Portal, you can easily take a look at all the included tests yourself.
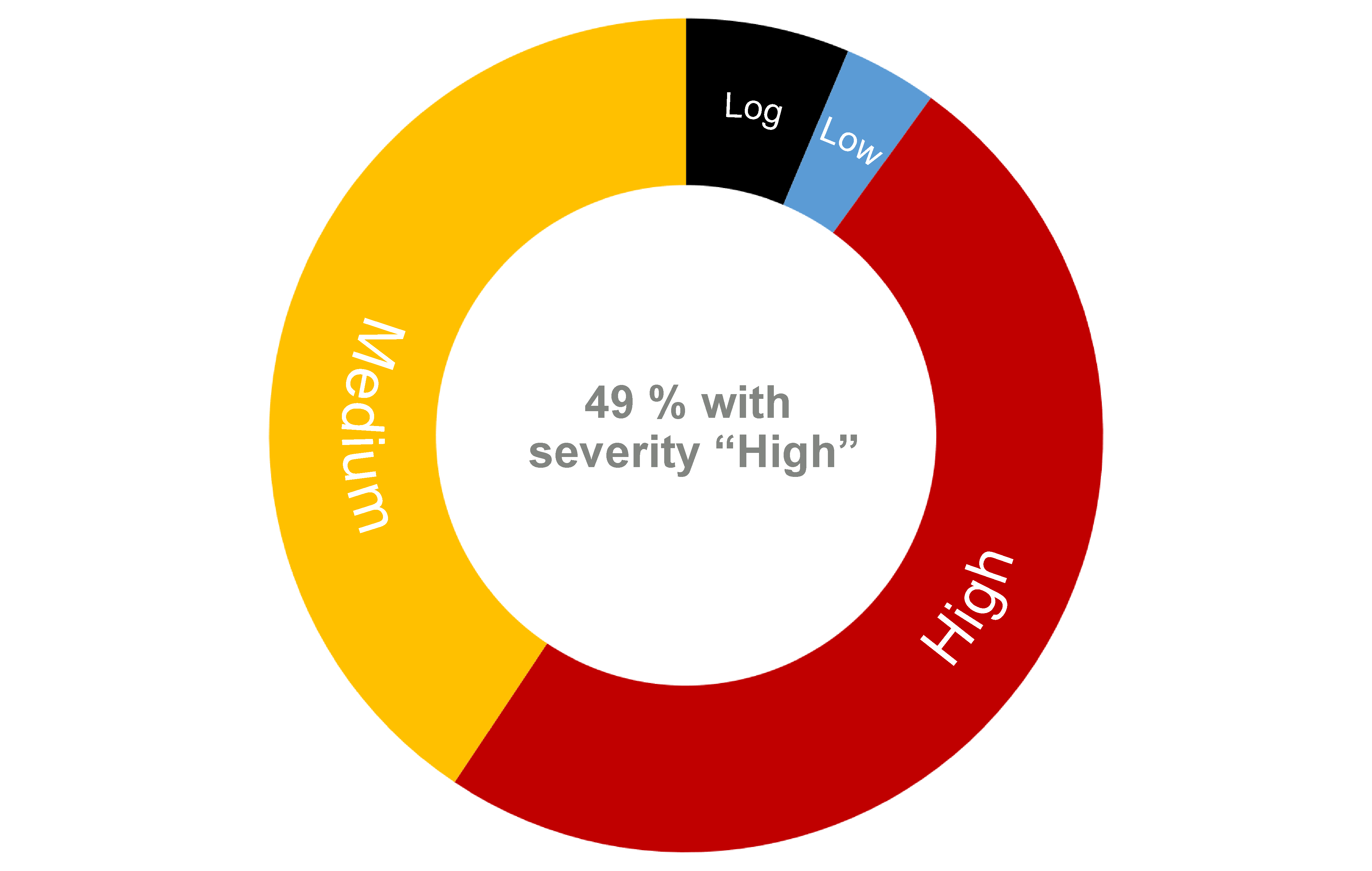
About half of the tests detect vulnerabilities with a high severity class – i.e., with a severity between 7.0 and 10.0. Another 40,000 tests such with the severity class “Medium” (severity 4.0 to 6.9).
Vulnerabilities for the same area are grouped into families. Among the largest families of vulnerability tests are mainly those for local security checks, i.e., authenticated scans. In these, the target is scanned both from the outside via the network and from the inside using a valid usage login. Thus, more details about vulnerabilities can be found on the scanned system. Vulnerability tests for such authenticated scans already account for over 60,000 tests. The largest VT families with a total of almost 30,000 vulnerability tests are “Fedora Local Security Checks” and “SuSE Local Security Checks”.
