January 2026 Threat Report: Off to a Raucous Start
So far, 2026 is off to a raucous start. The number of critical severity vulnerabilities impacting widely deployed software is staggering. Defenders need to scan widely and scan often to detect new threats in their infrastructure and prioritize mitigation efforts based on the potential impact to business operations, privacy regulations, and other compliance responsibilities. Defenders seeking to detect and protect can try Greenbone’s flagship OPENVAS BASIC for free, including a two-week free trial of the OPENVAS ENTERPRISE FEED.
This month, the World Economic Forum’s report Global Cybersecurity Outlook 2026 was released. The annual report surveys the top concerns of global cyber security and business leaders. This edition reported that 58% of surveyed executives perceive increased risk of exploitation via software vulnerabilities in 2026. Fraud, ransomware, and supply chain disruptions were ranked as the top impact concerns, while AI, phishing, and software vulnerabilities were considered the most concerning attack vectors. Respondents who considered their organizations to have high cyber resilience ranked exploitation of software vulnerabilities as the second most concerning threat, while medium and insufficient-resilience organizations ranked it third.
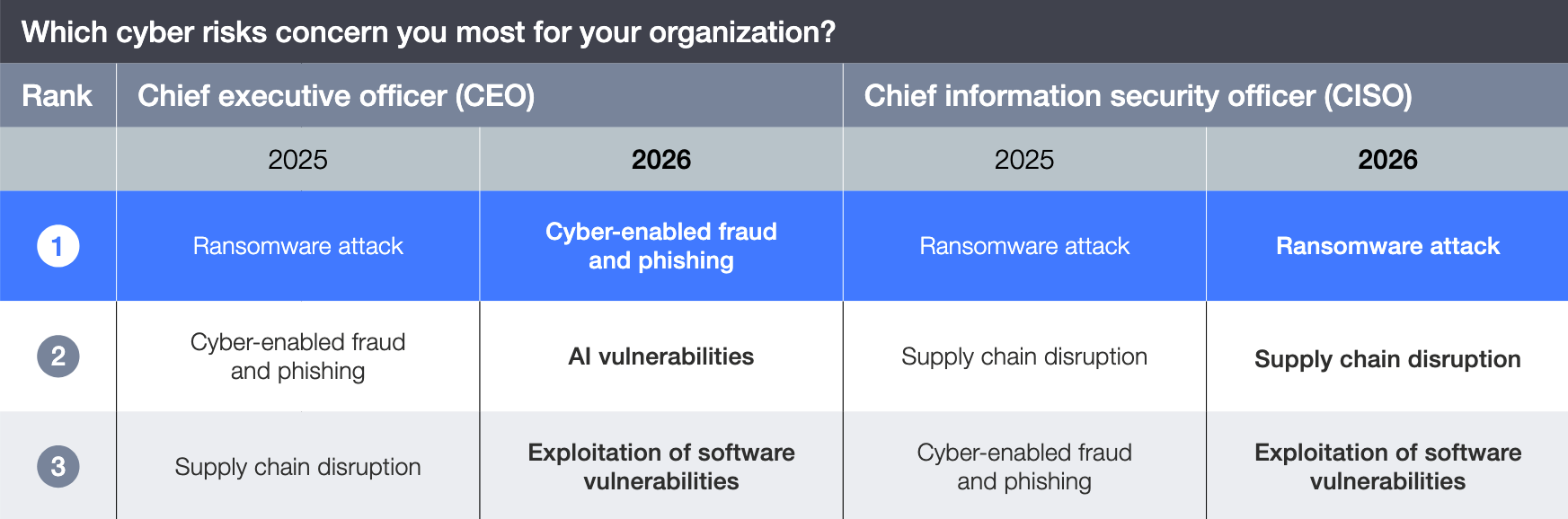
Figure 1: Evolving cyber risk concerns for CEOs and CISOs between 2025 and 2026. (Source: WEF Global Cybersecurity Outlook 2026)
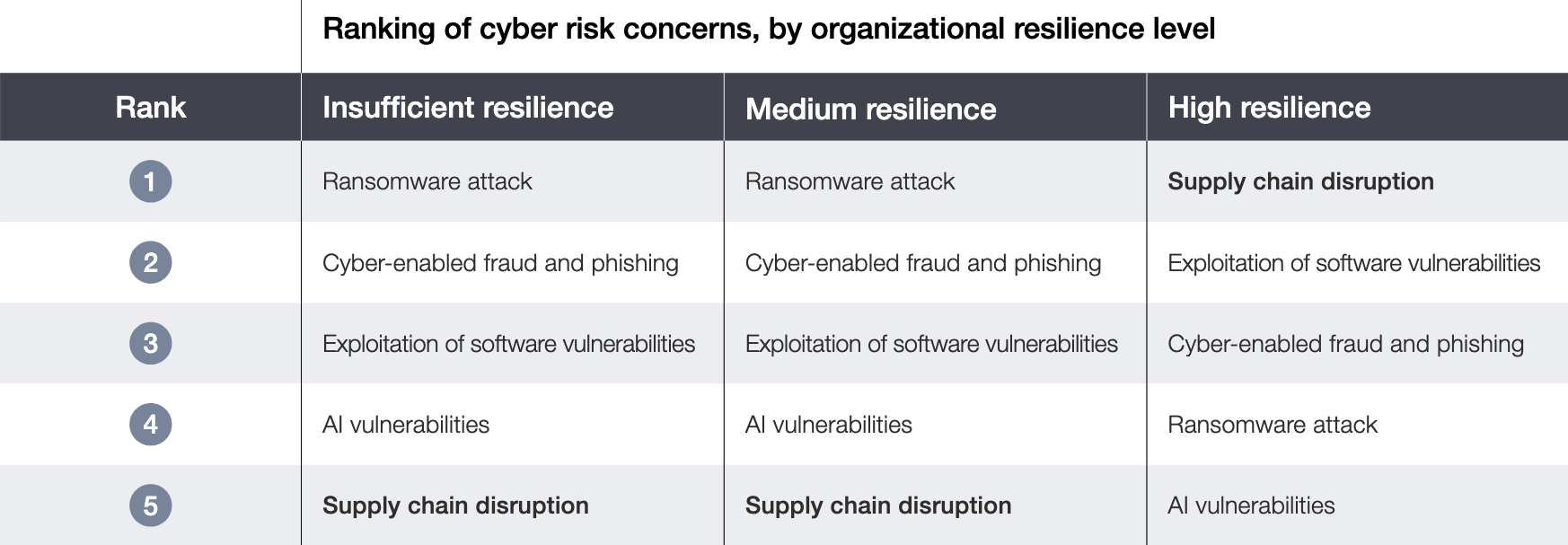
Figure 2: Top cyber risk concerns by cyber resilience level. (Source: WEF Global Cybersecurity Outlook 2026)
The survey included 873 participants from 99 countries, including C-suite executives, academics, civil society, and public-sector cybersecurity leaders. With these sentiments for 2026 in mind, let’s review some of the most high-risk software vulnerabilities from January.
High Alert: Max-Severity HPE OneView Actively Exploited
CVE-2025-37164 (CVSS 9.8, EPSS ≥ 99th pctl) was published in mid-December 2025 and added to CISA’s Known Exploited Vulnerabilities (KEV) list in early 2026. The flaw allows an attacker to gain unauthenticated remote code execution (RCE) on HPE OneView prior to version 11.00 and HPE Synergy Composer appliances that expose OneView. CVE-2025-37164 is classified as a Code Injection flaw [CWE-94]. The root cause is a REST API endpoint: /rest/id-pools/executeCommand. Submitted commands are executed with high-level privileges but without authentication.
