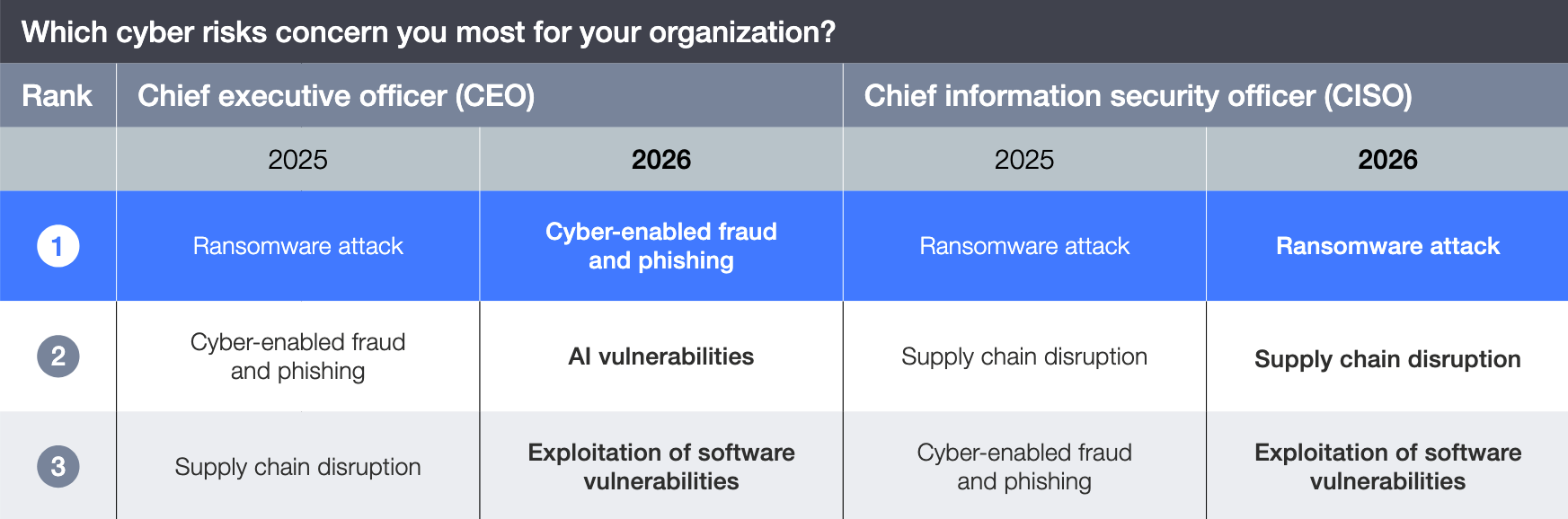
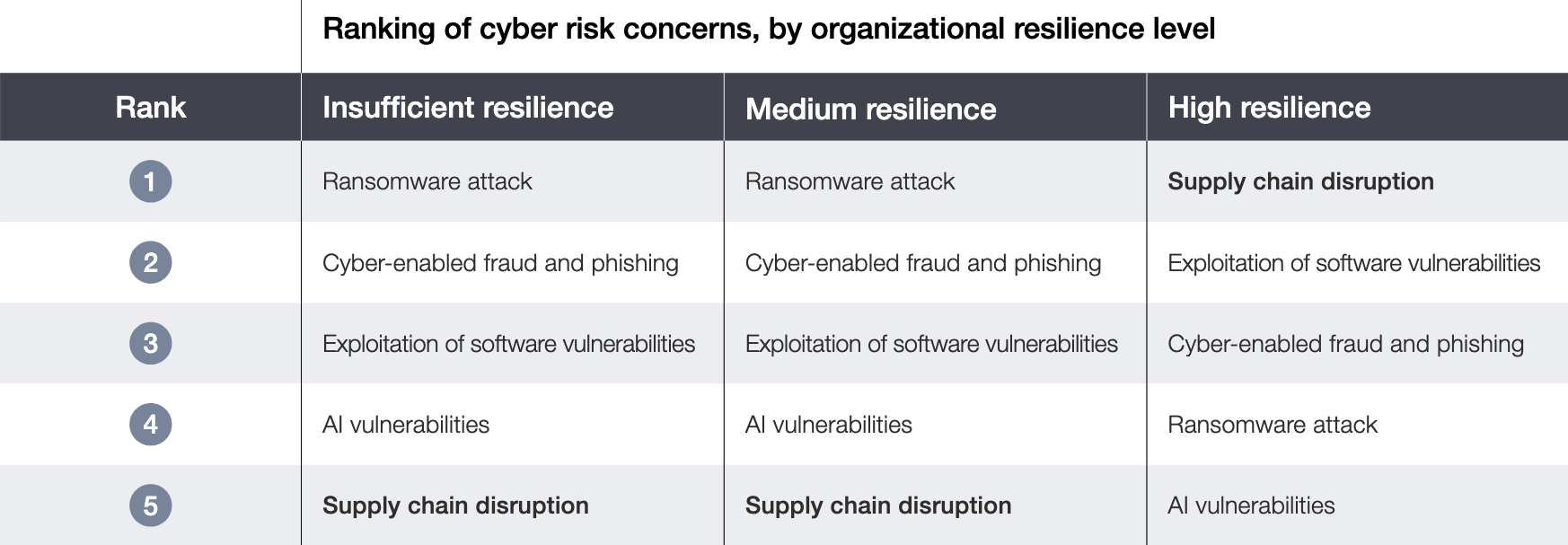
So far, 2026 is off to a raucous start. With so much activity in the software vulnerability landscape it’s easy to understand the concerns of global executives discussed in Part 1 of the January 2026 Threat Report. This volatility also highlights the value of Greenbone’s industry-leading detection coverage. In Part 2 of the January Threat report we cover more critical vulnerabilities exposed in the first month of 2026.
Defenders need to scan widely and scan often to detect new threats in their infrastructure and prioritize mitigation efforts based on the potential impact to business operations, privacy regulations, and other compliance responsibilities. Defenders seeking to detect and protect can try Greenbone’s flagship OPENVAS BASIC for free, including a two-week free trial of the OPENVAS ENTERPRISE FEED.
CVE-2025-69258: TrendMicro Apex Central Allows Unauthenticated RCE as SYSTEM
CVE-2025-69258 (CVSS 9.8) affecting Trend Micro Apex Central on-premises for Windows can allow unauthenticated RCE with SYSTEM-level privileges. Two additional CVEs, CVE-2025-69259 and CVE-2025-69260 (both CVSS 7.5) published at the same time allow denial of service (DoS) conditions. The root cause of CVE-2025-69258 is a buffer overflow [CWE-120] due to unsafe LoadLibraryEx usage and improper message handling. The bug leads to DLL injection, NULL handling flaws, and out-of-bounds reads.
Apex Central is a centralized management system for administering and monitoring Trend Micro security products across an organization, making it a prime target for attackers. On-premises Windows builds below 7190 are vulnerable. Apex Central does not include an automatic update mechanism for itself; administrators must manually install patches and upgrades. The vendor’s security advisory describes prerequisite software (such as Service Packs) that may need to be installed before the Critical Patch Build 7190 can be installed.
The CVEs are not confirmed as actively exploited, but full technical details and proof-of-concept exploits have been published for all three CVEs, significantly increasing their risk. Greenbone’s OPENVAS ENTERPRISE FEED includes a local registry check to detect all aforementioned CVEs.
Two New Actively Exploited Ivanti EPMM Flaws
Update
February 11, 2026
Active exploitation of CVE-2026-1281 and CVE-2026-1340 has resulted in confirmed government breaches across Europe. The Dutch Data Protection Authority and the Council for the Judiciary disclosed compromises, and the European Commission’s central mobile infrastructure was compromised [1][2][3][4]. Shadowserver has identified at least 86 compromised EPMM instances based on exploitation artifacts and many vulnerable instances remain online. Researchers assess that multiple threat actors are involved.
