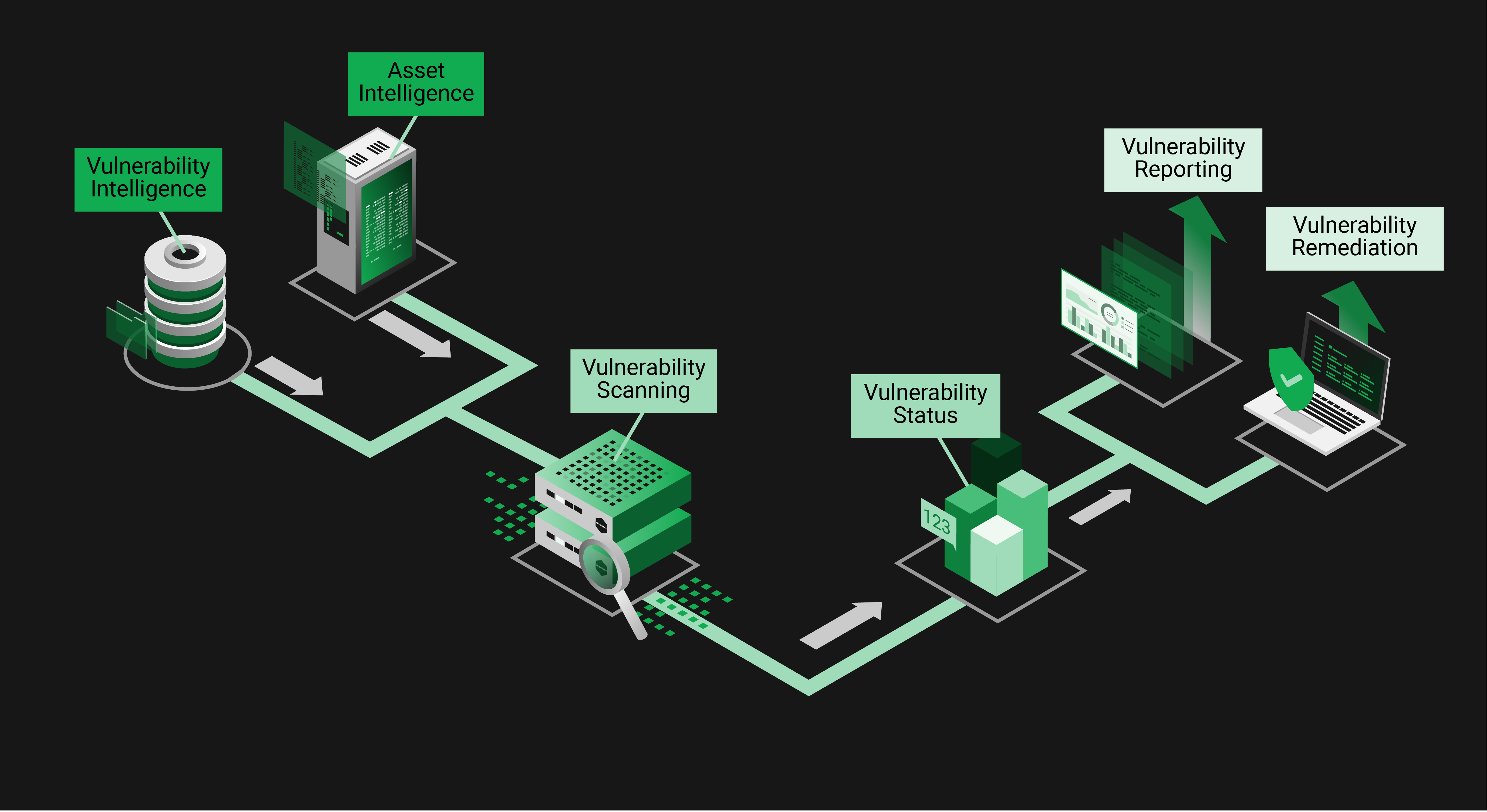
The job to protect from cyberattacks by minimizing your attack surface demands three essential pillars:
Vulnerability Intelligence
Know everything about vulnerabilities and risks immediately.
Asset Intelligence
Scan all the TCP/IP protocols, dive deep into assets and use other sources of asset details.
Vulnerability Scanning
Create, deploy, and execute vulnerability tests fast and by priority.
Vulnerability Intelligence
Vulnerability Intelligence helps doing two jobs: First you must make a priority decision about what attack vectors you should address and which ones you accept. This decision is not easy and may have a far-reaching impact. Even worse, it has to be made under time pressure and with limited resources. In other words, this decision is (sometimes) a triage. The better the information about the vulnerability the better will be the decision. And the more evidence you get, the less personal educated guess you have to add. Once you decided which attack vectors to address, technical details about the vulnerability intelligence will help as a guide for an efficient remediation. Knowing how easy or complicated a remediation is supports you already during the priority decision.
Asset Intelligence
Asset Intelligence is about knowing as much as possible about the assets that you have to protect from cyber-attacks. It may sound strange but the first part of this is to know which assets you have. Networks can be pretty dynamic because your people are very dynamic about extending and connecting services and devices. Scanning for existence of and scanning into assets is equally important. Both builds your inventory which you will later compare with the incoming vulnerability intelligence on new attack vectors. There are expected details like product versions and there are unexpected details determined only when a security advisory is published. For the first case you build a database allowing quick offline scans upon new advisories. For the latter case you need the ability to use arbitrary TCP/IP protocols to collect the information that are required to determine the presence of a vulnerability. A special case are fictive assets represented by inventories or a Software Bill of Materials, representing for example devices that are subject to the EU Cyber Resilience Act.
Vulnerability Scanning
The art of Vulnerability Scanning begins with the creation of tests, usually derived from Vulnerability Intelligence, and verified thoroughly. The growing number of security advisories makes this also a business of priority decision about which advisories to address first. Learning about the asset inventories of our customer helps us to make this job even better for them. After rapid deployment of the tests the art of vulnerability scanning finishes with a fast, powerful, and easy to deploy set of scanners. In simple words those scanners compare the vulnerability intelligence with asset intelligence to list up the current attack surface. Scanning can be as simple a comparing a version number or as complex as a multi-stage exploit via TCP/IP. In the end of the day the result is a vulnerability status with high relevance and high quality of detection, and so will be your vulnerability remediation and vulnerability reporting.