HPE OneView is a platform for centralized management of HPE data center infrastructure. Therefore, exploitation can provide attackers with control over network infrastructure, device firmware, and lifecycle management. Full technical details and several proof-of-concept (PoC) exploits exist [1][2][3], increasing the risk. Numerous national CERT alerts have been issued globally [4][5][6][7][8][9][10][11]. Greenbone’s OPENVAS ENTERPRISE FEED includes remote banner detection for defenders to identify affected systems. Users should apply the security hotfix for HPE OneView versions 5.20 trough 10.20 with urgency.
Critical Cisco Unified CM Flaw Actively Exploited
CVE-2026-20045 (CVSS 9.8, EPSS ≥ 75th pctl) is an unauthenticated RCE flaw affecting multiple Cisco products including Unified Communications Manager (CM), Unified CM Session Management Edition (SME), Unified CM IM & Presence Service, Cisco Unity Connection, and Webex Calling Dedicated Instance. The root cause is improper validation of user-supplied HTTP input [CWE-20] leading to code injection [CWE-94]. Successful exploitation grants user-level access followed by privilege escalation to root, resulting in full system takeover.
Cisco considers the flaw actively exploited, and it has been added to CISA KEV. Mass scanning activity has also been reported. No PoC exploit is publicly available, but Cisco networking devices are often targeted in high-profile hacks [1][2]. Multiple national CERT alerts have been issued globally [3][4][5][6][7][8][9][10][11].
Greenbone’s OPENVAS ENTERPRISE FEED includes separate vulnerability tests for Unified CM [12] and Unified CM IM&P [13]. No workarounds can mitigate this flaw. Users should upgrade to a fixed software release or apply a patch. See the vendor’s security advisory for more information.
Microsoft: Newly Exploited and Critical Out-of-Band Updates
Microsoft’s January 2026 patch release published 124 CVEs, eight classified as “Exploitation More Likely”. Two of the new CVEs were quickly tagged as actively exploited and added to CISA KEV [1][2]. Microsoft also released out-of-band (OOB) security patches for Windows 11 and Windows Server [3][4]. Greenbone’s OPENVAS ENTERPRISE FEED regularly publishes detection tests for CVEs in Microsoft’s monthly patch cycle and out-of-band security updates [5].
New high-risk CVEs affecting Microsoft products include:
- CVE-2026-20805 (CVSS 5.5): A flaw in Microsoft Windows Desktop Window Manager that allows an authorized attacker to leak sensitive memory information [CWE-200]. The root cause is exposure of user-mode memory addresses via Advanced Local Procedure Call (ALPC). The flaw enables leakage of small but security-relevant memory fragments that can be chained with other vulnerabilities to bypass protections such as ASLR. Exploitation may allow full system compromise. CISA has added the flaw to its KEV list. However, no public PoC or ransomware activity have been reported. Microsoft distributed a fix for CVE-2026-20805 in its January 2026 cumulative updates.
- CVE-2026-21509 (CVSS 7.8): An unauthorized local attacker can bypass Microsoft Office security features by exploiting reliance on untrusted inputs [CWE-807]. The flaw impacts Microsoft 365 and Microsoft Office 2016, 2019, and 2021. CISA has added the flaw to its KEV list but no public PoC is available. CVE-2026-21509 can be mitigated by installing the emergency patch or implementing registry-based controls [5][6].
- CVE-2026-20952 and CVE-2026-20953 (both CVSS 8.4): Both flaws enable RCE via social engineering attacks leveraging trojanized Office documents. Exploitation does not require the target to open a malicious file; the flaw can be triggered via the Preview Pane. These CVEs are not reported as actively exploited and no public PoC exploits are yet available. Patches are available in Microsoft’s January 2026 cumulative updates.