Numerous national cyber agencies have issued alerts for the CVEs and for their ongoing exploitation [1][2][3][4][5][6][7][8][9][10][11]. Ivanti has faced sustained scrutiny over its product security record, with CISA compiling more than 30 Ivanti vulnerabilities to its KEV list, many covered on our blog. Greenbone includes numerous vulnerability tests addressing Ivanti security flaws, allowing users to identify known vulnerabilities and secure their IT infrastructure.
Two new flaws affecting Ivanti Endpoint Manager Mobile (EPMM), CVE-2026-1281 and CVE-2026-1340 (both CVSS 9.8) were published on January 29th, 2026, and CVE-2026-1281 was immediately added to CISA’s KEV list that same day. Both CVEs allow unauthenticated RCE via code injection due to improper control of generated code [CWE-94]. Both are caused by pre-authenticated Apache RewriteMap integrations that pass attacker-controlled HTTP parameters into a Bash script that allows command substitution and remote shell command execution.
Once an EPMM device has been compromised, attackers may deploy backdoors [TA0011], seek lateral movement [TA0008] within the victim’s network or steal sensitive information [T1005] stored on the EPMM appliance. This may include administrator credentials [TA0006] and mobile device data including GPS location [T1430] and IMEI values [T1426]. Exploitation also allows configuration tampering [T1562] via the API or web console [T1102].
A detailed technical analysis has been released by watchTowr Labs, but push-button exploit kits are not publicly available. Furthermore, exploitation has not yet been linked to ransomware operations. Greenbone’s OPENVAS ENTERPRISE FEED includes a remote banner version check to identify affected instances. Both vulnerabilities affect on-prem instances of Ivanti EPMM. See Ivanti’s official advisory and analysis guidance for more specific information about affected versions, steps for installing the patches, and known indicators of compromise (IoC). Ivanti advises that simply installing the patch is not sufficient mitigation. Users should also hunt for IoC and initiate incident response processes followed by a full system rebuild if found.
CVE-2025-34026: Versa Concerto Actively Exploited
CVE-2025-34026 (CVSS 7.6, EPSS ≥ 98th pctl), published on May 21st, 2025, was added to CISA’s KEV list on January 22nd, 2026. The flaw allows authentication bypass leading to access to administrative endpoints in the Versa Concerto SD-WAN orchestration platform. The root cause is improper request handling in the exposed Traefik reverse proxy and Spring Boot Actuator endpoint. Exploitation enables access to heap dumps and trace logs that may contain plaintext credentials and session tokens.
Other Concerto vulnerabilities, CVE-2025-34027 (CVSS 10, EPSS ≥ 87th pctl) and CVE-2025-34025 (CVSS 8.6) can also lead to full system compromise, but reports of their active exploitation have not emerged. Both additional CVEs were also published on May 21st, 2025. Although a full technical analysis is available, public PoC exploits are not.
The OPENVAS ENTERPRISE FEED has included an active check for CVE-2025-34026 and another for CVE-2025-34027 since May 2025, giving defenders early notice to take defensive measures. These checks send specially crafted HTTP requests to identify vulnerable instances. The flaw was patched in Concerto version 12.2.1 GA released on April 16, 2025. Users should apply updates with urgency.
Ni8Mare and Steady Stream of Critical n8n CVEs Since Late 2025
Update
February 5, 2026
A new critical severity flaw affecting n8n was uncovered in early February 2026. CVE-2026-25049 (CVSS 9.9, EPSS ≥ 7th pctl) allows an authenticated user with permissions to create or modify workflows to exploit crafted expressions in workflow parameters. The vulnerability is due to improper control of dynamically-managed code resources [CWE-913]. Exploitation could trigger malicious command execution on the host. n8n versions prior to 1.123.17 and 2.5.2 are affected.
