Greenbone’s vulnerability management finds applications with Log4j vulnerabilities in systems that definitely need to be patched or otherwise protected. Depending on the type of systems and vulnerability, these can be found better or worse. Detection is also constantly improving and being updated. New breaches are found. Therefore, there may always be more systems with Log4Shell vulnerabilities in the network. For this reason, it is worthwhile to regularly update and scan all systems. The Greenbone vulnerability management offers appropriate automation functions for this purpose. But how are vulnerabilities found, and where can they be hidden? Why are vulnerabilities not always directly detectable? The following article will give you a brief insight into how scanning for vulnerabilities like Log4Shell works.
A vulnerability scanner makes specific queries to systems and services and can read from the responses what kind of systems and services they are, but also what products are behind them. This also includes information such as their versions or even settings and other properties. In many cases, this makes it possible to determine whether a vulnerability exists and whether it has already been eliminated. In practice, these are sometimes highly complicated and nested queries, but above all they are also very, very many. Entire networks are scanned for thousands of different vulnerabilities.
The Log4j vulnerability “Log4Shell” (CVE-2021-44228) is a flawed program library used in many web services products. Therefore, partly it is directly visible through a vulnerability scan, but partly it is hidden behind other elements. That is why there is not only one vulnerability test for Log4j, but several. More are added all the time because the manufacturers of the respective products share relevant information and also provide updates to close the gaps. The list of systems affected by Log4Shell is constantly updated at https://gist.github.com/SwitHak/b66db3a06c2955a9cb71a8718970c592.