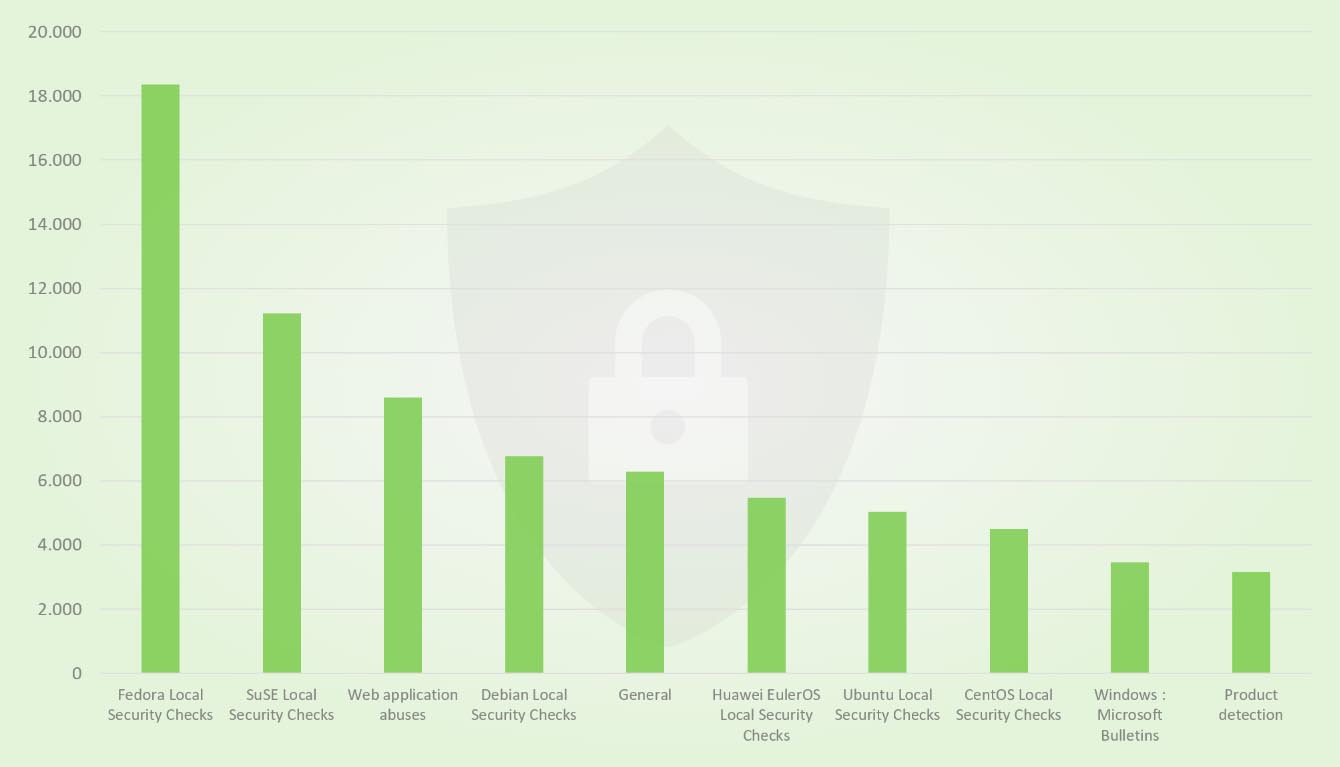
Number of VTs in the top 10 VT Families
Globally Known Vulnerabilities Are also Covered
The general public is unaware of many vulnerabilities. But every now and then, particularly significant and spectacular cyber attacks make it into the media – especially when many large companies or governments are affected.
Greenbone reacts immediately when such incidents become known and starts developing a corresponding vulnerability test. Such notable vulnerabilities in recent years include Heartbleed (2014), POODLE (2014), DROWN (2016), Meltdown (2018), Spectre (2018), BlueKeep (2019) and PrintNightmare (2021). Most people probably also particularly remember the Solarwinds attack in 2019 and 2020. The attackers had exploited a previously unknown vulnerability to inject the malicious webshell “SUPERNOVA”.
All of these vulnerabilities can be detected via tests in the Greenbone Security Feed.
In the future, we will continue to work on expanding the scope of our feed to provide users with the opportunity to detect vulnerabilities at an early stage and not give attacks a chance. So with our solutions constantly updated to cover the latest and most critical vulnerabilities, you can relax. The next 100,000 vulnerability tests will follow – stay tuned!