Several technical descriptions and PoC exploits are available for CVE-2026-25049 [1][2][3] increasing the risk of malicious exploitation and several national CERT alerts have been issued [4][5][6][7]. Greenbone’s OPENVAS ENTERPRISE FEED includes remote banner detection for CVE-2026-25049. The issue is patched in versions 1.123.17 and 2.5.2. Users should update to a patched version as soon as possible. More information is available from the vendor’s security advisory.
CVE-2026-21858 (aka Ni8Mare, CVSS 10, EPSS ≥ 90th pctl) is the most critical among a steady stream of critical n8n vulnerabilities that have surfaced since late 2025 affecting versions 1.x for both self-hosted and n8 Cloud instances. CVE-2026-21858 can be triggered remotely without authentication and allows full workflow-automation platform takeover. Multiple technical analyses are available for CVE-2026-21858 [1][2].
n8n is an open-source, fair-code workflow automation platform that enables users to visually connect applications, APIs, and services into automated processes. n8n’s workflow repository includes over 7,800 published workflows indicating the application is widely used.
Other critical and high-severity flaws disclosed in n8n versions 0.x and 1.x since late 2025 include:
- CVE-2026-21877 (CVSS 9.9, EPSS ≥ 94th pctl): An authenticated attacker may upload a malicious file type [CWE-434] to the n8n instance that allows RCE, potentially resulting in full system compromise. Administrators can reduce exposure by disabling the Git node and limiting access for untrusted users, but upgrading is recommended. This issue is fixed in version 1.121.3 and more information is available from the vendor’s security advisory.
- CVE-2025-68668 (CVSS 9.9, EPSS ≥ 13th pctl): A sandbox bypass vulnerability [CWE-693] in the Python Code node that uses Pyodide. An authenticated user with permissions to create or modify workflows can execute arbitrary commands on the host with n8n process privileges. Workarounds include: disabling the Code node entirely, disabling Python support in the Code node, and configuring n8n to use the task runner Python sandbox. A full root-cause analysis is available for CVE-2025-68668 increasing the risk. The issue is fixed in version 2.0.0, and more information is available in the vendor’s security advisory.
- CVE-2025-68613 (CVSS 8.8, EPSS ≥ 99th pctl): An RCE flaw in the n8n workflow expression evaluation system that allows expressions supplied by authenticated users to be evaluated in an unsandboxed execution environment [CWE-913] under certain conditions. An authenticated user could achieve RCE with n8n process privileges. Multiple PoC exploits [3][4][5] and a Metasploit module are available for CVE-2025-68613 increasing the risk. This issue is fixed in versions 1.120.4, 1.121.1, and 1.122.0, and more information is available in the vendor’s security advisory.
- CVE-2025-65964 (CVSS 8.8, EPSS ≥ 5th pctl): The Add Config operation allows workflows to set arbitrary Git configuration values, including core.hooksPath, which can point to a malicious Git hook. This could allow arbitrary command execution on the n8n host during Git operations. A full technical description and exploit chain is available. Exploitation requires n8n workflow privileges using the Git node. Workarounds include excluding the Git node and avoiding cloning or interacting with untrusted repositories using the Git node. This issue is fixed in version 1.119.2 and more information is available in the vendor’s security advisory.
Multiple CERT advisories have been issued globally addressing one or more of the aforementioned CVEs [6][7][8][9][10][11][12][13][14]. Active attack campaigns leveraging these CVEs have not been disclosed. The OPENVAS ENTERPRISE FEED includes multiple remote banner version checks to detect all the aforementioned vulnerabilities [15][16][17][18][19] as well as detection for many other CVEs affecting n8n.
n8n version 2.0 was released in December 2025 and is not affected by the aforementioned CVEs. n8n versions 0.x and 1.x users should identify the most recent fully patched version and update as soon as possible.