Adobe ColdFusion Requires Critical Patches Amidst Active Attack Campaigns
Adobe has patched a critical RCE flaw in ColdFusion versions 2025 and 2023 introduced by dependency on Apache Tika’s CVE-2025-66516 (CVSS 9.8, EPSS ≥ 88th pctl). The flaw in Apache Tika was published in December 2025. Greenbone includes a remote banner check for affected ColdFusion products as well as detection for other enterprise software products affected by CVE-2025-66516. The OPENVAS ENTERPRISE FEED also includes detection for all ColdFusion CVEs published in Adobe’s December 2025 patch release. Greenbone’s ENTERPRISE FEED also includes detection for 10 ColdFusion CVEs included in a new exploitation campaign that occurred over the holidays [1][2][3][4][5][6][7][8][9][10][11]. The reported mass exploitation event targeted ColdFusion and other enterprise software applications.
CVE-2025-68645: Zimbra Collaboration Suite (ZCS) Actively Exploited Again
CVE-2025-68645 (CVSS 8.8, EPSS ≥ 96th pctl) impacting Zimbra Collaboration Suite (ZCS), published in late December 2025, is now considered actively exploited by CISA. The flaw allows unauthenticated remote attackers to perform local file inclusion against ZCS 10.0 and 10.1. The root cause is improper request parameter handling in the RestFilter servlet of the Webmail Classic UI. This allows arbitrary files to be uploaded into the WebRoot directory such as web shells, potentially resulting in arbitrary RCE.
CVE-2025-68645 is being used in targeted, reconnaissance-driven attack campaigns. A public PoC can be found via Google search, but seems to have been removed from GitHub. ZCS has an extensive history of exploitation, often in ransomware attacks.
Greenbone’s OPENVAS ENTERPRISE FEED has included remote banner checks [1][2] prior to the disclosure of CVE-2025-68645, and now includes an active check for affected ZSC installations. Known affected versions include Zimbra Collaboration Suite 10.0.0 through 10.0.17 and 10.1.0 through 10.1.12, with the issue resolved in versions 10.0.18 and 10.1.13, released in early November 2025. Users who have not patched should do so immediately.
Gogs Self-Hosted Git Server Targeted in Mass Exploitation Attacks
CVE-2025-8110 (CVSS 8.8, EPSS ≥ 96th pctl) is a path traversal flaw [CWE-22] that allows authenticated attackers to achieve RCE against the Gogs self-hosted Git service. The root cause is improper symbolic link handling in the PutContents file update API which can be leveraged to overwrite arbitrary files outside the targeted repository. CVE-2025-8110 is considered a bypass of CVE-2024-55947 (CVSS 8.8) and requires only low-level permissions to create a repository for exploitation. Gogs does not need to be internet-facing for exploitation. Malicious insiders with access to Gogs instances hosted on a local network also represent a significant threat.
CVE-2025-8110 is being actively exploited in automated mass exploitation campaigns and has a full technical description and public PoC exploit kit. Historically, Gogs has a very high rate of exploit development for published CVEs. CVE-2025-8110’s timeline for disclosure and mitigation includes 6 months of active exploitation while patches remained unavailable. Exploitation was first observed in mid-2025, and the vulnerability was responsibly disclosed to maintainers on July 17, 2025. The CVE was only later published on December 10th, 2025 while still unpatched. Inspection of the Gogs release indicates patches became available on January 23, 2026 in Gogs v0.13.4. The OPENVAS ENTERPRISE FEED has included remote banner detection for vulnerable instances since initial publication.
Fortinet Exploited Again: New FortiCloud SSO Admin Authentication Bypass
CVE-2026-24858 (CVSS 9.8) is a new actively exploited flaw affecting FortiOS, FortiManager, FortiAnalyzer, FortiProxy, and FortiWeb when FortiCloud SSO is enabled. The flaw allows a FortiCloud-authenticated attacker to gain unauthorized administrative access to other tenants’ Fortinet devices. The root cause is an improper authentication flow [CWE-288] when FortiCloud SSO is used.