Some of the vulnerability tests require an authenticated scan. This means that the scanner must first log into a system and then detect the vulnerability in the system. An authenticated scan can provide more details about vulnerabilities on the scanned system.
The vulnerability tests that are suitable to find the Log4j vulnerability are provided collectively in a scan configuration. Greenbone keeps this “Log4j” scan configuration continuously up-to-date in order to keep adding new tests. As a result, a scan may report a Log4j vulnerability tomorrow that was not found today. It is therefore advisable to configure the Log4j scan to run automatically on a regular basis. This is especially important in the next weeks, when many software vendors are gathering more findings. Greenbone continuously integrates these findings into the tests and the scan configuration.
Does a Vulnerability Have to Be Exploited to Find It?
Exploiting a vulnerability to find it is not advisable. And fortunately, it is not necessary either. Doing so could cause the very damage that should be avoided at all costs. Moreover, a product vendor that provides vulnerability exploitation as a feature would potentially strongly encourage misuse of that feature, which raises further – not only legal – issues. Therefore, Greenbone’s vulnerability management does not include such features.
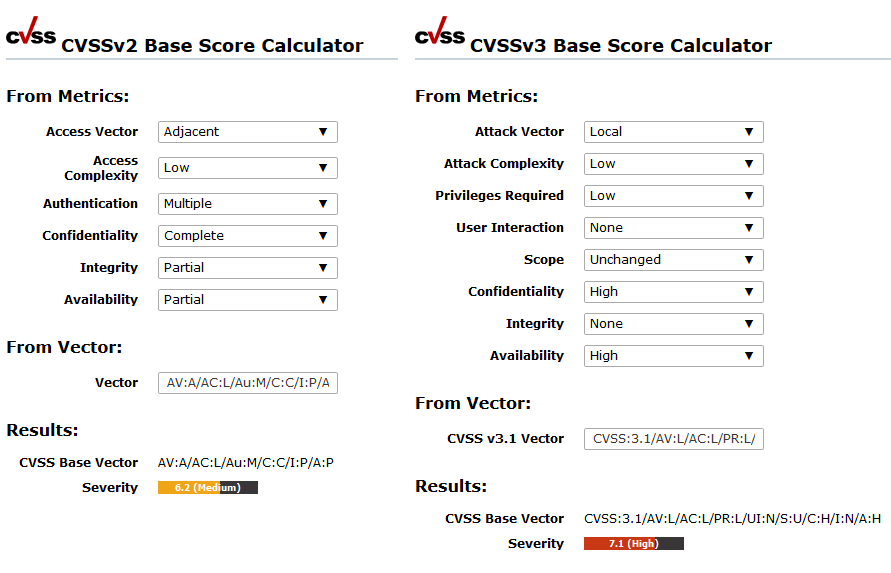
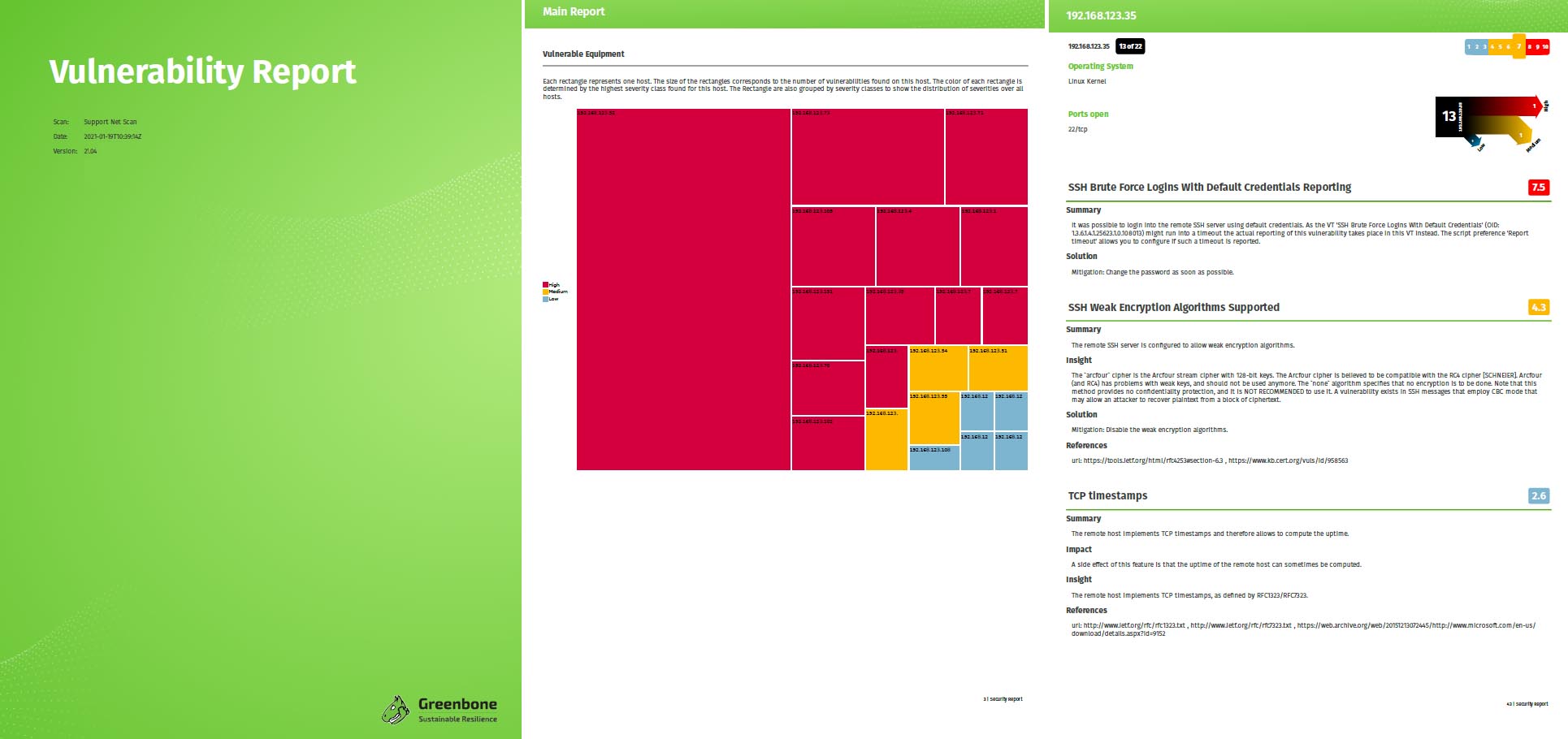
Exploitation of the Log4j vulnerability as attackers would do is also not required to prove the existence of the vulnerability. Greenbone has developed several tests to prove Log4Shell, each of which looks at systems in different depths. Several tests can detect the Log4j vulnerability with 100 % certainty, most with 80 % to 97 % certainty. Some tests also collect indicators of 30 % where they do not get close enough to the vulnerability. Each test at Greenbone makes a statement about detection certainty, which is stated as “Quality of Detection.”