CVE-2025-15467: Critical Flaw Affecting OpenSSL 3
CVE-2025-15467 (CVSS 9.8, EPSS ≥ 71st pctl) is the most critical among twelve new vulnerabilities affecting the widely used OpenSSL toolkit. The flaw is exploited by passing a malicious Cryptographic Message Syntax (CMS) [RFC5652] AuthEnvelopedData message [RFC5083] using an Authenticated Encryption with Associated Data (AEAD) cipher (e.g., AES-GCM) to inject an oversized ASN.1-encoded initialization vector (IV). OpenSSL copies the oversized IV into a fixed-size stack buffer without length checks [CWE-787]. The result is a pre-authentication stack overflow that allows arbitrary RCE and DoS.
CVE-2025-15467 does not affect day-to-day SSL/TLS operations since TLS uses the X.509 certificate standard [RFC5280]. However, email clients or plugins that support S/MIME AuthEnvelopedData from untrusted inbound mail are one example of a potential attack chain. A full technical description is available for CVE-2025-15467 increasing the risk of exploit kit development. Multiple national CERT alerts have been issued globally for CVE-2025-15467 [1][2][3][4][5][6].
The twelve CVEs, disclosed by security researcher Stanislav Fort, were reportedly discovered via AI-based software analysis. This achievement comes at a time when other software maintainers and security researchers assert that AI-submitted bug reports (dubbed “AI-slop”) are effectively disrupting their bug tracking operations [7][8][9][10] and in some cases, AI-generated CVE reports are not valid bugs to begin with.
The OPENVAS ENTERPRISE FEED includes multiple detection tests for various Linux distros and Windows installations of OpenSSL for CVE-2025-15467 and eleven other recently disclosed CVEs. All twelve of the CVEs affect OpenSSL versions 3.0, 3.3, 3.4, 3.5, and 3.6.0 (released on October 1, 2025) and are fixed in versions 3.0.19, 3.3.6, 3.4.4, 3.5.5, and 3.6.1.
Hypervisor Risk Remains Elevated in Early 2026
2025’s final threat report described a reported increase in cyber attacks targeting hypervisor platforms in late 2025. This trend is poised to continue into 2026. In January, several high-risk vulnerabilities were published for popular virtualization platforms. Due to the critical role of hypervisors in securely isolating critical workloads in enterprise network infrastructure, patches should be considered a top priority.
CVE-2024-37079: Active Campaigns Targeting VMware Hypervisors
In the December 2025 Threat Report, we discussed a new intelligence report from Huntress describing a sharp spike in cyber attacks against hypervisors. The attacks targeted VMWare ESXi, Workstation, and Fusion, leveraging CVE-2025-22224 (CVSS 8.2), CVE-2025-22225 (CVSS 8.2), and CVE-2025-22226 (CVSS 6.0) by executing code as the VMX process, escaping the VMX sandbox, and leaking memory from the VMX process, respectively. Greenbone includes a variety of checks for detecting these actively exploited CVEs [1][2][3][4].
In January 2026, CVE-2024-37079 (CVSS 9.8), affecting VMware vCenter Server versions 7 and 8, was added to CISA’s KEV list. The vulnerability, published in mid-2024, allows an unauthenticated attacker to achieve RCE by exploiting a heap-overflow vulnerability to trigger an out-of-bounds memory write [CWE-787]. CVE-2024-37080 (CVSS 9.8) was published at the same time, but has not been observed in active attacks. Both CVEs are flaws in vCenter’s DCERPC (Distributed Computing Environment Remote Procedure Call) protocol implementation. DCERPC is a key technology for remote control of adjacent remote systems.
Oracle Fixes 11 High Severity VirtualBox Flaws in 2026’s First Patch Release
Oracle’s January 2026 security patch release included eleven high-severity CVEs affecting VirtualBox versions 7.1.14 (released October 10th, 2025) and version 7.2.4 (released October 21, 2025). Most of the vulnerabilities require local access. The high-severity disclosures include:
- CVE-2026-21955 (CVSS 8.2): a high-severity vulnerability found in the core component of Oracle VirtualBox. The flaw allows a privileged, local attacker to compromise the virtualization software, with potential for full VirtualBox system takeover and unauthorized access to critical data.
