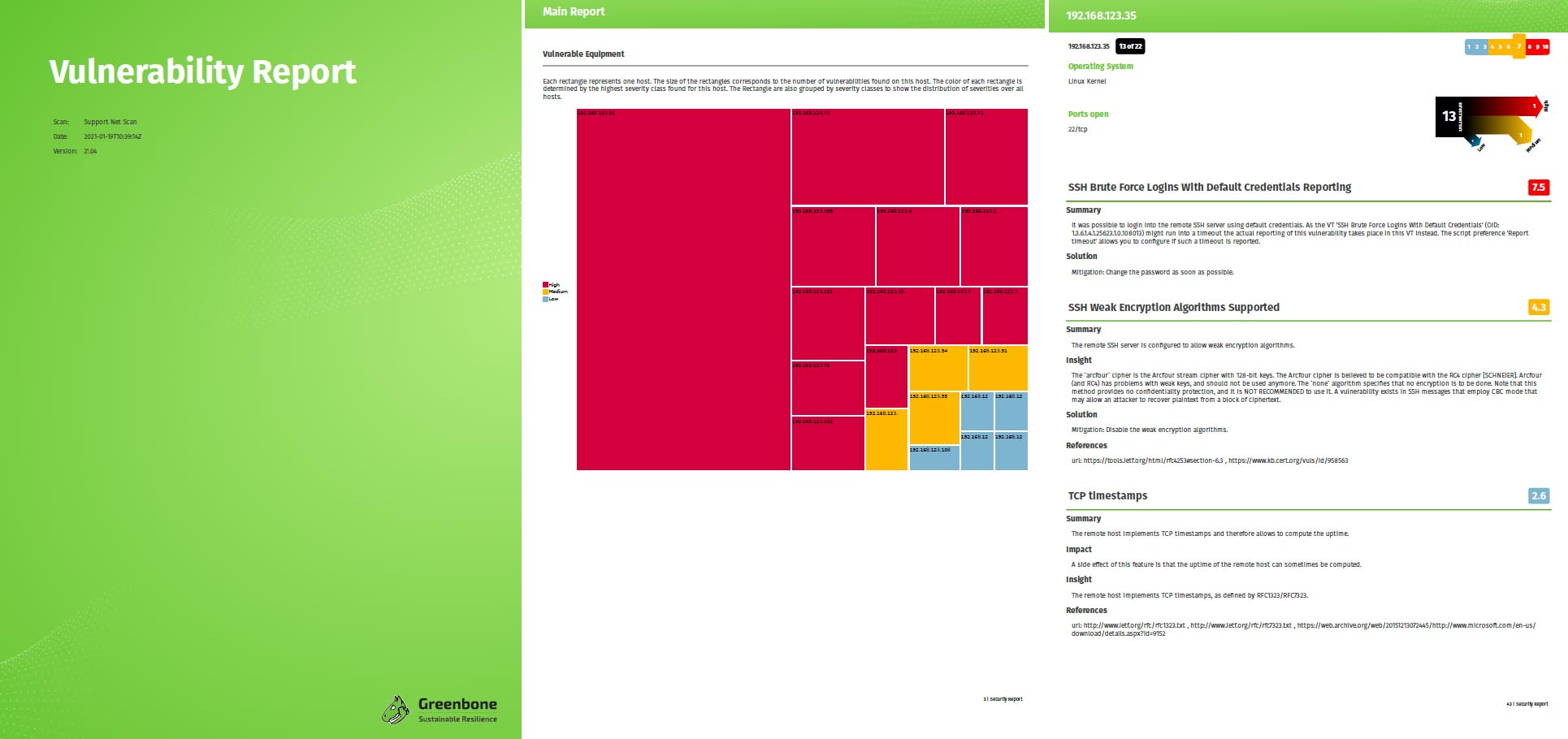
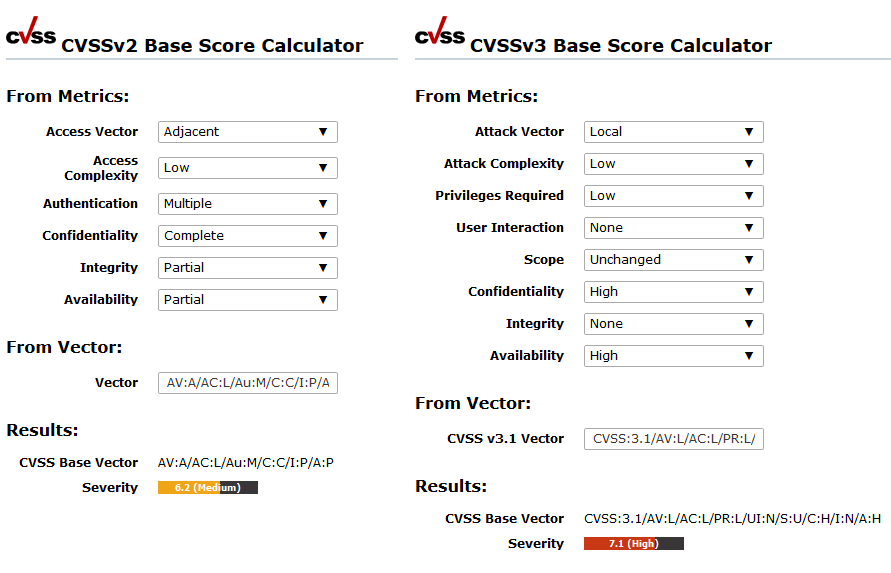
With the help of compliance policies, a company can check whether all components integrated in the system meet the required specifications. The increasing digitalization and the associated growth of new technologies create opportunities, but also risks. For this reason, the demands on compliance are increasing as well. With GOS 20.08, all compliance policies were made available via the Greenbone Security Feed and four new compliance policies were added: TLS-Map, BSI TR-03116: Part 4, Huawei Datacom Product Security Configuration Audit Guide and Windows 10 Security Hardening.

What is a compliance policy anyway?
In addition to legal requirements, companies and public authorities often have their own guidelines that must be met for the secure configuration of a system. The aim is to ensure the information security of the company or authority by guaranteeing the confidentiality, integrity, availability and authenticity of information.
All specifications and guidelines that are necessary for this are summarized in one document to form a policy.
Based on the individual criteria of the guidelines, Greenbone develops vulnerability tests – roughly speaking: one criterion results in one vulnerability test. Greenbone combines these tests into a scan configuration.
Such scan configurations, which reflect policies of companies or authorities, are called Compliance Policies.
Example: a company releases a security policy with the following requirements:
- Version 2 of software A is installed on the target system
- SSH is activated on the target system
- Software B is not installed on the target system
Greenbone develops a vulnerability test for each of the requirements, which checks whether the respective condition is fulfilled.
The three tests are then combined into a compliance policy that a user of the Greenbone solutions can choose when performing a vulnerability test. During the scan, it is checked whether the conditions mentioned above are met on the target system.
New: distribution of compliance policies via the Greenbone Security Feed
Starting with GOS 20.08, all standard scan configurations, reports formats, port lists, and compliance policies of Greenbone are distributed via the Greenbone Security Feed.
Among other things, this allows the publication and distribution of scan configurations for current, hot vulnerability tests. In the past, these were published as XML files for manual download on the Greenbone download website and had to be imported by the users themselves – which was very tedious and left room for mistakes, making a quick application hardly possible.
But this is not the only advantage. It also makes troubleshooting much easier and faster for the customer: objects can be updated and, if necessary, fixed for all setups with a single feed update.
In addition to this innovation, the Greenbone Security Feed has been extended by some important compliance policies.
More Compliance Policies in the Greenbone Security Feed
Four new compliance policies were added to the Greenbone Security Feed in the 4th quarter 2020:
- TLS-Map
- BSI TR-03116: Part 4
- Huawei Datacom Product Security Configuration Audit Guide
- Windows 10 Security Hardening
About the Special Scan Configuration TLS-Map
Note: TLS-Map is a scan configuration for special scans that are different from vulnerability scans. For reasons of simplicity, this special scan configuration is listed in this article along with the compliance policies.