What Is the Role of Software Product Vendors?
Manufacturers of a wide variety of products can use Log4j libraries, which are now vulnerable with it. Product manufacturers have included Log4j in different ways. Usually, a deep scan can find Log4j without the vendor’s help. However, most manufacturers also support the process through public vulnerability reports. These can then be used to write vulnerability tests that can provide a reliable vulnerability statement even with less deep scans. The reason for this is that the scans can use simpler configurations through vendor information. In addition, they also run faster.
In principle, however, a vulnerability scanner can also check and find vulnerabilities without the manufacturer publishing a vulnerability report.
Conclusion
Vulnerability management is an indispensable part of IT security. It can find risks and provides valuable information on how to fix them. However, no single measure provides 100 % security, not even vulnerability management. To make a system secure, many elements are used, which in their entirety should provide the best possible security.
This is comparable to a vehicle, where the passenger compartment, seat belts, airbags, brake support, assistance systems and much more increase safety, but can never guarantee it. Vulnerability management makes risks controllable.



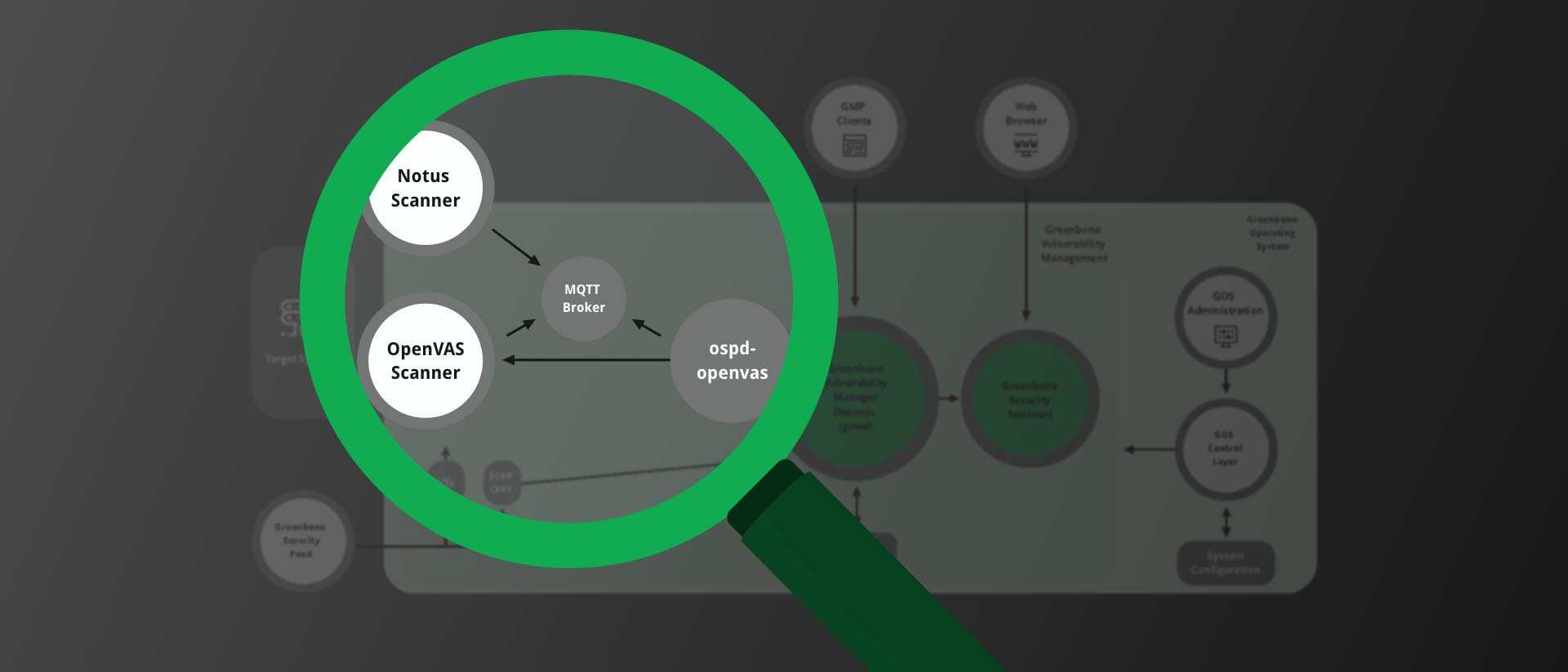

 Since 2021-04-30, the latest GOS version – version 21.04 – is available and, as always, it brings a lot of new features and improvements! What exactly? Get an overview of all important changes with GOS 21.04 here!