- CVE-2026-21956 (CVSS 8.2): a flaw in the core component of Oracle VirtualBox that allows a privileged attacker with logon privileges to compromise the integrity of VirtualBox and significantly impact additional products.
The new batch of VirtualBox flaws are not considered actively exploited and no public PoC exploits are available. Multiple national CERT advisories have been issued globally for Oracle’s latest security update [1][2][3][4][5]. Greenbone’s OPENVAS ENTERPRISE FEED detects all newly disclosed VirtualBox flaws across Windows, Linux, and macOS environments [5][6][7]. Users should update their VirtualBox instance to a patched version as soon as possible.
Other Notable High-Risk CVEs From January 2026
Here is a quick snapshot of other high-risk CVEs published in January 2026:
- BIND9 Denial of Service (CVE-2025-13878, CVSS 7.5): Allows unauthenticated remote attackers to cause DoS in ISC BIND 9. There are no reports of active exploitation or public PoC exploits. The issue impacts both authoritative servers and resolvers, and is fixed in BIND 9.18.44, 9.20.18, and 9.21.17 [1]. The OPENVAS ENTERPRISE FEED provides package-level detection across a wide array of Linux distributions and a remote banner check for Windows.
- Critical-Severity GitLab Vulnerability Plus More (CVE-2025-13761, CVSS 9.6): GitLab has released security updates7.1, 18.6.3, and 18.5.5 to patch multiple vulnerabilities in self-managed instances. The update cycle included critical-severity stored and reflected XSS that could enable arbitrary JavaScript execution in users’ browsers. Collectively the issues could impact integrity, confidentiality, and availability across most deployment types. Administrators should upgrade immediately and pay close attention to GitLab’s fast moving patch cycle. The OPENVAS ENTERPRISE FEED includes detection for all CVEs in the batch.
- Multiple Critical CVEs Affecting CoolLabs Coolify: Eleven new vulnerabilities affecting CoolLabs Coolify were released as a group in early January, 2026. Coolify is an open-source and self-hostable tool for managing servers, applications, and databases. The project’s GitHub repository shows ~50.5k stars, ~3.6k forks, and 575 contributors, signaling an active presence. More details are available on the product’s GitHub security page. The OPENVAS ENTERPRISE FEED provides detection for all eleven CVEs in the release.
- Unauthenticated RCE in telnetd (CVE-2026-24061, CVSS 9.8): The telnet remote access application has been considered a critical security risk for decades. It does not provide encryption for data in transit, making adversary-in-the-middle (AiTM) attacks [T1157] trivial. However, CVE-2026-24061 uncovers an even more severe risk that goes back to version 1.9.3, released May 2015. CVE-2026-24061 is an authentication bypass in GNU InetUtils telnetd, allowing attackers without credentials to gain root user access remotely. Multiple descriptions [1][2] and PoC are available [3][4][5] and numerous CERT advisories have been issued globally [6][7][8][9][10]. For users who require legacy support from the telnet service, patches have been issued. Otherwise users should ensure the service is uninstalled since it can also be exploited locally for privilege escalation. The OPENVAS ENTERPRISE FEED provides a set of package version checks for Linux and an active check effective for all operating systems [11].
Summary
With so much activity in the software vulnerability landscape, it’s easy to understand the concerns of global executives discussed in Part 1 of the January 2026 Threat Report. This volatility also highlights the value of Greenbone’s industry-leading detection coverage. January 2026 was so hectic, it deserved two threat reports. In Part 2 of the January 2026 Threat Report we reviewed another cluster of emerging high-risk software vulnerabilities. Defenders seeking to detect and protect can try Greenbone’s flagship OPENVAS BASIC for free, including a two-week free trial of the OPENVAS ENTERPRISE FEED.