Early exploitation of CVE-2026-24858 was initially mistaken for a recurrence of the December 2025 FortiCloud SSO bypass vulnerabilities CVE-2025-59718 and CVE-2025-59719 (both CVSS 9.8) due to the similar attack patterns. CVE-2026-24858 has no publicly released proof-of-concept exploits, and has not been associated with ransomware attacks. However, attackers have been observed downloading full device configuration files [T1005] and creating persistent super_admin local accounts [T1136.001].
Numerous national CERT alerts have been issued globally [1][2][3][4][5][6][7][8][9][10]. The OPENVAS ENTERPRISE FEED includes detection for CVE-2026-24858 for many Fortinet products [11][12][13][14]. Updates are not yet available for all affected products. Users should seek updated guidance from Fortinet’s official advisory. According to the advisory, Fortinet has disabled FortiCloud SSO authentication from vulnerable devices to provide mitigation and posted indicators of compromise (IoC) observed in attacks.
New High-Risk CVEs in SolarWinds Web Help Desk (WHD)
Update
February 11, 2026
Microsoft security researchers have confirmed active, in-the-wild exploitation of internet-exposed SolarWinds Web Help Desk (WHD) instances and CISA has added CVE-2025-40551 to its KEV list. According to Microsoft, the observed intrusions occurred in December 2025 and resulted in unauthenticated RCE. The exact vulnerability leveraged in the attacks remains unconfirmed because affected systems were vulnerable to multiple CVEs: CVE-2025-40551, CVE-2025-40536, and the previously disclosed CVE-2025-26399.
The breaches followed a multi-stage attack chain: initial compromise via SolarWinds WHD servers, followed by lateral movement [TA0008] toward high-value assets and, in at least one case, escalation to DCSync activity [T1003.006] against a domain controller. Post-exploitation activity relied heavily on living-off-the-land (LoTL) techniques [T1218] such as legitimate administrative tooling to reduce detection.
Six new high-risk vulnerabilities affecting SolarWinds Web Help Desk (WHD) were disclosed in January 2026. WHD plays a significant role in IT service management and sensitive asset tracking globally. Previous exploitation of similar bugs indicate threat actors will target newly disclosed CVEs.
The newly disclosed CVEs affecting SolarWinds WHD are:
- CVE-2025-40551 and CVE-2025-40553 (both CVSS 9.8) Allow unauthenticated RCE on vulnerable SolarWinds Web Help Desk servers. Both flaws are due to deserialization of untrusted data [CWE-502]. CISA added CVE-2025-40551 to their KEV list on February 3rd, 2026.
- CVE-2025-40552 and CVE-2025-40554 (both CVSS 9.8): Allow remote authentication bypass [CWE-1390] leading to unauthorized access and potentially invoking protected actions.
- CVE-2025-40536 (CVSS 8.1): A security control bypass flaw [CWE-693] allows an unauthenticated attacker to gain access to restricted functionalities.
- CVE-2025-40537 (CVSS 7.5): A hardcoded credentials vulnerability [CWE-798] allows access to administrative functions.
Active exploitation has not been reported although Horizon3.ai has published the technical details for at least one potential attack chain. All versions of WHD prior to 2026.1 are impacted. Greenbone’s OPENVAS ENTERPRISE FEED includes a remote banner version check covering and separate active checks for CVE-2025-40551 and CVE-2025-40536 [1] and CVE-2025-40537 [2] for all aforementioned vulnerabilities in SolarWinds WHD. Users should identify vulnerable instances in their IT infrastructure and upgrade to WHD 2026.1 as soon as possible.
CVE-2025-59470: Critical RCE Flaw in Veeam Restoration and Backups
Four new CVEs affecting Veeam Backup & Replication version 13 builds ≤ v13.0.1.180 were published in Veeam’s January security update. All four CVEs are rated critical . They are not yet reported as actively exploited, and no public PoC exploit exists at this time. Several national CERT advisories have been issued globally [1][2][3][4][5].