Since 2021-04-30, the latest GOS version – version 21.04 – is available and, as always, it brings a lot of new features and improvements! What exactly? Get an overview of all important changes with GOS 21.04 here!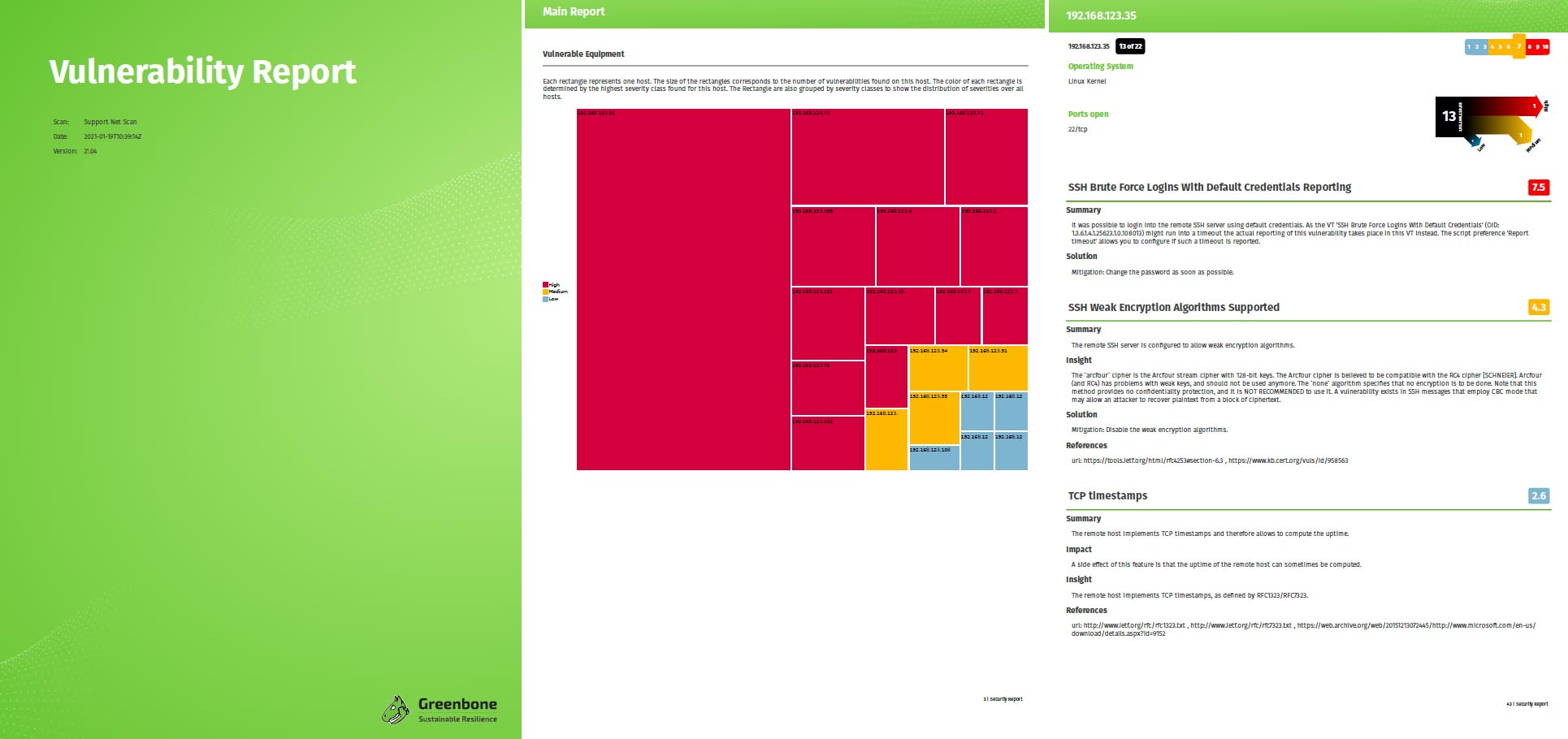





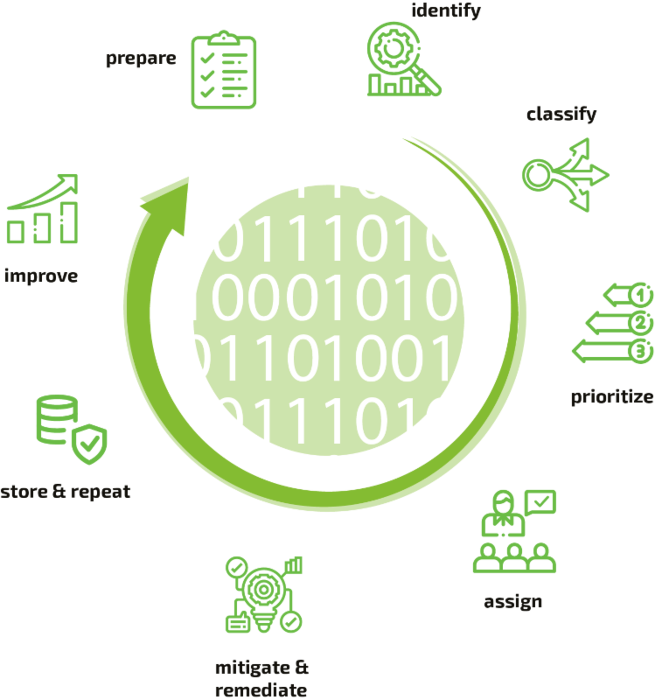 Why Cyber Resilience Is Particularly Important for Critical Infrastructures Sustainable cyber resilience is important for companies in all industries. But it is indispensable in the area of critical infrastructure (CRITIS). As defined by the German government, this includes “organizations or facilities of critical importance to the state community, the failure or impairment of which would result in sustained supply shortages, significant disruptions to public safety, or other dramatic consequences.” CRITIS organizations must therefore protect themselves particularly well against cyber attacks – this is required by law. The EU launched the European Programme for Critical Infrastructure Protection (EPCIP) back in 2006 and expanded and supplemented it in subsequent years. Member states are implementing the EU NIS directive in national law, Germany for instance with the IT Security Act (IT-SIG). Large economic nations have already developed regulatory bodies. In the U.S., for example, this is the National Institute of Standards and Technology (NIST) and in Germany the Federal Office for Information Security (BSI). In Germany, the critical infrastructures are divided into 9 sectors. One of these is the water sector with the divisions of public water supply and wastewater disposal. It includes, for example, waterworks, pumping stations, water pipelines and networks, wastewater treatment plants, the sewerage system, and dam and flood protection facilities. They all play a critical role in our society. Attacks on the water supply could therefore hit a society to the core and, in the worst case, threaten human lives. Attacks on the wastewater disposal system are just as dangerous. If it no longer functions, the result would be considerable hygienic and health problems. Since the water infrastructure uses many IT systems and electronic control systems (ICS) nowadays, it becomes an attractive target for hackers. Incidents Show the Vulnerability of the Water Sector In recent years, there have been numerous attacks on water infrastructures worldwide. Fortunately, there have been no serious consequences so far. However, the attacks show that hackers are exploring how to take control of control systems and prepare further attacks. In 2013, for example, Iranian hackers attempted to penetrate the