The special scan configuration TLS-Map is helpful wherever secure communication over the Internet is required. TLS – short for Transport Layer Security – is a protocol for the secure transmission of data on the Internet. It is the successor of SSL – Secure Sockets Layer – which is why both protocols are still often used synonymously today. However, all SSL versions and TLS versions prior to version 1.2 have been outdated since 2020 at the latest and are therefore insecure.
The largest area of application for TLS is data transfer via the World Wide Web (WWW), for example between a web browser as the client and a server such as www.greenbone.net. Other areas of application are in e-mail traffic and in the transfer of files via File Transport Protocol (FTP).
The special scan configuration TLS-Map checks whether the required TLS version is available on the target system and whether the required encryption algorithms – so-called ciphers – are offered.
About the Compliance Policy BSI TR-03116: Part 4
The Technical Guideline BSI TR-03116 Cryptographic Requirements for Federal Projects from the Federal Office for Information Security (BSI) is used for Federal Government projects. This means that if a federal project should be implemented, this guideline must be fulfilled. It consists of 5 parts in total:
- Part 1: Telematic infrastructure
- Part 2: Sovereign identification documents
- Part 3: Intelligent measuring systems
- Part 4: Communications procedures in applications
- Part 5: Applications of the Secure Element API
The compliance policy, which Greenbone Network has developed accordingly, checks whether the contents of the fourth part of the policy are fulfilled. This part contains requirements for communication procedures.
The compliance policy BSI TR-03116: Part 4 in the Greenbone Security Feed tests the three main requirements – minimum TLS version as well as necessary and not legitimate ciphers – of the technical guideline.
About the Compliance Policy Huawei Datacom Product Security Configuration Audit Guide
Compliance policies for Huawei solutions have been part of the Greenbone Security Feed for quite some time.
Greenbone had already developed compliance policies for the following two solutions:
- EulerOS: Linux operating system, based on CentOS
Related compliance Policy: EulerOS Linux Security Configuration
- GaussDB: database management system (DBMS)
Related compliance policy: GaussDB 100 V300R001C00 Security Hardening Guide
With a compliance policy for Huawei Datacom, a product category that also includes routers and switches with their own operating system, a third compliance policy for solutions developed by Huawei is added now.
For all three products – Huawei Datacom, EulerOS and GaussDB – there are security configurations that were specified by Huawei. Based on these configurations, Greenbone has developed compliance policies which check the compliance with those security configurations. The different compliance policies are always applied if the corresponding solution is available on the target system.
For the Huawei Datacom operating system, Huawei distributes the Huawei Datacom Product Security Configuration Audit Guide. The associated, newly developed compliance policy tests, for example, whether the correct versions of SSH and SNMP are available on the target system.
About the Compliance Policy Windows 10 Security Hardening
The compliance policy Windows 10 Security Hardening includes vulnerability tests to evaluate the hardening of Windows 10 according to industry standards.
Among other things, the compliance policy checks different password specifications such as age, length and complexity of the password, specifications for the assignments of user rights, and requirements for different system devices.
Even faster integration of compliance policies with GOS 20.08
As digitalization continues, compliance requirements are growing in companies of all sizes and in all industries.
Through the direct integration of compliance policies via the Greenbone Security Feed and the inclusion of new compliance policies, the testing of target systems is even more efficient, easier and quicker, thus increasing the protection of the IT infrastructure without the need for special compliance know-how. Of course, we continue to work on new compliance policies on an ongoing basis. So be curious!






 Since 2021-04-30, the latest GOS version – version 21.04 – is available and, as always, it brings a lot of new features and improvements! What exactly? Get an overview of all important changes with GOS 21.04 here!
Since 2021-04-30, the latest GOS version – version 21.04 – is available and, as always, it brings a lot of new features and improvements! What exactly? Get an overview of all important changes with GOS 21.04 here!