The CVEs are described below:
- CVE-2025-55125 (CVSS 9.8): An attacker with the Backup or Tape Operator can achieve RCE as root by creating a malicious backup configuration file. The root cause is a command injection flaw due to improper sanitization of user supplied input [CWE-77].
- CVE-2025-59468 (CVSS 9.1): An attacker with the Backup Administrator role to perform RCE as the postgres user by sending a malicious password parameter. The root cause is a command injection flaw due to improper sanitization of user supplied input [CWE-77].
- CVE-2025-59469 (CVSS 9.0): An attacker with the Backup or Tape Operator role can write files as root. Although classified as an exposure of a sensitive information flaw [CWE-200] by NIST, it actually allows privileged file write operations, potentially leading to full system takeover.
- CVE-2025-59470 (CVSS 9.0): Authorized attackers can achieve RCE as the server’s postgres user. The root cause is a command injection flaw due to improper sanitization of user supplied input [CWE-77].
Veeam indicates that it serves 82% of Fortune 500 companies. As such, Veeam Backup & Replication is a high-value target for ransomware operators and has a documented history of exploitation by ransomware groups [7][8][9]. While exploitation requires Backup Operator or Tape Operator roles, these accounts are typically compromised via credential theft [TA0006] or by creating new privileged accounts [T1136] once an attacker gains admin-level control of the environment [6]. The OPENVAS ENTERPRISE FEED includes remote banner detection for all four new CVEs affecting Veeam Backup & Replication.
New Wireshark CVEs Can Trigger Denial-of-Service (DoS)
Multiple vulnerabilities affecting Wireshark’s protocol dissection logic can result in denial-of-service (DoS). The flaws affect various versions of Wireshark between 4.4.0 and 4.6.2. The new CVEs can be triggered by malformed network traffic.
- CVE-2026-0959 (CVSS 6.5): IEEE 802.11 protocol dissector can crash in Wireshark 4.6.0 to 4.6.2 and 4.4.0 to 4.4.12 allowing DoS.
- CVE-2026-0960 (CVSS 5.5): HTTP3 protocol dissector can enter an infinite loop in Wireshark 4.6.0 to 4.6.2 allowing DoS.
- CVE-2026-0961 (CVSS 6.5): A BLF file parser can crash in Wireshark 4.6.0 to 4.6.2 and 4.4.0 to 4.4.12 allowing DoS.
- CVE-2026-0962 (CVSS 6.5)): The SOME/IP-SD protocol dissector can crash in Wireshark 4.6.0 to 4.6.2 and 4.4.0 to 4.4.12 allowing DoS.
Because tshark shares the same libwireshark dissection engine, these flaws also affect headless and CLI-based workflows, meaning automated processing of untrusted PCAP files or live captures can trigger DoS conditions. The Greenbone ENTERPRISE FEED includes local security checks for Windows, Linux, and macOS environments. Extended information can be found from the vendor’s advisory.
Summary
January 2026 makes it clear that exploiting software vulnerabilities remains a dominant and persistent cyber security risk for virtually all organizations globally. This month included multiple critical and actively exploited flaws affecting widely deployed enterprise software. Network management systems, collaboration tools, backup software, and security appliances remain prime targets for threat actors. Unauthenticated or low-privilege RCE can have severe downstream impacts such as ransomware or data theft resulting in fraud. Organizations should scan widely and scan often to maintain complete visibility of emerging threats within their infrastructure. Defenders seeking to detect and protect can try Greenbone’s flagship OPENVAS BASIC for free, including a two-week free trial of the OPENVAS ENTERPRISE FEED.
Joseph has had a varied and passionate background in IT and cyber security since the late 1980s. His early technical experience included working on an IBM PS/2, assembling PCs and programming in C++.
He also pursued academic studies in computer and systems engineering, anthropology and an MBA in technology forecasting.
Joseph has worked in data analytics, software development and, in particular, enterprise IT security. He specialises in vulnerability management, encryption and penetration testing.