Why Cyber Resilience Is Particularly Important for Critical Infrastructures Sustainable cyber resilience is important for companies in all industries. But it is indispensable in the area of critical infrastructure (CRITIS). As defined by the German government, this includes “organizations or facilities of critical importance to the state community, the failure or impairment of which would result in sustained supply shortages, significant disruptions to public safety, or other dramatic consequences.” CRITIS organizations must therefore protect themselves particularly well against cyber attacks – this is required by law. The EU launched the European Programme for Critical Infrastructure Protection (EPCIP) back in 2006 and expanded and supplemented it in subsequent years. Member states are implementing the EU NIS directive in national law, Germany for instance with the IT Security Act (IT-SIG). Large economic nations have already developed regulatory bodies. In the U.S., for example, this is the National Institute of Standards and Technology (NIST) and in Germany the Federal Office for Information Security (BSI). In Germany, the critical infrastructures are divided into 9 sectors. One of these is the water sector with the divisions of public water supply and wastewater disposal. It includes, for example, waterworks, pumping stations, water pipelines and networks, wastewater treatment plants, the sewerage system, and dam and flood protection facilities. They all play a critical role in our society. Attacks on the water supply could therefore hit a society to the core and, in the worst case, threaten human lives. Attacks on the wastewater disposal system are just as dangerous. If it no longer functions, the result would be considerable hygienic and health problems. Since the water infrastructure uses many IT systems and electronic control systems (ICS) nowadays, it becomes an attractive target for hackers. Incidents Show the Vulnerability of the Water Sector In recent years, there have been numerous attacks on water infrastructures worldwide. Fortunately, there have been no serious consequences so far. However, the attacks show that hackers are exploring how to take control of control systems and prepare further attacks. In 2013, for example, Iranian hackers attempted to penetrate the 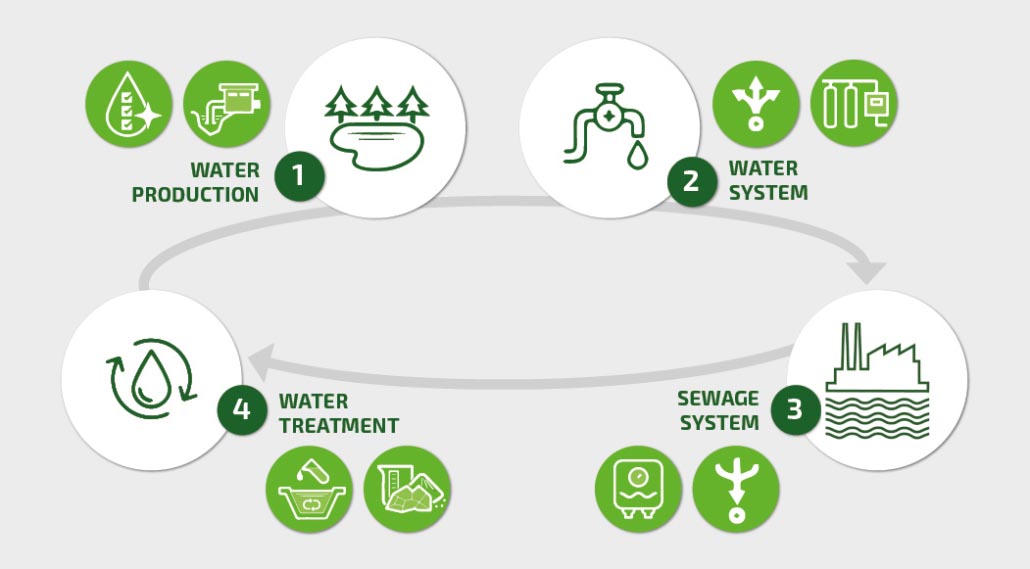 Many networked IT systems and industrial control systems are therefore used in drinking water supply and wastewater disposal, enabling largely automated processes. Examples include sensors for temperature, flow rate, or chlorine content, remotely readable meters, and web portals and mobile apps for customers. Challenges for Cyber Resilience in the Water Sector To reduce their attack surface for cyber criminals, water sector organizations must consider the full range of networked systems, devices and applications. But this is not always easy. One problem is that the ICSs used in the water infrastructure come from different generations. Many of the older control systems were developed at a time when little or no consideration was given to cyber security. This leads to a heterogeneous, vulnerable IT landscape. Additionally, the high degree of automation and dependence on industrial controls makes water infrastructure particularly vulnerable to attack. Furthermore, the IT systems in use are becoming increasingly complex. This makes it difficult for companies to achieve a sufficient level of protection. The increasing networking of components within the field and control level as well as the control and process control technology increases the complexity even further. At the same time, this increases the attack surface for hackers. They have more and more opportunities to penetrate networks, steal data or manipulate industrial controls. Even Previously Unexploited Vulnerabilities Should Not Be Underestimated A recent study by Kenna Security found that the total number of vulnerabilities discovered per year has increased from 4,100 in 2011 to 17,500 in 2021. On the other hand, the percentage of vulnerabilities exploited by hackers has not grown at the same rate. What is the reason for this? Cyber crime follows the same economic rules as any other business model: least investment for maximum result. But cyber crime also suffers from the same problem as the IT industry in general: experts are a limited resource. Companies cannot change this initial situation, but they can ensure that their attack surface is reduced. Tolerating a large attack surface, even if the vulnerabilities are not yet weaponized, is replacing control with gambling. As soon as it seems cheaper for cyber criminals or the outcome is promising, cyber crime will focus on vulnerabilities that are not yet weaponized, and the conversion of vulnerabilities into weapons will happen quickly. Even worse is the motivation of cyber terrorists, who have so far been fortunately unsuccessful due to a lack of expertise. It is unclear whether they will gain the necessary skills and if so, when. But they do not follow the rules of economics, which makes them less predictable in selecting targets and suitable weaponized vulnerabilities. In essence, there are two good general reasons why organizations should establish a process to manage and minimize their entire attack surface and not just focus on current (or likely) weaponizable vulnerabilities:
Many networked IT systems and industrial control systems are therefore used in drinking water supply and wastewater disposal, enabling largely automated processes. Examples include sensors for temperature, flow rate, or chlorine content, remotely readable meters, and web portals and mobile apps for customers. Challenges for Cyber Resilience in the Water Sector To reduce their attack surface for cyber criminals, water sector organizations must consider the full range of networked systems, devices and applications. But this is not always easy. One problem is that the ICSs used in the water infrastructure come from different generations. Many of the older control systems were developed at a time when little or no consideration was given to cyber security. This leads to a heterogeneous, vulnerable IT landscape. Additionally, the high degree of automation and dependence on industrial controls makes water infrastructure particularly vulnerable to attack. Furthermore, the IT systems in use are becoming increasingly complex. This makes it difficult for companies to achieve a sufficient level of protection. The increasing networking of components within the field and control level as well as the control and process control technology increases the complexity even further. At the same time, this increases the attack surface for hackers. They have more and more opportunities to penetrate networks, steal data or manipulate industrial controls. Even Previously Unexploited Vulnerabilities Should Not Be Underestimated A recent study by Kenna Security found that the total number of vulnerabilities discovered per year has increased from 4,100 in 2011 to 17,500 in 2021. On the other hand, the percentage of vulnerabilities exploited by hackers has not grown at the same rate. What is the reason for this? Cyber crime follows the same economic rules as any other business model: least investment for maximum result. But cyber crime also suffers from the same problem as the IT industry in general: experts are a limited resource. Companies cannot change this initial situation, but they can ensure that their attack surface is reduced. Tolerating a large attack surface, even if the vulnerabilities are not yet weaponized, is replacing control with gambling. As soon as it seems cheaper for cyber criminals or the outcome is promising, cyber crime will focus on vulnerabilities that are not yet weaponized, and the conversion of vulnerabilities into weapons will happen quickly. Even worse is the motivation of cyber terrorists, who have so far been fortunately unsuccessful due to a lack of expertise. It is unclear whether they will gain the necessary skills and if so, when. But they do not follow the rules of economics, which makes them less predictable in selecting targets and suitable weaponized vulnerabilities. In essence, there are two good general reasons why organizations should establish a process to manage and minimize their entire attack surface and not just focus on current (or likely) weaponizable vulnerabilities:

